ASA(v)
{Back to Index}
Table of Contents
1 配置 ASA
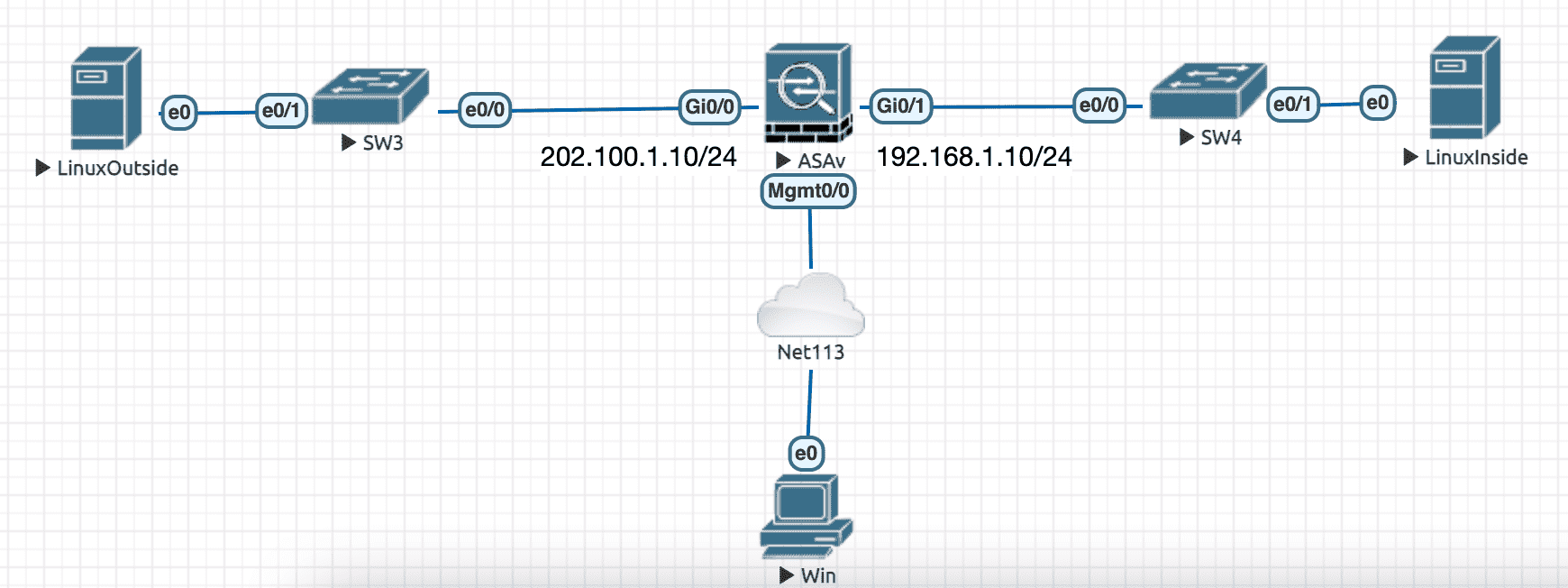
Figure 1: 拓扑示例
配置 IP 地址
ciscoasa> en Password: ciscoasa# conf t ciscoasa(config)# int manage0/0 ciscoasa(config-if)# nameif management INFO: Security level for "management" set to 0 by default. ciscoasa(config-if)# ip add dh ciscoasa(config-if)# no sh ciscoasa(config-if)# int g0/0 ciscoasa(config-if)# nameif outside ! 名字决定了 security level INFO: Security level for "outside" set to 0 by default. ciscoasa(config-if)# ip add 202.100.1.10 255.255.255.0 ciscoasa(config-if)# no sh ciscoasa(config-if)# int g0/1 ciscoasa(config-if)# nameif inside INFO: Security level for "inside" set to 100 by default. ciscoasa(config-if)# ip add 192.168.1.10 255.255.255.0 ciscoasa(config-if)# no sh ciscoasa(config-if)# sh ip add System IP Addresses: Interface Name IP address Subnet mask Method GigabitEthernet0/0 outside 202.100.1.10 255.255.255.0 manual GigabitEthernet0/1 inside 192.168.1.10 255.255.255.0 manual Management0/0 management 10.74.113.104 255.255.255.0 DHCP Current IP Addresses: Interface Name IP address Subnet mask Method GigabitEthernet0/0 outside 202.100.1.10 255.255.255.0 manual GigabitEthernet0/1 inside 192.168.1.10 255.255.255.0 manual Management0/0 management 10.74.113.104 255.255.255.0 DHCP
日志
logging console info logging enable
配置 http 服务器
username cisco password Cisco123 privilege 15
http 0 0 management ! 从 management 接口进来,并且处于该网段的地址(偷懒填 0 0 表示所有地址),可以访问服务器
aaa authentication http console LOCAL
http server enable
启动ASDM
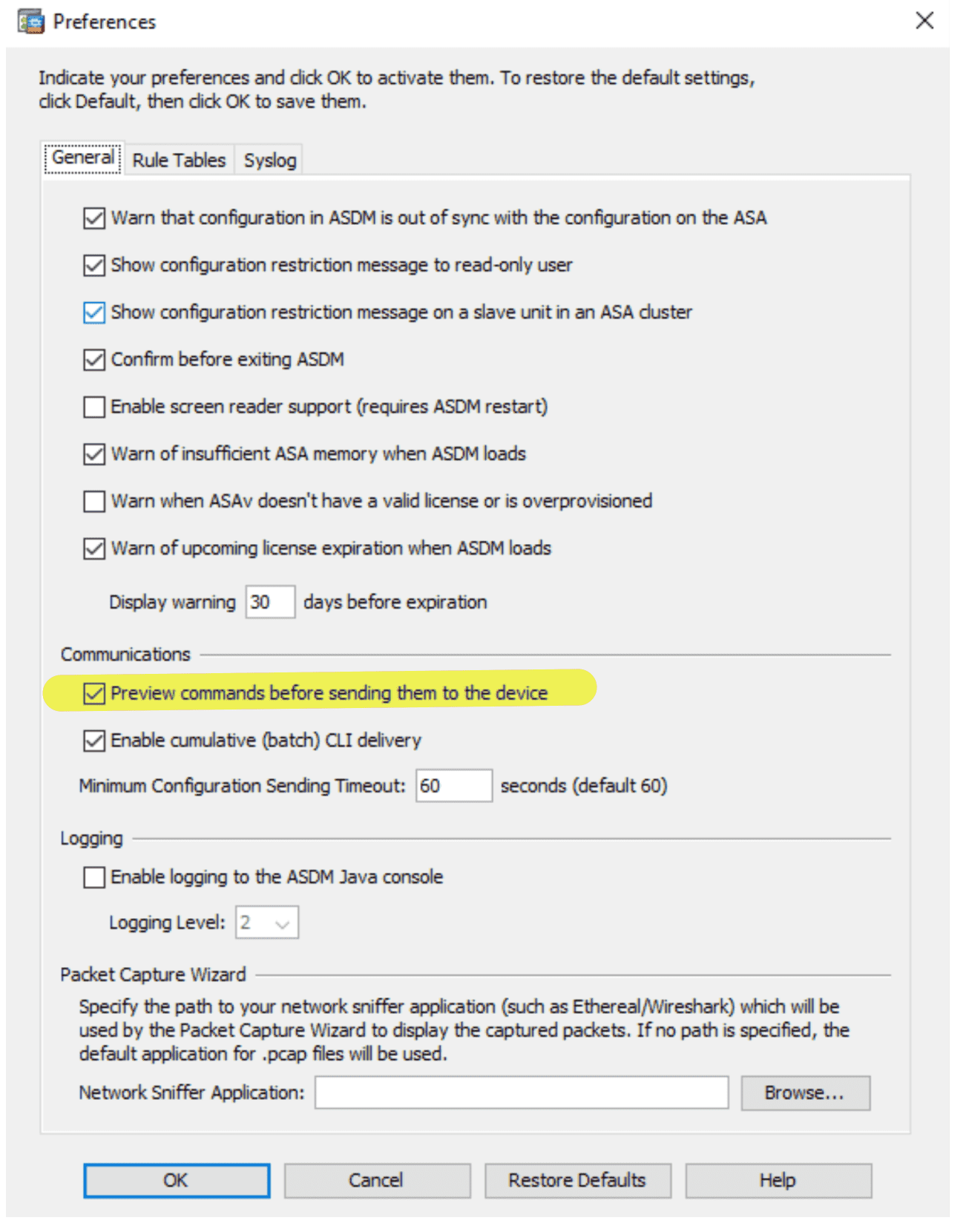
Figure 3: 建议勾选
默认外部无法主动访问内部,可以使用 ACL 来允许访问:
ciscoasa(config)# access-list Outside-In extended permit tcp host 202.100.1.101 host 192.168.1.101 eq 8080
ciscoasa(config)# access-group Outside-In in interface outside
ciscoasa(config)# sh conn detail
3 in use, 8 most used
Flags: A - awaiting inside ACK to SYN, a - awaiting outside ACK to SYN,
B - initial SYN from outside, b - TCP state-bypass or nailed,
C - CTIQBE media, c - cluster centralized,
D - DNS, d - dump, E - outside back connection, e - semi-distributed,
F - outside FIN, f - inside FIN,
G - group, g - MGCP, H - H.323, h - H.225.0, I - inbound data,
i - incomplete, J - GTP, j - GTP data, K - GTP t3-response
k - Skinny media, M - SMTP data, m - SIP media, n - GUP
O - outbound data, P - inside back connection,
q - SQL*Net data, R - outside acknowledged FIN,
R - UDP SUNRPC, r - inside acknowledged FIN, S - awaiting inside SYN,
s - awaiting outside SYN, T - SIP, t - SIP transient, U - up,
V - VPN orphan, W - WAAS,
w - secondary domain backup,
X - inspected by service module,
x - per session, Y - director stub flow, y - backup stub flow,
Z - Scansafe redirection, z - forwarding stub flow
TCP outside: 202.100.1.101/57702 inside: 192.168.1.101/8080,
flags UIB , idle 11s, uptime 13s, timeout 1h0m, bytes 14
! B 表示从外部主动发起的流量
ciscoasa(config)#
1.1 Telnet 1
ASAv(config)# username cisco password Cisco123 privilege 15 ASAv(config)# telnet 10.74.113.0 255.255.255.0 management ASAv(config)# aaa authentication telnet console LOCAL ASAv(config)# aaa authorization exec auth auto-enable ! into enable mode directly after login (after v9.1.5) ASAv(config)# int m0/0 ASAv(config-if)# security-level 100 ! 因为 ASA 不允许从安全级别最低的端口上进行 telnet , 直接设为 100 一了百了
2 常用命令
2.1 查看模式
路由墙还是透明墙
show firewall
2.2 还原出厂配置
clear config all
2.3 删除所有特定类型配置
比如要删除所有关于 object-group 的配置:
clear config object-group
2.4 查看接口地址
sh int ip b
2.5 查看接口名与安全等级
sh nameif
2.6 查看状态化表项
sh conn
2.7 查看 nat 转换表项
sh xlate
2.8 查看 nat 配置
! 两个结合起来一起看,因为 nat 既可以配置在全局,也可以配置在 object 下
! 而只看 object 看不到 nat 相关配置
sh run object
sh run nat
2.9 查看 service policy 执行状态
ASA(config)# sh service-policy interface inside
Interface Inside:
Service-policy: L3_Policy
Class-map: L3_ACL_Class
Inspect: http L7_HTTP_Policy, packet 74, drop 18, reset-drop 18, v6-fail-close 0
3 Security Level
- 安全级别范围是 0-100 ,接口名称含有 inside 字样的默认级别为 100 ,其余皆为 0
- 从高级别接口到低级别接口的流量称为 Outbound 流量,默认是允许的
- 从低级别接口到高级别接口的流量称为 Inbound 流量,默认是 不允许 的, 但可以使用 ACL 放行 2
- 相同安全级别接口之间流量默认是不允许的,但可以通过
permit inter-interface予以放行
