策略路由(PBR)
{Back to Index}
Table of Contents
策略路由面向的对象是 数据 。
基于策略的路由比传统路由能力更强,使用更灵活,它使网络管理者不仅能够根据目的地址而且能够根据协议类型、报文大小、应用或 IP 源地址来选择转发路径。
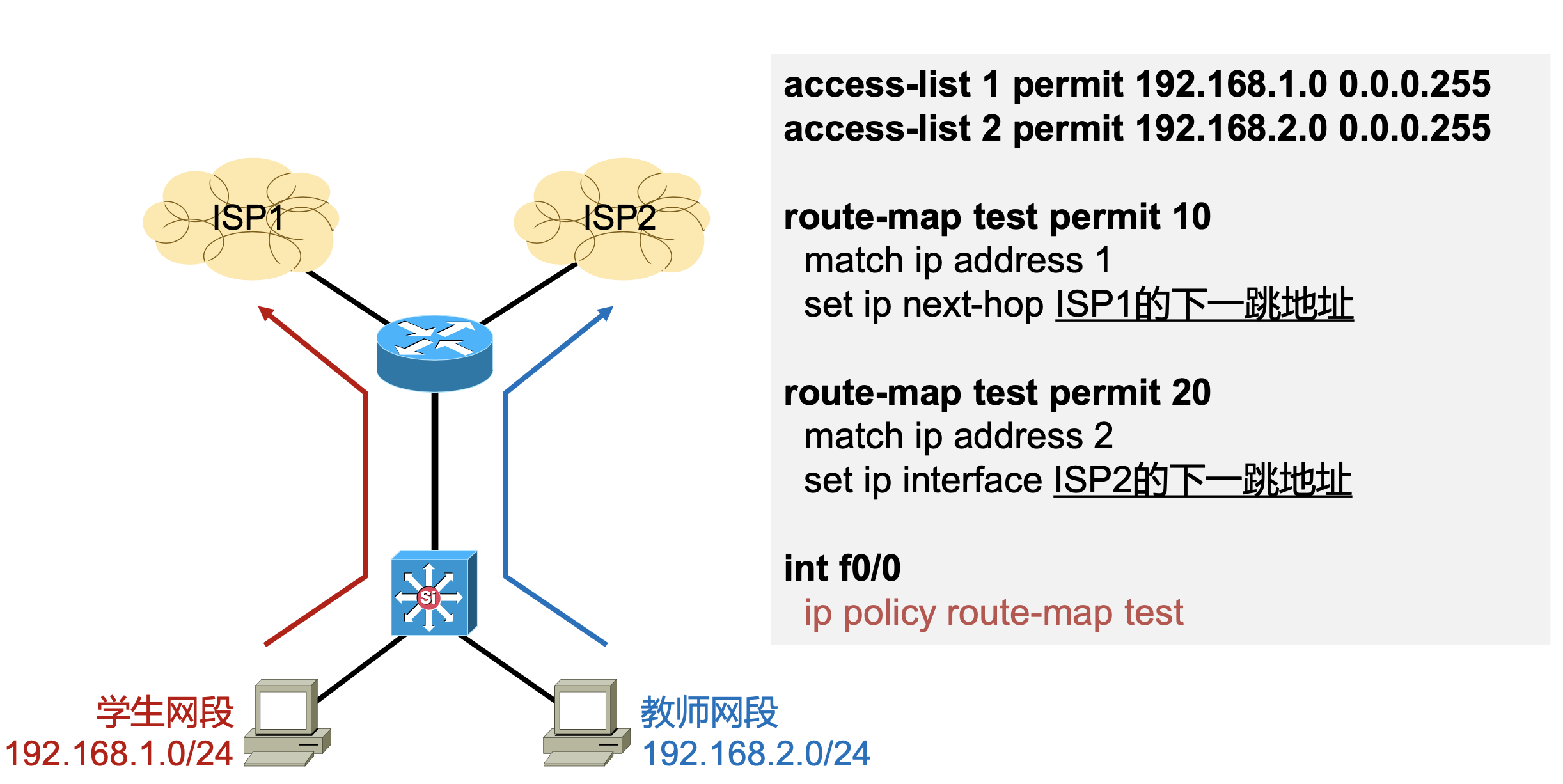
Figure 1: 经典案例
1 对数据的处理逻辑
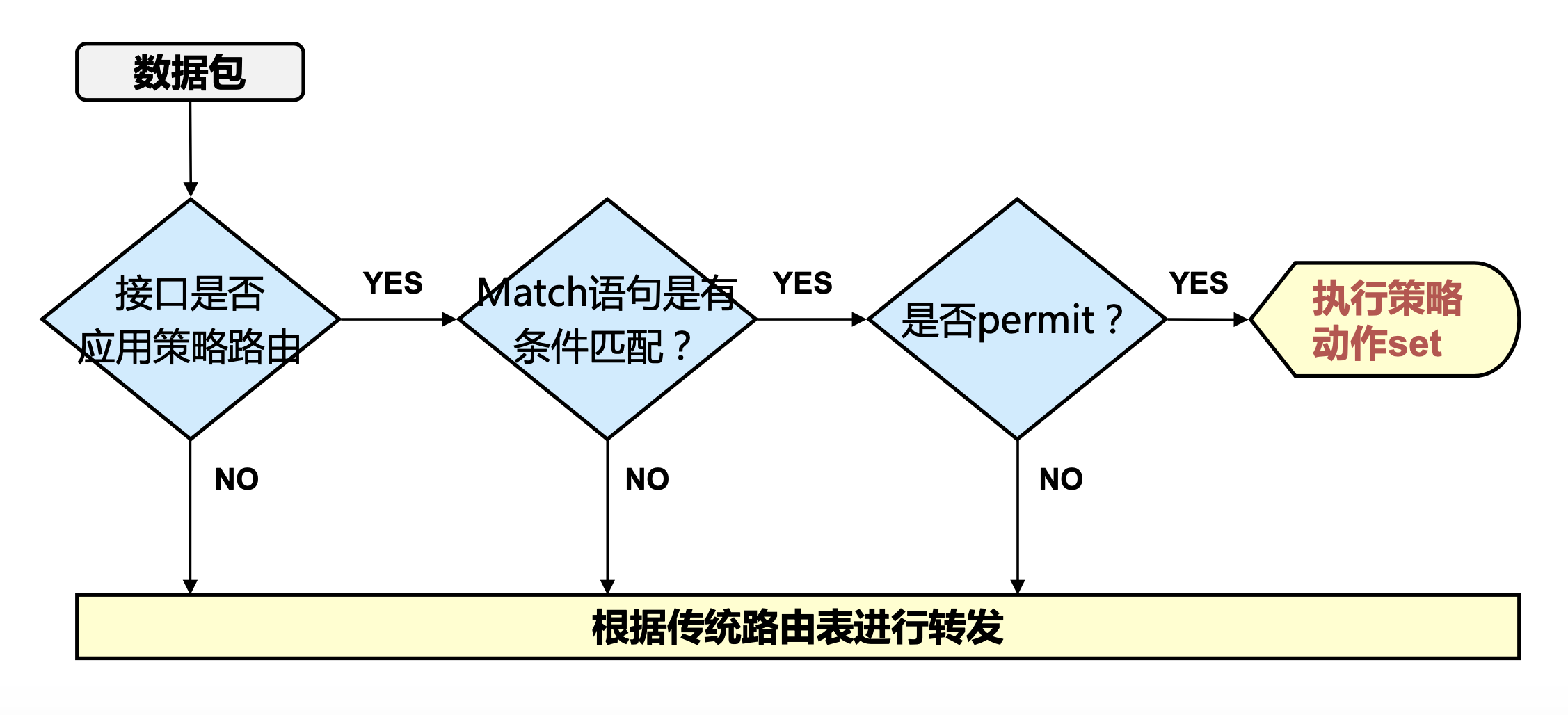
2 配置要点
2.1 ip policy
只对 进入接口 的数据流量生效,本地始发的流量无效
router(config-if)# ip policy route-map map
2.2 ip local policy
可以针对本地始发的流量生效
router(config)# ip local policy route-map map
3 使用 PBR 控制路由实验
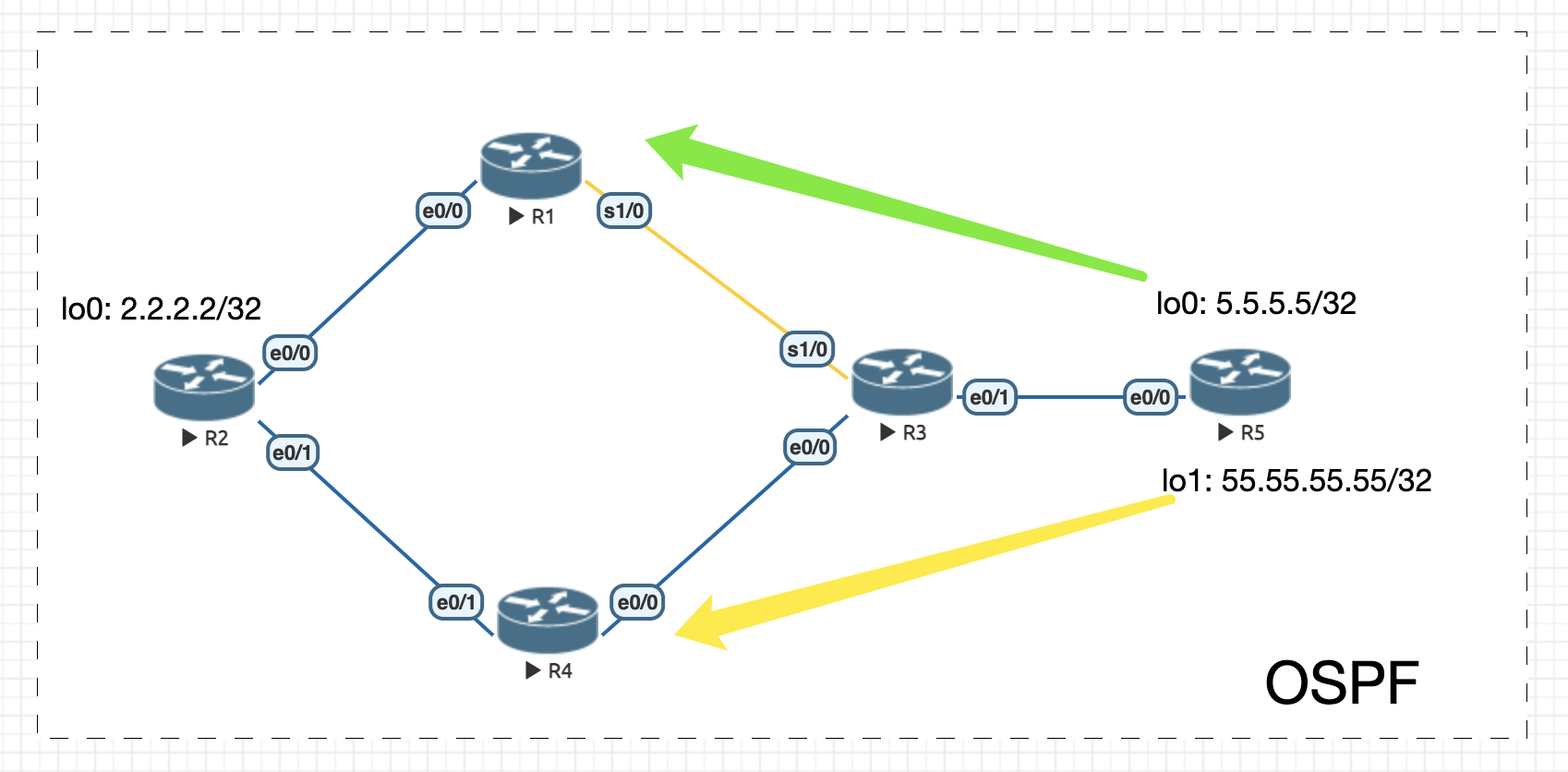
Figure 3: 实验环境
初始配置
----------------- R1 ---------------------- en conf t hostname R1 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int e0/0 ip address 10.1.12.1 255.255.255.0 no sh exit int s1/0 ip address 10.1.13.1 255.255.255.0 no sh exit router ospf 110 router-id 11.11.11.11 network 10.1.12.1 0.0.0.0 area 0 network 10.1.13.1 0.0.0.0 area 0 exit end ----------------- R2 ---------------------- en conf t hostname R2 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int lo0 ip address 2.2.2.2 255.255.255.255 exit int e0/0 ip address 10.1.12.2 255.255.255.0 no sh exit int e0/1 ip address 10.1.24.2 255.255.255.0 no sh exit router ospf 110 router-id 22.22.22.22 network 2.2.2.2 0.0.0.0 area 0 network 10.1.12.2 0.0.0.0 area 0 network 10.1.24.2 0.0.0.0 area 0 exit end ----------------- R3 ---------------------- en conf t hostname R3 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int e0/0 ip address 10.1.34.3 255.255.255.0 no sh exit int e0/1 ip address 10.1.35.3 255.255.255.0 no sh exit int s1/0 ip address 10.1.13.3 255.255.255.0 no sh exit router ospf 110 router-id 33.33.33.33 network 10.1.13.3 0.0.0.0 area 0 network 10.1.34.3 0.0.0.0 area 0 network 10.1.35.3 