3.1 Same security traffic
ASA 默认相同接口级别间不允许转发流量,而且 也不会把从同一接口进入的流量再从相同接口转发出来 。
前者可以通过 permit inter-interface 来放行,后者可以通过 permit intra-interface 来放行。
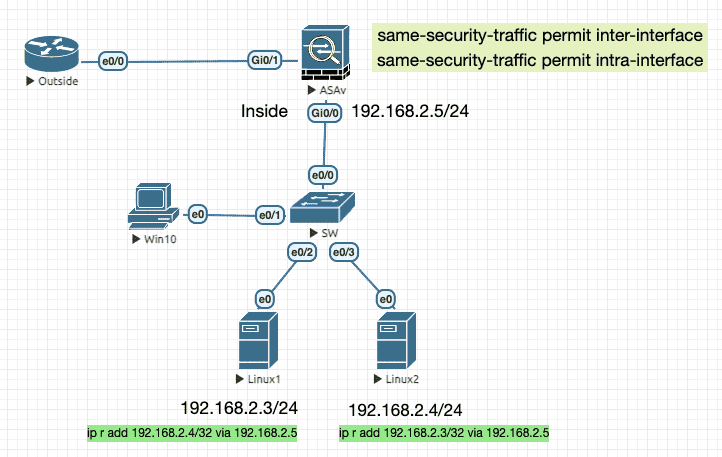
Figure 4: 实验拓扑
ASA 初始配置
en conf t hostname ASAv int g0/0 nameif Inside ip add dh no sh ! username cisco password Cisco123 privilege 15 http server enable http 192.168.2.0 255.255.255.0 Inside aaa authentication http console LOCAL
配置放行策略
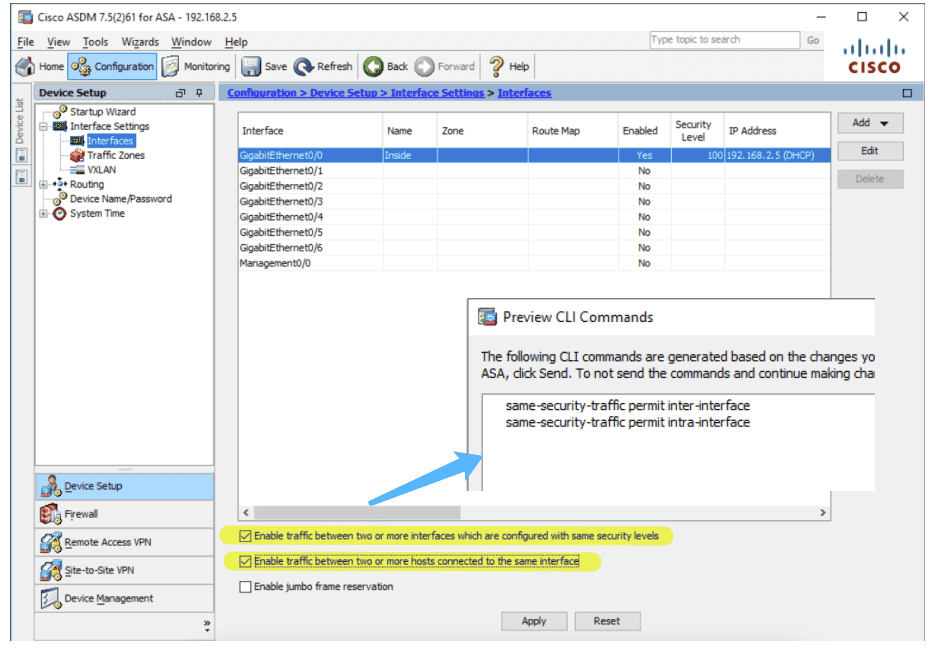
Figure 5: 放行后,Linux 主机间可以借由 ASA (充当网关)进行通信
4 NAT
4.1 概述
ASA >8.3+ 的 NAT 设计分两类:
- Network Object NAT (自动 NAT)
- Twice NAT (手动 NAT)
自动 NAT 适用于 大多数 应用场景,手动 NAT 可以用于 特殊应用场景 (全能且支持策略NAT,但配置相对复杂,常见应用都能在自动 NAT 中覆盖)。
从配置特点上看:
- 自动 NAT 需要在 object network 模式下配置 NAT 规则
- 手动 NAT 需要在全局模式下配置 NAT 规则,并调用 object network 对象
两种配置方式的整体执行顺序:(Unified NAT Rule Table) 【手动有2个section,自动的只有1个section】
##########################
# Section 1 #
# 常规手动 NAT #
##########################
||
\/
##########################
# Section 2 #
# 自动 NAT #
##########################
||
\/
##########################
# Section 3 #
# After-Auto 手动 NAT #
##########################
两种配置方式的内部执行顺序:
手动
先匹配原则 ,因此可以随意调整顺序
自动
静态优于动态 ,如果类型相同则按照掩码长度,IP 地址大小,名称字母顺序进行排序
从分配表项的角度看 ,NAT 可分为静态和动态两种类型:
dynamic
当匹配符合规则的流量出现时,动态生成转换表项。
staic
当手动配置好转换规则后,转换表项就已生成好,只要配置不删除,表项就一直存在。
4.2 应用场景
4.2.1 动态 NAT (一对一)
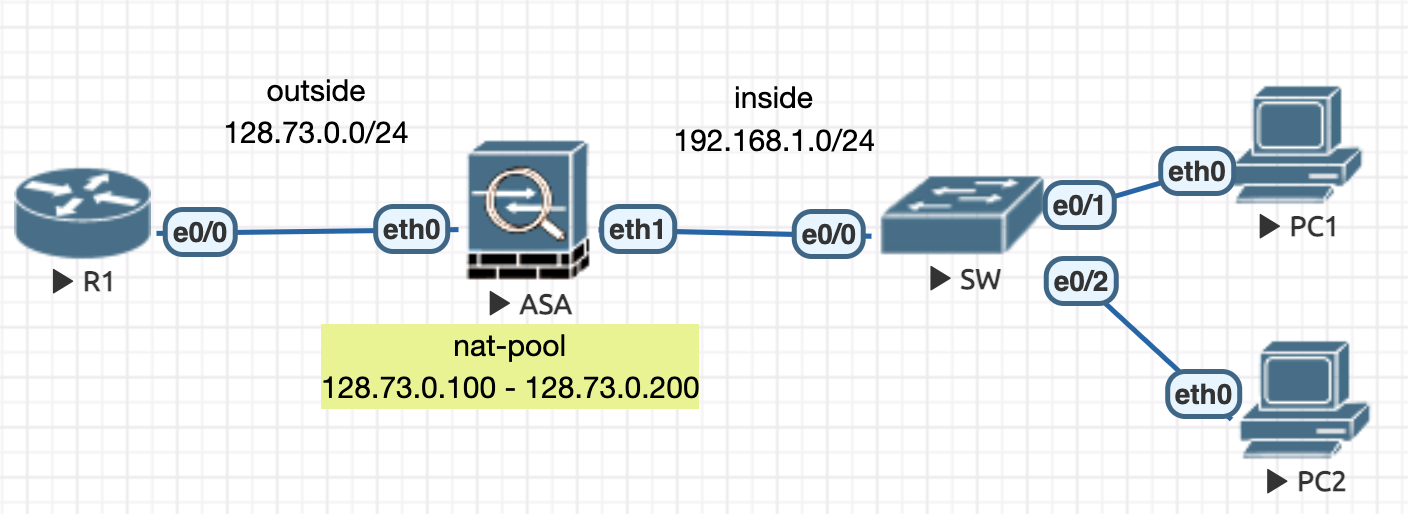
Figure 6: 私网用户每人分配一个公网地址
初始配置
! ################################################### ! # R1 # ! ################################################### int e0/0 ip add 128.73.0.1 255.255.255.0 no sh ! ! ################################################### ! # ASA # ! ################################################### policy-map global_policy class inspection_default inspect icmp ! int e0 nameif outside ip add 128.73.0.10 255.255.255.0 no sh ! int e1 nameif inside ip add 192.168.1.10 255.255.255.0 no sh !
NAT 配置
! ################################################### ! # ASA # ! ################################################### object network NAT-POOL range 128.73.0.100 128.73.0.200 ! object network PRIVATE-SRC subnet 192.168.1.0 255.255.255.0 nat (inside,outside) dynamic NAT-POOL !
show
! ####################### check ####################### ciscoasa(config)# sh run obj object network NAT-POOL range 128.73.0.100 128.73.0.200 object network PRIVATE-SRC subnet 192.168.1.0 255.255.255.0 ciscoasa(config)# sh run nat ! object 和 nat 是分开显示的 ! object network PRIVATE-SRC nat (inside,outside) dynamic NAT-POOL ciscoasa(config)# sh conn ! 状态化表项(瞬时) 0 in use, 2 most used ciscoasa(config)# sh xlate ! 转换表项(默认保存3小时) 2 in use, 2 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net NAT from inside:192.168.1.2 to outside:128.73.0.114 flags i idle 0:00:10 timeout 3:00:00 NAT from inside:192.168.1.1 to outside:128.73.0.124 flags i idle 0:00:53 timeout 3:00:00
4.2.2 动态 PAT (多对一) 【最常见】
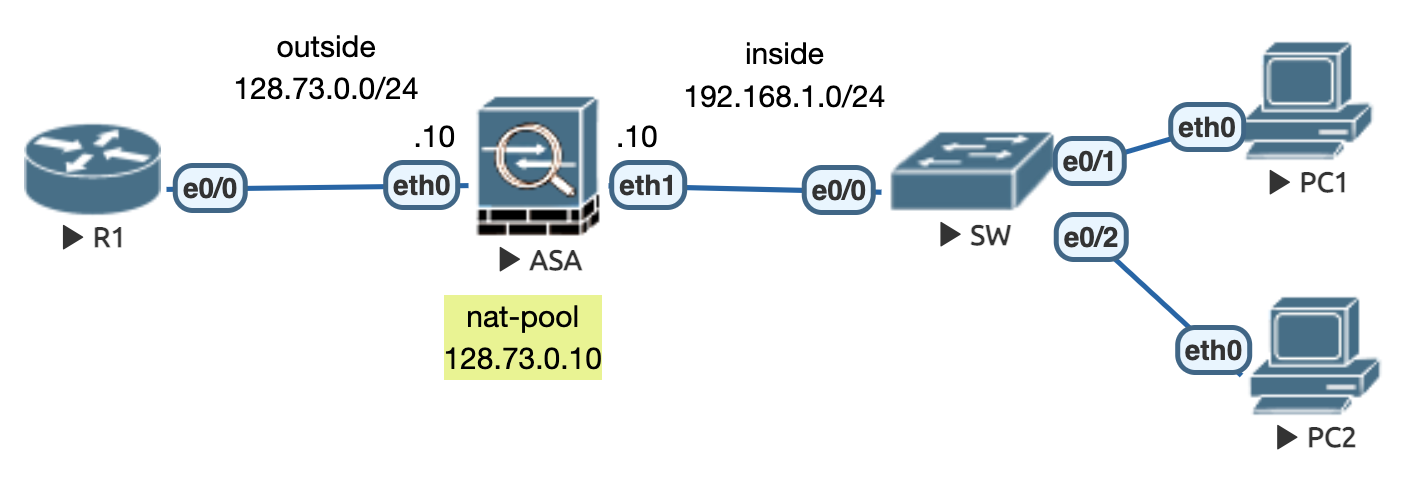
初始配置同上。
PAT 配置
! ################################################### ! # ASA # ! ################################################### !!! 当地址池仅有一个地址时,系统自动认为做PAT而不是NAT。!!! object network MY-PAT-POOL host 128.73.0.11 ! 不同于接口地址 ! object network PRIVATE-SRC subnet 192.168.1.0 255.255.255.0 nat (inside,outside) dynamic MY-PAT-POOL !
show
ciscoasa(config)# sh xlate
5 in use, 10 most used
Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap,
s - static, T - twice, N - net-to-net
ICMP PAT from inside:192.168.1.1/32720 to outside:128.73.0.11/32720 flags ri idle 0:00:02 timeout 0:00:30 ! 连接断开 30s 后回收表项
ICMP PAT from inside:192.168.1.1/32464 to outside:128.73.0.11/32464 flags ri idle 0:00:03 timeout 0:00:30
ICMP PAT from inside:192.168.1.1/32208 to outside:128.73.0.11/32208 flags ri idle 0:00:04 timeout 0:00:30
ICMP PAT from inside:192.168.1.1/31952 to outside:128.73.0.11/31952 flags ri idle 0:00:05 timeout 0:00:30
ICMP PAT from inside:192.168.1.1/31696 to outside:128.73.0.11/31696 flags ri idle 0:00:06 timeout 0:00:30
其他演化配置方式:
简化私网地址配置方式
object network MY-PAT-POOL host 128.73.0.11 ! object network PRIVATE-SRC subnet 0 0 nat (inside,outside) dynamic MY-PAT-POOL !
省略 object network
! 如果只有一个地址,可以直接写
object network PRIVATE-SRC
subnet 0 0
nat (inside,outside) dynamic 128.73.0.11
!
直接使用出接口地址
object network PRIVATE-SRC subnet 0 0 nat (inside,outside) dynamic interface ! ciscoasa(config-network-object)# sh xl 5 in use, 10 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net ICMP PAT from inside:192.168.1.1/35284 to outside:128.73.0.10/35284 flags ri idle 0:00:01 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/35028 to outside:128.73.0.10/35028 flags ri idle 0:00:02 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/34772 to outside:128.73.0.10/34772 flags ri idle 0:00:03 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/34516 to outside:128.73.0.10/34516 flags ri idle 0:00:03 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/34260 to outside:128.73.0.10/34260 flags ri idle 0:00:04 timeout 0:00:30
多个地址PAT(pat-pool)
! 当地址池仅有一个地址时,系统自动认为做PAT而不是NAT。 ! 但当地址池多于一个地址时,则必须加上 pat-pool 参数以避免被当做动态NAT一对一 object network MY-PAT-POOL range 128.73.0.11 128.73.0.12 ! object network PRIVATE-SRC subnet 0 0 nat (inside,outside) dynamic pat-pool MY-PAT-POOL ! ciscoasa(config-network-object)# sh xl 6 in use, 35 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net ICMP PAT from inside:192.168.1.2/58589 to outside:128.73.0.11/58589 flags ri idle 0:00:00 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/58333 to outside:128.73.0.11/58333 flags ri idle 0:00:01 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/58077 to outside:128.73.0.11/58077 flags ri idle 0:00:02 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/57565 to outside:128.73.0.11/57565 flags ri idle 0:00:03 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/57309 to outside:128.73.0.11/57309 flags ri idle 0:00:04 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/57053 to outside:128.73.0.11/57053 flags ri idle 0:00:05 timeout 0:00:30
多个地址PAT(pat-pool/round-robin)
! 多个出口地址轮流使用 object network MY-PAT-POOL range 128.73.0.11 128.73.0.12 ! object network PRIVATE-SRC subnet 0 0 nat (inside,outside) dynamic pat-pool MY-PAT-POOL round-robin ! ciscoasa(config)# sh xl 7 in use, 35 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net ICMP PAT from inside:192.168.1.2/35293 to outside:128.73.0.12/35293 flags ri idle 0:00:06 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/35037 to outside:128.73.0.12/35037 flags ri idle 0:00:07 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/34781 to outside:128.73.0.12/34781 flags ri idle 0:00:08 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/34525 to outside:128.73.0.12/34525 flags ri idle 0:00:09 timeout 0:00:30 ICMP PAT from inside:192.168.1.2/34013 to outside:128.73.0.12/34013 flags ri idle 0:00:09 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/36061 to outside:128.73.0.11/36061 flags ri idle 0:00:04 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/35805 to outside:128.73.0.11/35805 flags ri idle 0:00:05 timeout 0:00:30
先做一对一NAT,地址不够再PAT
object network MY-NAT-POOL range 128.73.0.11 128.73.0.12 ! object network MY-PAT-POOL host 128.73.0.13 ! object-group network POOLS network-object obj MY-NAT-POOL network-object obj MY-PAT-POOL ! object network PRIVATE-SRC subnet 0 0 nat (inside,outside) dynamic POOLS ! ciscoasa(config-network-object)# sh xl 7 in use, 35 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net NAT from inside:192.168.1.2 to outside:128.73.0.12 flags i idle 0:00:07 timeout 3:00:00 ICMP PAT from inside:192.168.1.1/24550 to outside:128.73.0.13/24550 flags ri idle 0:00:00 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/24294 to outside:128.73.0.13/24294 flags ri idle 0:00:01 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/24038 to outside:128.73.0.13/24038 flags ri idle 0:00:02 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/23782 to outside:128.73.0.13/23782 flags ri idle 0:00:03 timeout 0:00:30 ICMP PAT from inside:192.168.1.1/23270 to outside:128.73.0.13/23270 flags ri idle 0:00:03 timeout 0:00:30 NAT from inside:192.168.1.3 to outside:128.73.0.11 flags i idle 0:00:10 timeout 3:00:00
4.2.3 静态一对一 【通常用于发布内部服务器】
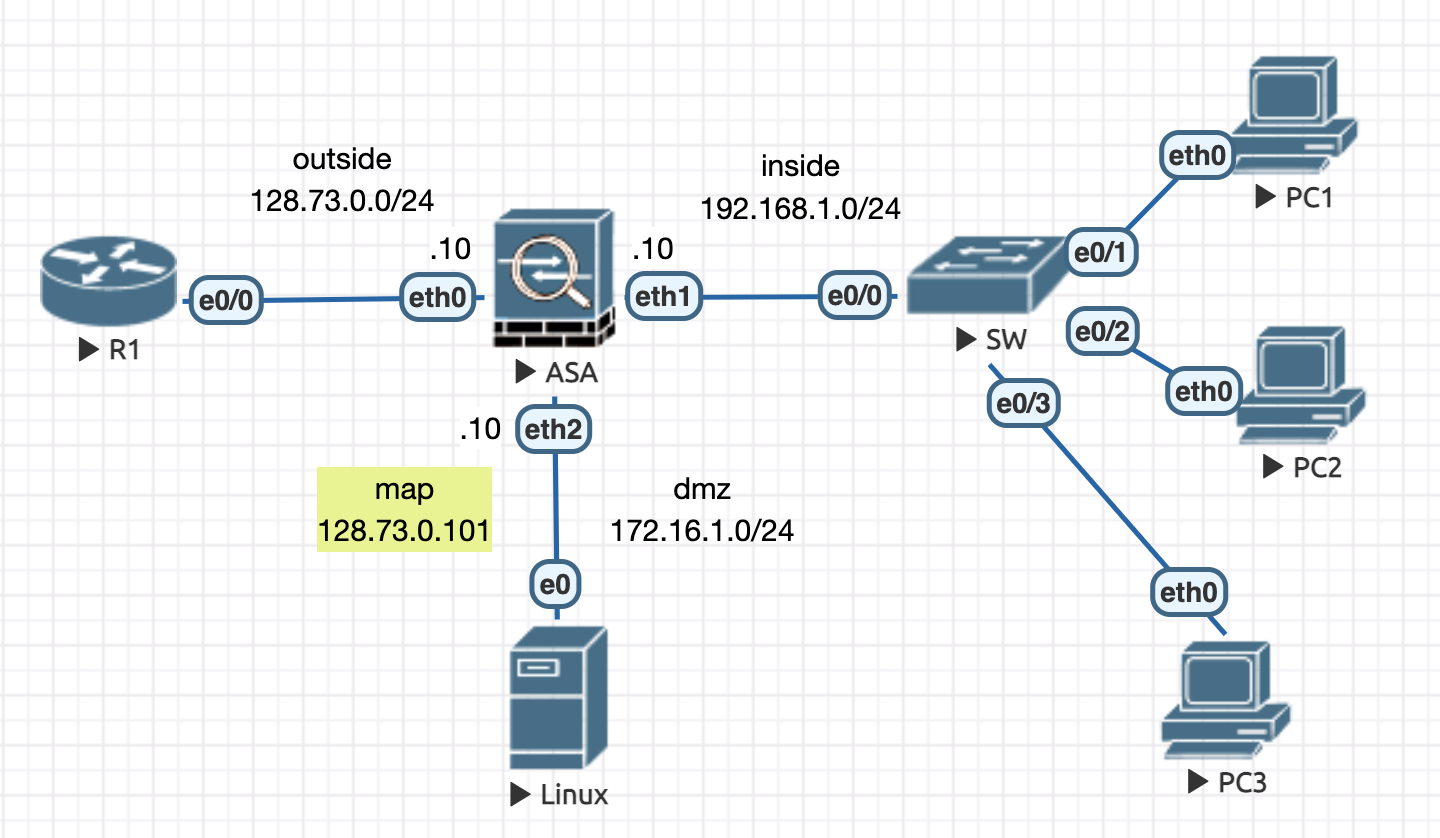
初始配置
! ################################################### ! # R1 # ! ################################################### int e0/0 ip add 128.73.0.1 255.255.255.0 no sh ! ip route 0.0.0.0 0.0.0.0 128.73.0.10 ! ################################################### ! # ASA # ! ################################################### policy-map global_policy class inspection_default inspect icmp ! int e0 nameif outside ip add 128.73.0.10 255.255.255.0 no sh ! int e1 nameif inside ip add 192.168.1.10 255.255.255.0 no sh ! int e2 nameif dmz security-level 50 ip add 172.16.1.10 255.255.255.0 no sh !
static NAT 1/1 config
! ################################################### ! # ASA # ! ################################################### ! object network MY_MAP ! host 128.73.0.101 ! ! object network PRIVATE_SRC ! host 172.16.1.1 ! nat (dmz,outside) static MY_MAP ! ! 其实可以省略定义 MY_MAP ,因为只有一个 IP ,可以直接 inline 方式写: object network PRIVATE_SRC host 172.16.1.1 nat (dmz,outside) static 128.73.0.101 ! ! 别忘了配置 ACL ,这里放行所有 IP ,实际中根据需求可以限定协议和端口 ! 注意,这里放行内网地址,即 DNAT 后的地址 access-list ACL_1 permit ip any host 172.16.1.1 access-group ACL_1 in interface outside ! 配置好后,转换表项就生成好了,且没有超时时间 ciscoasa(config-network-object)# sh xl 1 in use, 1 most used Flags: D - DNS, e - extended, I - identity, i - dynamic, r - portmap, s - static, T - twice, N - net-to-net NAT from dmz:172.16.1.1 to outside:128.73.0.101 flags s idle 0:00:00 timeout 0:00:00
4.2.4 静态端口转换
拓扑同上
static port mapping config
! ###################################################
! # ASA #
! ###################################################
object network PRIVATE_SRC
host 172.16.1.1
nat (dmz,outside) static interface service tcp 80 8080
!