0.0.0.0 area 0 exit end ----------------- R4 ---------------------- en debug crypto ipsec client ezvpn conf t hostname R4 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int e0/0 ip address 10.1.34.4 255.255.255.0 no sh exit int e0/1 ip address 10.1.24.4 255.255.255.0 no sh exit router ospf 100 router-id 44.44.44.44 network 10.1.24.4 0.0.0.0 area 0 network 10.1.34.4 0.0.0.0 area 0 exit end ----------------- R5 ---------------------- en conf t hostname R5 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int lo0 ip address 5.5.5.5 255.255.255.255 exit int lo1 ip address 55.55.55.55 255.255.255.255 exit int e0/0 ip address 10.1.35.5 255.255.255.0 no sh exit router ospf 110 router-id 5.5.5.5 network 5.5.5.5 0.0.0.0 area 0 network 55.55.55.55 0.0.0.0 area 0 network 10.1.35.5 0.0.0.0 area 0 exit end
观察数据传输路径
R5#traceroute 2.2.2.2 source 5.5.5.5 Type escape sequence to abort. Tracing the route to 2.2.2.2 VRF info: (vrf in name/id, vrf out name/id) 1 10.1.35.3 0 msec 1 msec 0 msec 2 10.1.34.4 1 msec 0 msec 0 msec 3 10.1.24.2 1 msec * 1 msec R5#traceroute 2.2.2.2 source 55.55.55.55 Type escape sequence to abort. Tracing the route to 2.2.2.2 VRF info: (vrf in name/id, vrf out name/id) 1 10.1.35.3 0 msec 0 msec 0 msec 2 10.1.34.4 1 msec 1 msec 0 msec 3 10.1.24.2 1 msec * 1 msec
使用 PBR
========= R3 ========== en debug ip policy conf t hostname R3 no ip do lo line con 0 exec-timeout 0 0 logging synchronous exit int e0/0 ip address 10.1.34.3 255.255.255.0 no sh exit int e0/1 ip address 10.1.35.3 255.255.255.0 no sh exit int s1/0 ip address 10.1.13.3 255.255.255.0 no sh exit router ospf 110 router-id 33.33.33.33 network 10.1.13.3 