access-list ACL_1 permit tcp any host 172.16.1.1 eq 80
access-group ACL_1 in interface outside
! 172.16.1.1:80 对外以 128.73.0.10:8080 的形式暴露服务
4.2.5 基于策略 NAT 【手动配置方式】
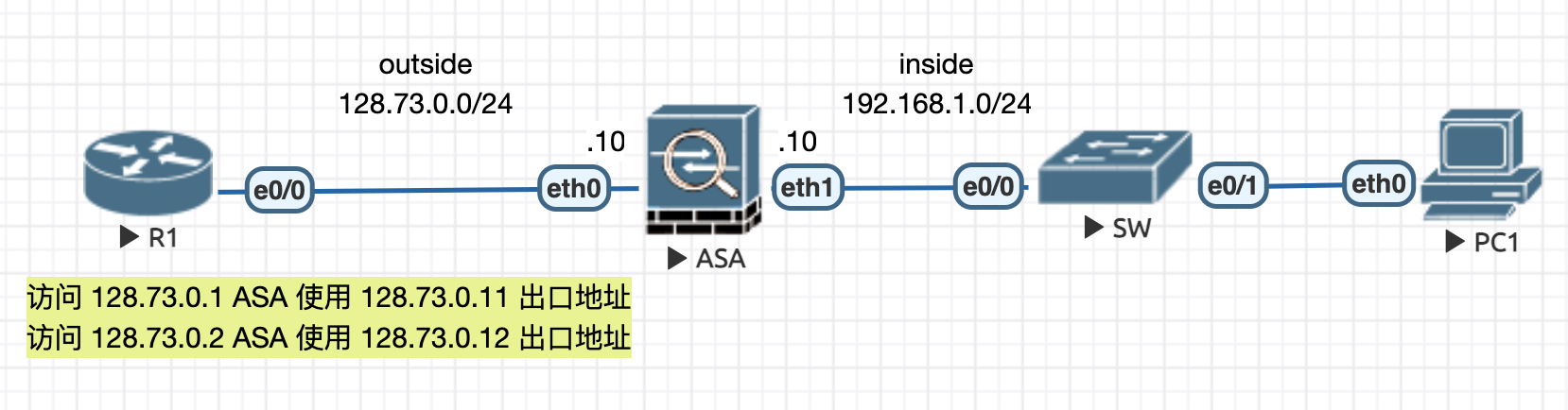
初始配置
! ################################################### ! # R1 # ! ################################################### int e0/0 ip add 128.73.0.1 255.255.255.0 ip add 128.73.0.2 255.255.255.0 secondary no sh ! ip route 0.0.0.0 0.0.0.0 128.73.0.10 ! ################################################### ! # ASA # ! ################################################### policy-map global_policy class inspection_default inspect icmp ! int e0 nameif outside ip add 128.73.0.10 255.255.255.0 no sh ! int e1 nameif inside ip add 192.168.1.10 255.255.255.0 no sh ! !
config
! ################################################### ! # ASA # ! ################################################### object network DST-1 host 128.73.0.1 ! object network DST-2 host 128.73.0.2 ! object network PAT-1 host 128.73.0.11 ! object network PAT-2 host 128.73.0.22 ! object network PRIVATE_SRC subnet 0 0 exit ! must be under global config mode nat (inside,outside) source dynamic PRIVATE_SRC PAT-1 destination static DST-1 DST-1 nat (inside,outside) source dynamic PRIVATE_SRC PAT-2 destination static DST-2 DST-2 ! 当流量从 inside 流向 outside 时,如源地址为 PRIVATE-SRC ,目的地址为 DST-1 ,则将源地址转换为 PAT-1 ,目标地址仍为 DST-1 ! 当流量从 inside 流向 outside 时,如源地址为 PRIVATE-SRC ,目的地址为 DST-2 ,则将源地址转换为 PAT-2 ,目标地址仍为 DST-2 ! source 后面的 dynamic/static 表示是动态 SNAT 还是静态 SNAT ,紧跟的两个对象,前者是实际源地址,后者是转换后源地址。 ! 而 destination 后只能跟 static ,表明目的地址只能静态明确指定,紧跟的两个对象,前者是转换后的地址,后者是实际地址。 ! 可以看出,这种手动的配置方式可以实现源目地址同时转换。(只是这个例子中,目的地址保持不变)
4.2.6 DNS Rewrite (属于静态一对一) 3
用于内部有服务器并在出口做了 Static NAT 映射到公网地址,同时内部又有访问该服务器的需求的场景。 由于内部不能直接访问服务器的外网地址,因为这相当于访问【防火墙背后的接口地址】,这是被禁止的。
当然也可以考虑架设内部 DNS 服务器,将域名映射到内部服务器地址。
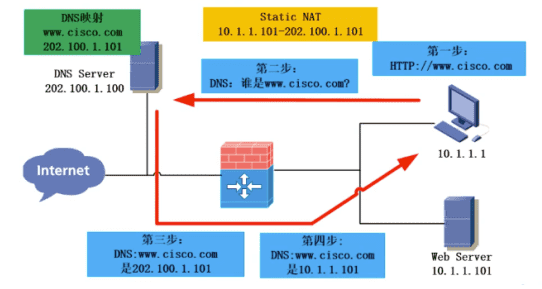
Figure 10: 原理示意
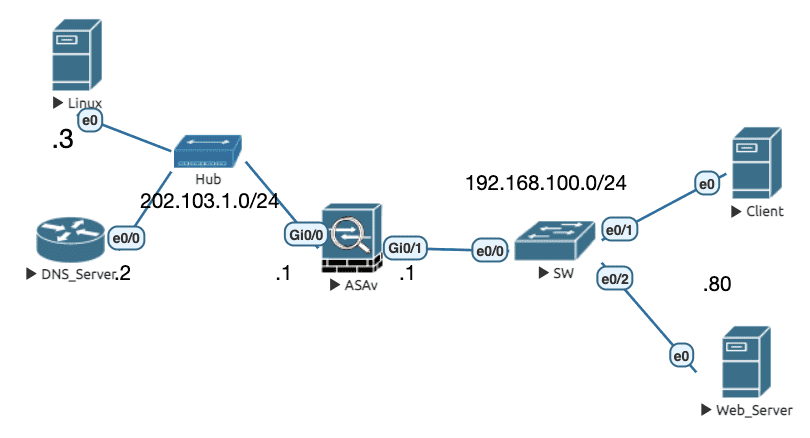
Figure 11: 实验拓扑
初始配置
! ###################################################
! # Static NAT (DNS rewrite) configuration #
! ###################################################
object network Internal_Server
host 192.168.100.80
nat (Inside,Outside) static 202.103.1.80 dns
!
access-list Outside_To_Inside_ACL extended permit tcp any host 192.168.100.80
access-group Outside_To_Inside_ACL in interface Outside
4.2.7 Identity NAT (转换前后源目地址不变) 【手动配置方式】
ASA 通过 outside 接口与远端站点建立 VPN , 同时为私网提供 PAT 上网服务。由于执行步骤上会先做 PAT ,后做 VPN 感兴趣流匹配,因此会导致站点间数据无法使用 VPN 。此时就需要将 VPN 感兴趣流从 PAT 转换规则中排除,这种场景只能使用手动方式配置,因为这种场景隐含了策略 NAT 的工作方式(即需要区分目的地址,这是自动 NAT 做不到的)。
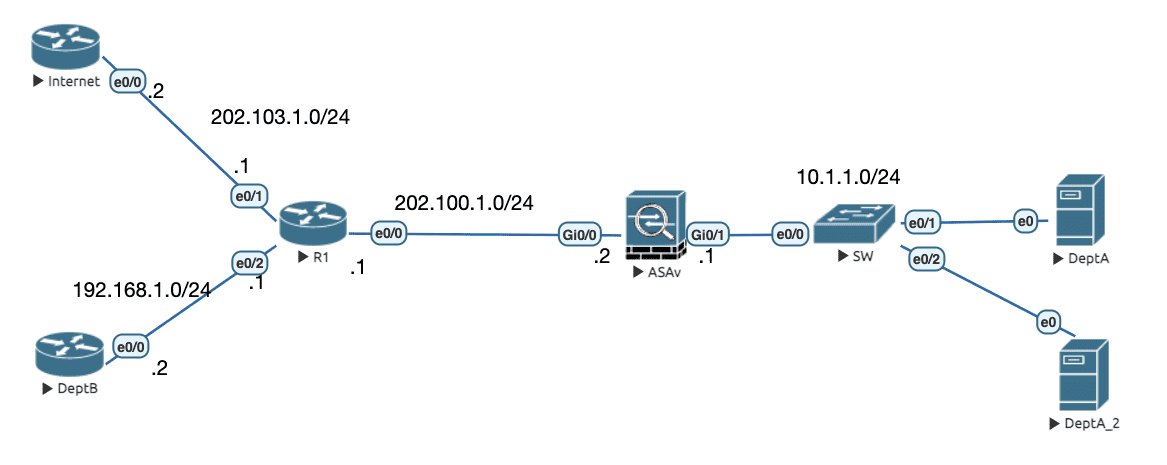
Figure 12: 实验拓扑(NAT 旁路)
初始配置
! ################################################### ! # Configure Identity NAT # ! ################################################### object network Inside_Network subnet 10.1.1.0 255.255.255.0 ! object network VPN subnet 192.168.1.0 255.255.255.0 ! nat (Inside,Outside) source static Inside_Network Inside_Network destination static VPN VPN ! ##################################################### ! # Method 1: Configure PAT for rest traffic (manual) # ! ##################################################### nat (Inside,Outside) source dynamic Inside_Network interface ! 如果按照上一条这么配置,观察 nat rule : ciscoasa(config)# sh nat detail Manual NAT Policies (Section 1) 1 (Inside) to (Outside) source static Inside_Network Inside_Network destination static VPN VPN translate_hits = 33, untranslate_hits = 33 Source - Origin: 10.1.1.0/24, Translated: 10.1.1.0/24 Destination - Origin: 192.168.1.0/24, Translated: 192.168.1.0/24 2 (Inside) to (Outside) source dynamic Inside_Network interface ! 这条相当于 default translate_hits = 60, untranslate_hits = 0 Source - Origin: 10.1.1.0/24, Translated: 202.100.1.2/24 ! ################################################### ! # Method 2: Configure PAT for rest traffic (auto) # ! ################################################### object network Inside_Network subnet 10.1.1.0 255.255.255.0 nat (Inside,Outside) dynamic interface ! ! 如果按照上一条这么配置,观察 nat rule : ciscoasa(config)# sh nat detail Manual NAT Policies (Section 1) 1 (Inside) to (Outside) source static Inside_Network Inside_Network destination static VPN VPN translate_hits = 401, untranslate_hits = 401 Source - Origin: 10.1.1.0/24, Translated: 10.1.1.0/24 Destination - Origin: 192.168.1.0/24, Translated: 192.168.1.0/24 Auto NAT Policies (Section 2) 1 (Inside) to (Outside) source dynamic Inside_Network interface translate_hits = 7, untranslate_hits = 0 Source - Origin: 10.1.1.0/24, Translated: 202.100.1.2/24 ! 因为此时 PAT 是自动配置方式,位于 united rule table 的 section 2 中,手动配置位于 section 1 中, ! 因此 VPN 流量在 section 1 中优先匹配处理了,这就达到了 bypass 的目的
! ################################################### ! # DeptA# telnet 192.168.1.2 # ! ################################################### DeptB#who Line User Host(s) Idle Location * 0 con 0 idle 00:00:00 2 vty 0 cisco idle 00:00:10 10.1.1.2 Interface User Mode Idle Peer Address ! ################################################### ! # DeptA# telnet 202.103.1.1 # ! ################################################### Internet#who Line User Host(s) Idle Location * 0 con 0 idle 00:00:00 2 vty 0 cisco idle 00:00:25 202.100.1.2 Interface User Mode Idle Peer Address
5 MPF
MPF 是一种流量策略框架,即使用 class-map 定义需要执行访问控制的流量,并将 class-map 关联到 policy-map ,最后使用 service-policy 在接口或者全局激活该策略。即:
- class-map(which)
- 表示针对什么流量做策略
- policy-map(what)
- 表示要做什么策略(inspect)
- service-policy(where)
- 表示在哪里调用(执行)策略
注意:
- 全局和每一个接口 只能 配置一个
policy-map - 默认有个名为 global_plolicy 的全局
policy-map,不需要新建全局的policy-map,复用这个默认的即可(定义额外的class-map) - 接口上的策略应用于 in/out 两个方向,全局策略只针对 in 方向。不过,policing(流量监管) 可指定方向,以及 priority(优先队列)只能用于 out 方向。
层次结构举例
! ################################################### ! # service-policy => policy-map => class-map # ! ################################################### ASAv(config)# sh run service-policy service-policy global_policy global ASAv(config)# sh run policy-map policy-map global_policy class inspection_default inspect ip-options inspect netbios inspect rtsp inspect sunrpc inspect tftp ! 按照 tftp 流量特征去 inspect inspect xdmcp inspect dns preset_dns_map ... ASAv(config)# sh run class-map ! class-map inspection_default match default-inspection-traffic ! | | | | | mpf-class-map mode commands/options: | access-list Match an Access List | any Match any packet |-> default-inspection-traffic Match default inspection traffic: ctiqbe----tcp--2748 diameter--tcp--3868 diameter--tcp/tls--5868 diameter--sctp-3868 dns-------udp--53 ftp-------tcp--21 gtp-------udp--2123,3386 h323-h225-tcp--1720 h323-ras--udp--1718-1719 http------tcp--80 icmp------icmp ils-------tcp--389 ip-options-----rsvp m3ua------sctp-2905 mgcp------udp--2427,2727 netbios---udp--137-138 radius-acct----udp--1646 rpc-------udp--111 rsh-------tcp--514 rtsp------tcp--554 sip-------tcp--5060 sip-------udp--5060 skinny----tcp--2000 smtp------tcp--25 sqlnet----tcp--1521 tftp------udp--69 vxlan-----udp--4789 waas------tcp--1-65535 xdmcp-----udp--177 dscp Match IP DSCP (DiffServ CodePoints) flow Flow based Policy port Match TCP/UDP/SCTP port(s) precedence Match IP precedence rtp Match RTP port numbers tunnel-group Match a Tunnel Group
5.1 L3/L4 监控配置步骤
- 创建 class-map ,根据特征匹配流量
- 创建 policy-map
- 调用 class-map ,明确对什么对象设定策略
- 分别对某类(class)流量设置行为:
- QoS policing or shaping
- 优先队列
- 将流量发送到 AIP-SSM (IPS)
- 将流量发送到 CSC-SSM (AV)
- Netflow 分析(对包头信息进行分类统计)
- 应用程序监控(SPI)
- 连接参数设置 (set connection) ,还可以关联一个 tcp-map ,在其中定义 TCP 会话参数
调用到全局或某个接口
调用时无需手动指定策略生效方向,会根据策略内容和调用点不同动态决定方向,比如整形(shaping)和优先队列(priority)只能是出向,而接口调用都是双向,全局调用则是所有接口入向。
- 一个 policy-map 可以包含多个 class-map ,数据包从上到下匹配,匹配到就执行然后退出, 所以不存在多次匹配执行
5.2 L7 监控配置步骤
L7 策略只能针对特定的应用层协议进行操作(不是所有协议都支持的)。
配置步骤:
- 创建 class-map type inspect <proto> match-any|match-all(加 type 表示是 L7 的 class-map ,没有 type 则是用于是 L3/L4 的)
- 指定单条或多条匹配规则 (match/match not) ,或者如要匹配全部流量,也可以不写 match
- 创建 policy-map type ,类型要与 class-map 匹配
- policy-map 内部调用 class-map 并确定具体行为(drop/reset/log)
- 将 L7 policy-map 调用到 L3/L4 policy-map 的 inspect 语句后 ,因为 L7 策略是作为 L3/L4 流量监控的 附加参数
配置示例可以参考下面的【HTTP监控】。
5.3 应用场景
5.3.1 HTTP 监控
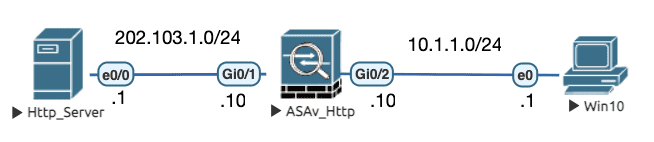
初始配置
需求:阻止访问 uri 含有 show/running-config 的请求
regex Regex_URI "show/running-config" ! class-map type inspect http match-all L7_HTTP_Class match request uri regex Regex_URI match request method get ! policy-map type inspect http L7_HTTP_Policy class L7_HTTP_Class reset log ! ! access-list ACL permit ip host 10.1.1.1 host 202.103.1.1 ! class-map L3_ACL_Class match access-list ACL ! policy-map L3_Policy class L3_ACL_Class inspect http L7_HTTP_Policy ! ! service-policy L3_Policy interface inside ! ! policy-map global_policy ! class inspection_default ! inspect http L7_HTTP_Policy ! ! ! !
5.3.2 监控管理流量
所谓的管理流量指的是目标地址是 ASA 的流量,而不是专指 Management 接口的流量。
type inspect 只针对穿越流量 ,无法控制抵达自身的流量。 type management 就是用于解决这个问题的。
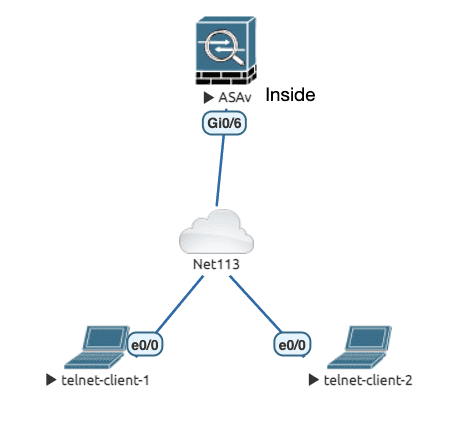
Figure 14: 实验拓扑(只放行一条管理连接)
初始配置
config
class-map type management Telnet_Class
match port tcp eq telnet
!
policy-map Telnet_Policy
class Telnet_Class
! max 1 conn, and 0 half-open conn
set connection conn-max 1 embryonic-conn-max 0
!
!
service-policy Telnet_Policy interface Inside
!
show
ASAv-HTTP(config)# sh service-policy interface inside
Interface Inside:
Service-policy: Telnet_Policy
Class-map: Telnet_Class
Set connection policy: conn-max 1
current embryonic conns 0, current conns 1, drop 8
5.3.3 DCD (dead connection detection)
ASA 向 TCP 两端发送 keepalive 报文,探测端点是否仍然存活,如端点无反应,则清除状态化表项。
access-list All_Tcp_ACL permit tcp any any ! class-map All_Tcp_Class match access-list All_Tcp_ACL ! policy-map global_policy class All_Tcp_Class ! idle 时长1小时,到期后进行 DCD ,DCD 消息(tcp keepalive)间隔5s,连发4次,4次都无响应则清除表项 set connection timeout idle 01:00:00 dcd 0:00:05 4 ! !
抓包:
100 20:06:31.515194 10.1.1.2 45922 202.103.1.1 23 TELNET 66 Telnet Data ... 101 20:06:31.722858 202.103.1.1 23 10.1.1.2 45922 TCP 54 23 → 45922 [ACK] Seq=54 Ack=49 Win=4080 Len=0 106 20:06:43.447874 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Keep-Alive] 23 → 45922 [ACK] Seq=53 Ack=49 Win=4080 Len=0 107 20:06:43.448930 10.1.1.2 45922 202.103.1.1 23 TCP 54 [TCP Keep-Alive ACK] 45922 → 23 [ACK] Seq=49 Ack=54 Win=64187 Len=0 108 20:06:43.451397 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Dup ACK 101#1] 23 → 45922 [ACK] Seq=54 Ack=49 Win=4080 Len=0 109 20:06:55.341083 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Keep-Alive] 23 → 45922 [ACK] Seq=53 Ack=49 Win=4080 Len=0 110 20:06:55.341874 10.1.1.2 45922 202.103.1.1 23 TCP 54 [TCP Keep-Alive ACK] 45922 → 23 [ACK] Seq=49 Ack=54 Win=64187 Len=0 111 20:06:55.343420 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Dup ACK 101#2] 23 → 45922 [ACK] Seq=54 Ack=49 Win=4080 Len=0 114 20:07:07.284477 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Keep-Alive] 23 → 45922 [ACK] Seq=53 Ack=49 Win=4080 Len=0 115 20:07:07.284791 10.1.1.2 45922 202.103.1.1 23 TCP 54 [TCP Keep-Alive ACK] 45922 → 23 [ACK] Seq=49 Ack=54 Win=64187 Len=0 116 20:07:07.286297 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Dup ACK 101#3] 23 → 45922 [ACK] Seq=54 Ack=49 Win=4080 Len=0 125 20:07:19.219359 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Keep-Alive] 23 → 45922 [ACK] Seq=53 Ack=49 Win=4080 Len=0 126 20:07:19.219752 10.1.1.2 45922 202.103.1.1 23 TCP 54 [TCP Keep-Alive ACK] 45922 → 23 [ACK] Seq=49 Ack=54 Win=64187 Len=0 127 20:07:19.221301 202.103.1.1 23 10.1.1.2 45922 TCP 54 [TCP Dup ACK 101#4] 23 → 45922 [ACK] Seq=54 Ack=49 Win=4080 Len=0
5.3.4 打开 TTL 递减功能
ASA 默认不会对穿越的流量修改 TTL ,因此 traceroute 时 ASA 相当于隐形,因此如果需要暴露 ASA ,可以手动开启 TTL 递减。
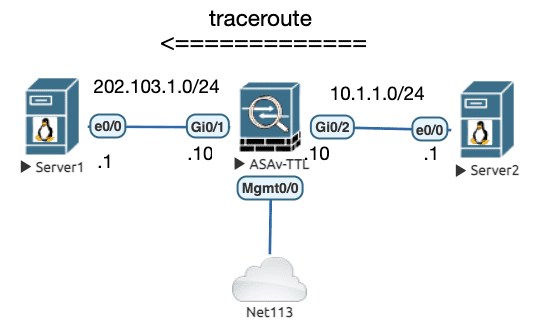
Figure 15: 实验拓扑
初始配置
! ################################################### ! # Before configuration # ! ################################################### Server2#traceroute ip 202.103.1.1 Type escape sequence to abort. Tracing the route to 202.103.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 202.103.1.1 4 msec 2 msec * Server2#
! ################################################### ! # Config decrement-ttl # ! ################################################### access-list Traceroute extended permit udp any any gt 33433 ! start from 33434 ! ISO use UDP to probe while Windows PC use ICMP class-map Traceroute-class-map match access-list Traceroute ! policy-map global_policy class Traceroute-class-map set connection decrement-ttl
! ###################################################
! # After configuration #
! ###################################################
Server2#traceroute ip 202.103.1.1
Type escape sequence to abort.