0.0.0.0 area 0 network 10.1.34.3 0.0.0.0 area 0 network 10.1.35.3 0.0.0.0 area 0 exit ip access-list extended ACL5 permit ip 5.5.5.5 0.0.0.0 2.2.2.2 0.0.0.0 exit ip access-list extended ACL55 permit ip 55.55.55.55 0.0.0.0 2.2.2.2 0.0.0.0 exit route-map PBR permit 10 match ip address ACL5 set ip next-hop 10.1.13.1 exit route-map PBR permit 20 match ip address ACL55 set ip next-hop 10.1.34.4 exit int e0/1 ! must apply upon INCOMING interface ip policy route-map PBR exit end
再次观察数据传输路径
R5#traceroute 2.2.2.2 source 5.5.5.5
Type escape sequence to abort.
Tracing the route to 2.2.2.2
VRF info: (vrf in name/id, vrf out name/id)
1 10.1.35.3 1 msec 0 msec 1 msec
2 10.1.13.1 5 msec 5 msec 5 msec
3 10.1.12.2 5 msec * 5 msec
R5#
R3 debug 信息
R3# *Aug 6 09:36:21.025: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, policy match *Aug 6 09:36:21.025: IP: route map PBR, item 10, permit *Aug 6 09:36:21.025: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2 (Serial1/0), len 28, policy routed *Aug 6 09:36:21.025: IP: Ethernet0/1 to Serial1/0 10.1.13.1 *Aug 6 09:36:21.025: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, policy match *Aug 6 09:36:21.025: IP: route map PBR, item 10, permit *Aug 6 09:36:21.025: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2 (Serial1/0), len 28, policy routed *Aug 6 09:36:21.025: IP: Ethernet0/1 to Serial1/0 10.1.13.1 *Aug 6 09:36:21.026: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, policy match *Aug 6 09:36:21.026: IP: route map PBR, item 10, permit *Aug 6 09:36:21.026: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2 (Serial1/0), len 28, policy routed *Aug 6 09:36:21.026: IP: Ethernet0/1 to Serial1/0 10.1.13.1 *Aug 6 09:36:21.026: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:21.026: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:21.026: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed *Aug 6 09:36:21.031: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:21.031: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:21.031: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed *Aug 6 09:36:21.036: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:21.036: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:21.036: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed *Aug 6 09:36:21.041: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:21.041: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:21.041: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed *Aug 6 09:36:21.046: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:21.046: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:21.046: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed *Aug 6 09:36:24.048: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, FIB policy match *Aug 6 09:36:24.048: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, len 28, PBR Counted *Aug 6 09:36:24.048: IP: s=5.5.5.5 (Ethernet0/1), d=2.2.2.2, g=10.1.13.1, len 28, FIB policy routed
策略不命中的情况
R5#ping 2.2.2.2 r 1 Type escape sequence to abort. Sending 1, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds: ! Success rate is 100 percent (1/1), round-trip min/avg/max = 1/1/1 ms ------------------------ R3# *Aug 6 09:47:42.653: IP: s=10.1.35.5 (Ethernet0/1), d=2.2.2.2, len 100, FIB policy rejected(no match) - normal forwarding R3#