Tracing the route to 202.103.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 10.1.1.10 2 msec 5 msec *
2 202.103.1.1 4 msec 3 msec *
5.3.5 Inspect ESP (ipsec-pass-thru)
IPSEC 两个协商阶段是可以成功的,因为过程是基于 UDP 500 端口的。但是后续的数据是基于 IP 的,无法形成会话表,导致通信失败。
Branch#sh cry session detail Crypto session current status Interface: Tunnel0 Session status: UP-ACTIVE Peer: 202.103.1.1 port 500 Session ID: 0 IKEv1 SA: local 10.1.1.1/500 remote 202.103.1.1/500 Active IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 Active SAs: 2, origin: crypto map ! 协商成功,但是数据无法通信 Inbound: #pkts dec'ed 0 drop 0 life (KB/Sec) 4375619/3282 Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 4375619/3282
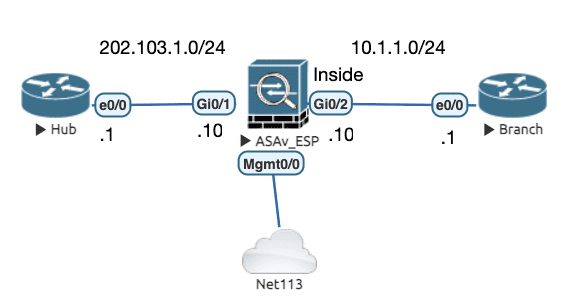
Figure 16: 实验配置
初始配置
! ################################################### ! # Enable ESP Inspection # ! ################################################### access-list ESP_ACL extended permit esp any any class-map ESP_CLASS_MAP match access-list ESP_ACL ! policy-map global_policy class ESP_CLASS_MAP inspect ipsec-pass-thru
5.3.5.1 途径有NAT设备的情况
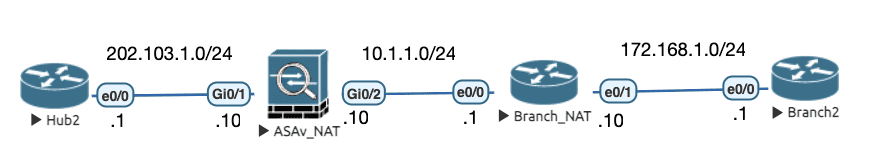
Figure 17: 实验拓扑
初始配置
Hub1 和 ASAv 的初始配置和上面的初始配置一样。
因为协商阶段可以检测出链路上存在 NAT ,因此不需要开启 ESP Inspection 也能通信。
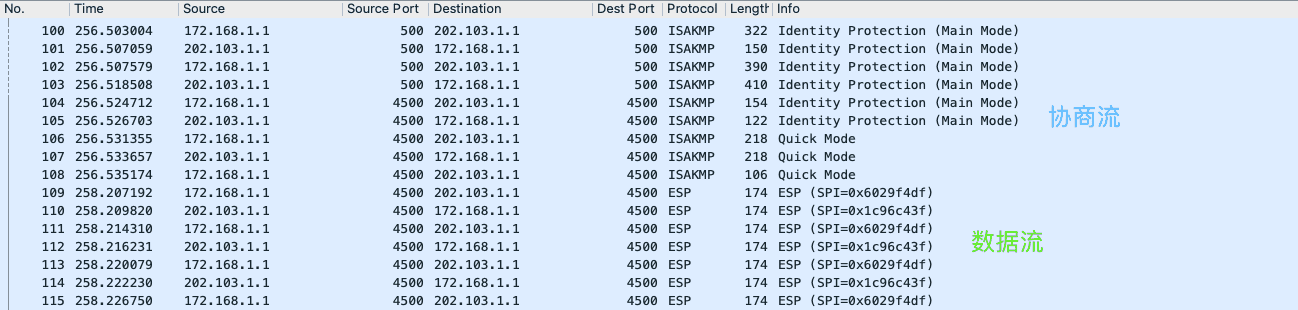
Figure 18: 协商流和数据流都是基于 UDP 的,默认会在 ASA 上建立会话表
5.3.6 关闭 TCP 序列号扰乱
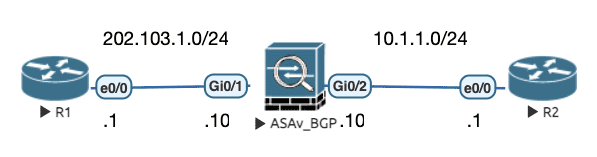
Figure 19: 实验拓扑( R1/R2 欲建立 BGP 邻居 )
初始配置
控制台会打印 %TCP-6-BADAUTH: Invalid MD5 digest from 202.103.1.1(14530) to 10.1.1.1(179) tableid - 0 ,这是因为 BGP 认证会将 TCP 序列号作为哈希运算的一个参数,而 ASA 默认会对 TCP 的序列号进行扰乱,因此需要认证的 BGP 邻居在跨越 ASA 时会协商失败。
! ################################################### ! # Disable random-seq for BGP # ! ################################################### class-map BGP_CLASS_MAP match port tcp eq bgp ! policy-map global_policy class BGP_CLASS_MAP set connection random-sequence-number disable ! !
更通用的配置:
access-list All_Tcp_ACL permit tcp any any ! class-map All_Tcp_Class match access-list All_Tcp_ACL ! policy-map global_policy class All_Tcp_Class set connection random-sequence-number disable ! !
5.3.7 tcp-state-bypass
- 在异步路由的环境中,默认情况下,当 ASA 收到一个无状态化表项 (connection) 的 inbound syn/ack TCP 包,直接丢包
- 出于安全目的,ASA 默认禁用 TCP option ,而某些协议需要使用 option (如 BGP ,其认证功能是基于 TCP option 实现的)
- ASA 默认会扰乱 TCP 序号,如应用程序需要检验 TCP 完整性,可能会收到影响
tcp-state-bypass 就是解决上述问题的,即直接绕开检查,放行流量。通常只应该 Bypass 可信的流量。
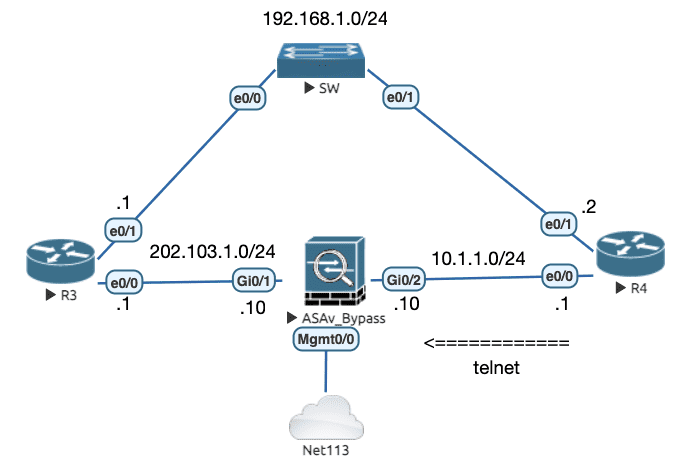
Figure 20: 实验拓扑( R4 所有流量都经过 ASA )
初始配置
尝试从 R3 telnet R4 (telnet 192.168.1.2) ,不成功,需要配置 tcp-state-bypass 放行 R4 -> R3 的 syn/ack :
! ################################################### ! # Bypass Configuration # ! ################################################### ! Define traffic first access-list Traffic_ACL permit ip host 192.168.1.2 host 192.168.1.1 class-map Bypass-Class match access-list Traffic_ACL ! policy-map global_policy class Bypass-Class set connection advanced-option tcp-state-bypass ! !
6 透明墙
只有在不希望重新规划现有网络 IP 地址的场景下,才需要使用到透明模式,其他场景,都推荐使用路由模式。
注意事项:
- ASA 模式切换前后,原有配置会丢失
- 使用透明墙模式, 必须要配置一个网管 IP ,否则只有非 IP 流量(如 ARP )可以通过,但是 网管 IP 不能够作为网关使用
- 如果有组播或广播流量,需要 明确 放行穿越
- 透明墙没有 STP 概念,因此每隔接口建议连接交换机不同的 VLAN
6.1 工作原理
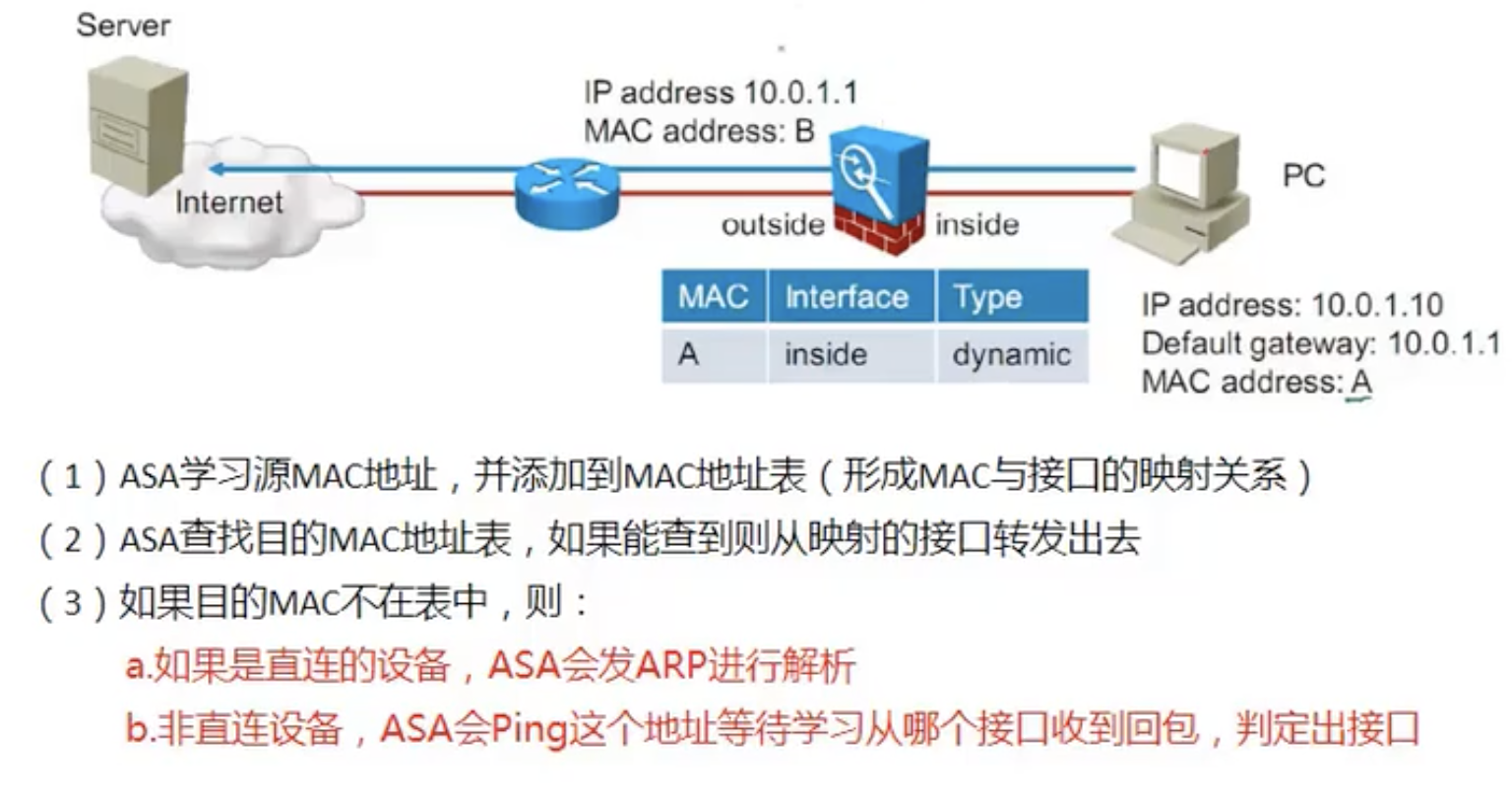
Figure 21: 注意:ping 的源是带内网管接口 BVI 的 IP 地址
上图中的(3)b. ,假设 PC 已知晓网关的 mac ,而防火墙却不知道(比如经历了重启,或 clear mac-address-table ),因此,问题变为了 已知目标 MAC ,但 ASA 无法从 mac-address-table 中获取 MAC 对应的接口信息 ,这种情况下,防火墙不会对 PC 发来的数据做未知单播泛洪(这是交换机的工作行为)。
如果目标地址和 BVI 是同一网段,则对每个接口发起 ARP 用以确定出口地址;
否则使用 ping 来确定出接口,ICMP 的源地址为 BVI , TTL 为 1 ,源 MAC 为 ASA MAC ,目的 MAC 为网关 MAC (就是收到的数据帧中的目标 MAC), 发向桥域中每个接口 (除了收到数据帧的入接口),正确的网关会回复 ICMP time-to-live exceeded ,ASA 由此就可以确定出接口。
这就是透明墙与交换机本质的不同,即透明墙为了防止信息泄露,原则上避免泛洪。
6.1.1 应用范例
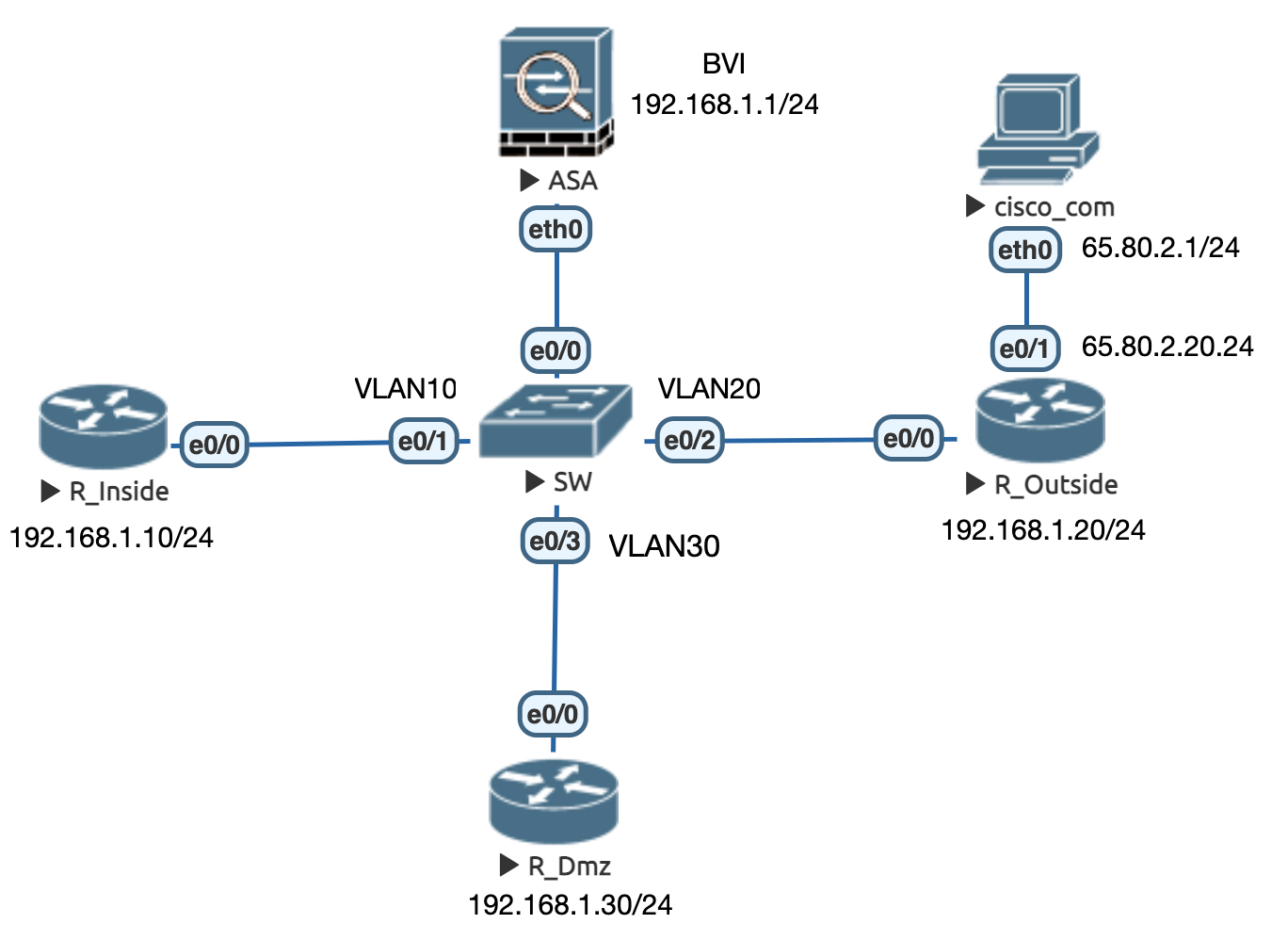
Figure 22: 物理拓扑
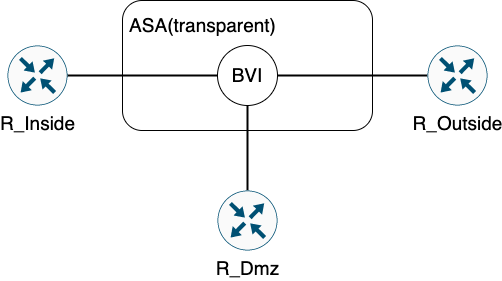
Figure 23: 逻辑拓扑
初始配置
! ################################################### ! # SW # ! ################################################### en conf t ip domain-name cisco.com hostname SW line con 0 exec-timeout 0 0 logging synchronous ! int e0/0 sw trunk encapsulation dot1q sw mo t sw trunk allowed vlan 10,20,30 spanning-tree portfast edge trunk ! int e0/1 sw mo ac sw ac vl 10 ! int e0/2 sw mo ac sw ac vl 20 ! int e0/3 sw mo ac sw ac vl 30 ! ! span portfast edge default ! ################################################### ! # R_Inside # ! ################################################### en terminal length 0 ! no pager conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname R_Inside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 192.168.1.10 255.255.255.0 no sh ! int lo0 ip add 1.1.1.1 255.255.255.255 no sh ! ip route 65.80.2.0 255.255.255.0 192.168.1.20 ! ! ################################################### ! # R_Outside # ! ################################################### en terminal length 0 ! no pager conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname R_Outside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 192.168.1.20 255.255.255.0 no sh ! int e0/1 ip add 65.80.2.20 255.255.255.0 no sh ! ! ################################################### ! # R_Dmz # ! ################################################### en terminal length 0 ! no pager conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname R_Dmz no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 192.168.1.30 255.255.255.0 no sh ! ! ################################################### ! # ASA # ! ################################################### firewall transparent int e0 no sh ! int e0.10 vlan 10 nameif Inside bridge-group 1 ! int e0.20 vlan 20 nameif Outside bridge-group 1 ! int e0.30 vlan 30 nameif DMZ bridge-group 1 ! int BVI1 ip add 192.168.1.1 255.255.255.0 ! policy-map global_policy class inspection_default inspect icmp ! ! send RESET back for TCP if inbound traffic is not allowed ! service resetinbound
当 R_Inside 访问 R_Ouside 时,ASA 会 在桥域范围内 转发 ARP (DMZ 也会收到 ARP 请求),并记录 MAC 与 桥域的关系:
ciscoasa# sh mac-address-table interface mac address type Age(min) bridge-group ----------------------------------------------------------------------------------- Inside aabb.cc03.3000 dynamic 5 1 Outside aabb.cc03.4000 dynamic 1 1
这样,当二层帧发到 ASA 后,ASA 就知道从哪个接口转发出去了。
注意,如果 ASA 不配置 BVI ,则数据无法访问,因为 ASA 收到数据时将无法得知是应该在桥域范围(同一网段)广播 ARP ,还是应该使用 ping 探测包(不同网段)。
假设此时在 ASA 上建立静态一对一 NAT ,将 R_Inside 上的 lo0 映射成 192.168.1.11 :
object network Static_1v1
host 1.1.1.1
nat (inside,outside) static 192.168.1.11
!
access-list My_ACL permit ip host 192.168.1.20 host 1.1.1.1
access-group My_ACL in interface outside
route inside 1.1.1.1 255.255.255.255 192.168.1.10
发现只有在 ASA 上配置了路由后,R_Outside 发向 192.168.1.11 的数据才能顺利通过。 这是因为当从 R_Outside 发往 192.168.1.11 的帧被截获后,ASA 依据 xlate 将目标地址转换回 1.1.1.1 ,之后仍是 基于三层路由的方式 通过查询路由表来确定下一跳出接口。(实际中有这种NAT的应用场景吗?)
ASA 上需要配置路由的场景基本上只有:
- 给 management 接口配置默认路由:route management 0 0 x.x.x.x
- 给带内管理地址配置路由:route inside x.x.x.x m.m.m.m <next-hop>
- 透明墙做 NAT (其实也就这个场景特殊点需要配路由)
- 自身发起流量
如果这时在 ASA 上清空 mac-address-table (cle mac-a) ,并从 R_Inside 上 ping 65.80.2.1 ,可以在 ASA e0 接口发现用于确定出接口的 ping 探测包:
! ASA 发向 outside (vlan tag 20) 37503 19:16:51.111244 192.168.1.1 65.80.2.1 ICMP 78 Echo (ping) request id=0x1124, seq=0/0, ttl=1 (no response found!) ! ASA 发向 dmz (vlan tag 30) 37504 19:16:51.112701 192.168.1.1 65.80.2.1 ICMP 78 Echo (ping) request id=0x1124, seq=0/0, ttl=1 (no response found!) ! 就 R_Outside 回复了,出接口也就得知了 37505 19:16:51.113294 192.168.1.30 192.168.1.1 ICMP 74 Time-to-live exceeded (Time to live exceeded in transit)
6.2 使用 Ethernet ACL 放行非 IP 流量
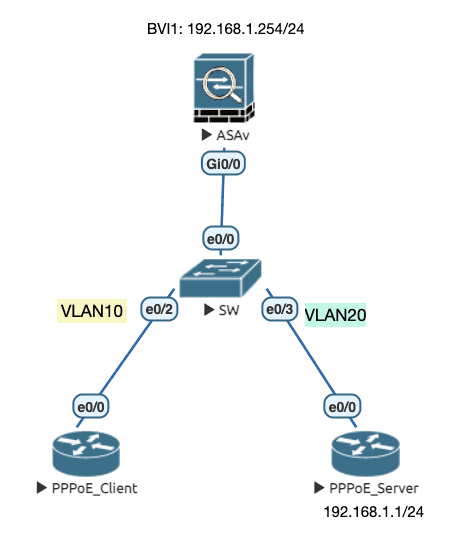
Figure 24: 实验拓扑
初始配置
ASA 默认不会放行非 IP 流量 (ARP 除外),因此需要配置 ACL 放行 承载 PPPoE 协议的以太网流量 :
! ###################################################
! # Allow PPPoE ACL #
! ###################################################
access-list Outside_ACL ethertype permit 8863
access-list Outside_ACL ethertype permit 8864
access-list Inside_ACL ethertype permit 8863
access-list Inside_ACL ethertype permit 8864
! 在双向接口入向调用
access-group Outside_ACL in interface Outside
access-group Inside_ACL in interface Inside
!
! ###################################################
! # Show PPPoE Session #
! ###################################################
PPPoE_Client#sh pppoe summary
1 client session
PPPoE_Client#sh pppoe se
PPPoE_Client#sh pppoe session
1 client session
Uniq ID PPPoE RemMAC Port VT VA State
SID LocMAC VA-st Type
N/A 2 aabb.cc00.7000 Et0/0 Di1 Vi1 UP
aabb.cc00.8000 UP
7 多模墙(Security Context) 4
7.1 概述
- 一个 ASA 可以划分出多个虚拟的防火墙,称为子墙 (Security Context)
- 每个子墙拥有自己的接口和安全策略
- 子墙之间可以共享物理接口(仅限路由模式,透明模式不能共享)
- 每个子墙有属于自己独立的 running-config
使用虚拟墙的场景:
- 多租户,为不同网络提供不同安全策略
- 为不同流量做隔离
- 需要部署 A/A Failover
限制:
- 所有子墙要么都是路由模式,要么都是透明模式 (9.0 后没有此限制)
- 多模透明墙不支持共享物理接口
- 使用共享接口时,需为每个子墙的共享接口指定不同 MAC 地址
7.2 配置步骤
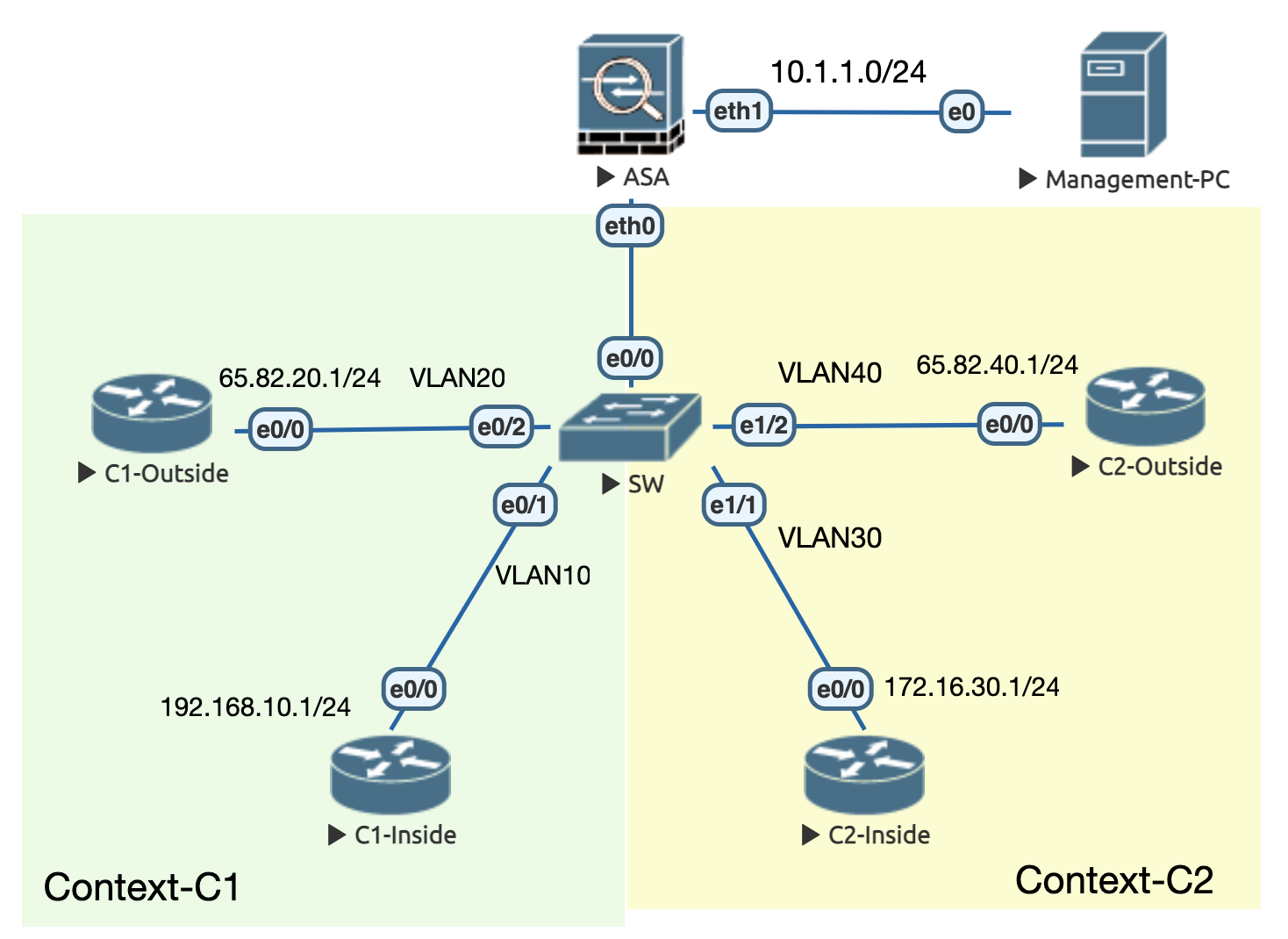
基础配置
! ################################################### ! # SW # ! ################################################### en conf t ip domain-name cisco.com hostname SW line con 0 exec-timeout 0 0 logging synchronous ! int e0/0 sw trunk encapsulation dot1q sw mo t sw trunk allowed vlan 10,20,30,40 spanning-tree portfast edge trunk ! int e0/1 sw mo ac sw ac vl 10 ! int e0/2 sw mo ac sw ac vl 20 ! int e1/1 sw mo ac sw ac vl 30 ! int e1/2 sw mo ac sw ac vl 40 ! ! ################################################### ! # C1-Inside # ! ################################################### en conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname C1-Inside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 192.168.10.1 255.255.255.0 no sh ! ip route 0.0.0.0 0.0.0.0 192.168.10.254 ! ! ################################################### ! # C1-Outside # ! ################################################### en conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname C1-Outside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 65.82.20.1 255.255.255.0 no sh ! ip route 192.168.10.0 255.255.255.0 65.82.20.254 ! ! ################################################### ! # C2-Inside # ! ################################################### en conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname C2-Inside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 172.16.30.1 255.255.255.0 no sh ! ip route 0.0.0.0 0.0.0.0 172.16.30.254 ! ! ################################################### ! # C2-Outside # ! ################################################### en conf t ip domain-name cisco.com alias exec ai sh ip int | in is.*up|Internet address|Secondary address alias exec ii sh ip int b | ex un alias exec i sh ip int b alias exec rr sh ip route | begin Gateway hostname C2-Outside no ip do lo line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 exec-timeout 0 0 logging synchronous transport input all login local ! username cisco priv 15 pass Cisco123 int e0/0 ip add 65.82.40.1 255.255.255.0 no sh ! ip route 172.16.30.0 255.255.255.0 65.82.40.254 !
7.2.1 切换模式
会备份原先的 running-config ,并 自动创建一个新的虚拟墙 (admin context ,主要用于登录后进行全局和子墙管理) ,此时的 系统全局配置只能做一些基本的配置,如创建 context ,给 context 关联接口 。
ciscoasa(config)# sh mode Security context mode: single ciscoasa(config)# mode multiple WARNING: This command will change the behavior of the device WARNING: This command will initiate a Reboot Proceed with change mode? [confirm] Convert the system configuration? [confirm] ! The old running configuration file will be written to flash Converting the configuration - this may take several minutes for a large configuration The admin context configuration will be written to flash The new running configuration file was written to flash Security context mode: multiple --- SHUTDOWN NOW --- ciscoasa# sh context Context Name Class Interfaces Mode URL *admin default Routed disk0:/admin.cfg Total active Security Contexts: 1 ciscoasa# sh int ip b Interface IP-Address OK? Method Status Protocol Ethernet0 unassigned YES unset administratively down up Ethernet1 unassigned YES unset administratively down up Ethernet2 unassigned YES unset administratively down up Ethernet3 unassigned YES unset administratively down up
7.2.2 配置 admin 子墙
- system 模式(系统全局)没有可以用于通信的接口,需要使用 admin context 和外界通信
- 用于远程登录后管理其他子墙,必须创建
- 可用于发送 syslog
changeto system int e1 no sh ! context admin allocate-int e1 iManagement ! changeto context admin int iManagement nameif management security-level 100 ip add 10.1.1.254 255.255.255.0 no sh ! telnet 0 0 management username cisco password Cisco123 aaa authentication telnet console LOCAL !
7.2.3 初始化虚拟防火墙
在系统配置中创建(子)接口
changeto system int e0 no sh ! int e0.10 vlan 10 ! int e0.20 vlan 20 ! int e0.30 vlan 30 ! int e0.40 vlan 40 !
新建 context 并分配接口
changeto sys context C1 config-url flash:/C1.cfg allocate-interface e0.10 iInside allocate-interface e0.20 iOutside ! context C2 config-url flash:/C2.cfg allocate-interface e0.30 iInside allocate-interface e0.40 iOutside !
配置子墙
changeto context C1 int iInside nameif Inside ip add 192.168.10.254 255.255.255.0 no sh ! int iOutside nameif Outside ip add 65.82.20.254 255.255.255.0 no sh ! !! changeto context C2 int iInside nameif Inside ip add 172.16.30.254 255.255.255.0 no sh ! int iOutside nameif Outside ip add 65.82.40.254 255.255.255.0 no sh !
7.3 共享接口的数据包归属问题
虽然路由模式下允许不同子墙共享一个物理接口,但 ASA 必须要能 判断出收到的数据包该分配到那个子墙处理 ,因此每个 进入的包 都必须先进行包分类,分类原则与顺序是:
- 唯一物理接口
- 唯一 MAC 地址
- 唯一 NAT global IP
假设子墙使用了共享接口,且公用了相同的 MAC (默认行为),也没有配置 NAT ,则数据包将被丢弃。
最常见的解决方案是配置 mac-address auto 。
7.3.1 基于 NAT 出口地址 (共享外部接口)
在共享外部接口的情况下,必须在每个子接口上配置 NAT ,这样回包才能找到正确的子墙进行处理,否则回包将会被丢弃。
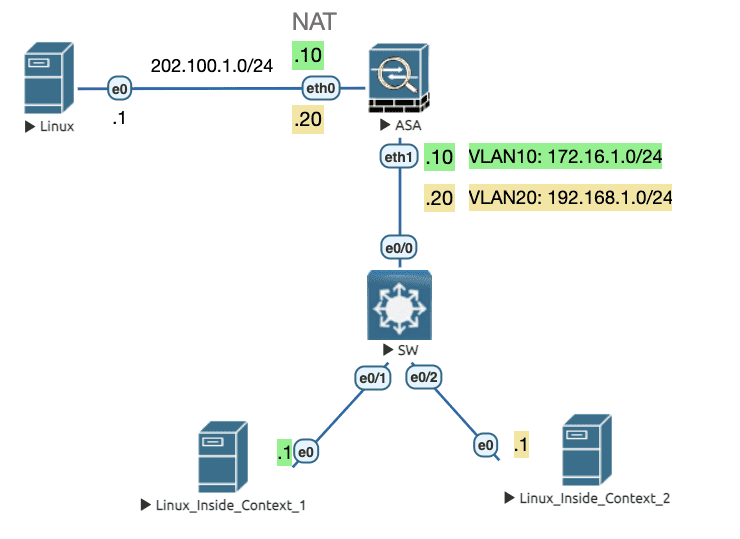
Figure 26: 实验拓扑
配置
7.3.2 基于接口(独立接口)
上面例子中的 e1.10 和 e1.20 相当于两个独立接口。
7.3.3 基于 MAC 地址 (共享内部接口)
必须为共享的内部接口在每一个子墙中设置不同的 MAC 地址。
在系统全局模式下使用 mac-address auto 为共享的接口在每个 context 中自动生成 MAC 地址。
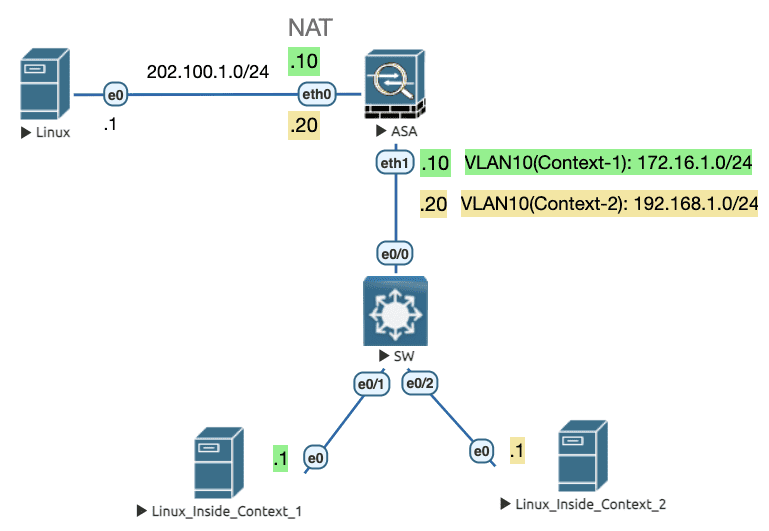
Figure 27: 实验拓扑
配置
! ###################################################
! # ASA (multiple mode) #
! ###################################################
hostname ASA
int e0
no sh
!
int e1
no sh
!
int e1.10
vlan 10
!
context Context-1
config-url flash:/context-1.cfg
allocate-interface e0
allocate-interface e1.10
!
context Context-2
config-url flash:/context-2.cfg
allocate-interface e0
allocate-interface e1.10
!
mac-address auto
!
changeto context Context-1
int e1.10
nameif Inside
ip add 172.16.1.10 255.255.255.0
no sh
!
int e0
nameif Outside
ip add 202.100.1.10 255.255.255.0
no sh
!
object network Inside_Network
subnet 172.16.1.0 255.255.255.0
nat (Inside,Outside) dynamic interface
!
policy-map global_policy
class inspection_default
inspect icmp
!
service resetinbound
!!!!!!!!!!!!!!!!!!!!!
changeto context Context-2
int e1.10
nameif Inside
ip add 192.168.1.20 255.255.255.0
no sh
!
int e0
nameif Outside
ip add 202.100.1.20 255.255.255.0
no sh
!
object network Inside_Network
subnet 192.168.1.0 255.255.255.0
nat (Inside,Outside) dynamic interface
!
policy-map global_policy
class inspection_default
inspect icmp
!
service resetinbound
!
! ################################################### ! # Check gateway mac # ! ################################################### root@Linux_Inside_Context_1:~# ip r default via 172.16.1.10 dev eth0 172.16.1.0/24 dev eth0 proto kernel scope link src 172.16.1.1 root@Linux_Inside_Context_1:~# ip n 172.16.1.10 dev eth0 lladdr a2:00:00:00:00:02 REACHABLE root@Linux_Inside_Context_2:~# ip r default via 192.168.1.20 dev eth0 192.168.1.0/24 dev eth0 proto kernel scope link src 192.168.1.1 root@Linux_Inside_Context_2:~# ip n 192.168.1.20 dev eth0 lladdr a2:00:00:00:00:06 REACHABLE
8 高可用技术
8.1 冗余接口
- 2 个物理接口( 只能2个 )可以捆绑起来使用,以提供接口级别的冗余,每个物理接口称为 member
- 其中一个物理接口为 主接口 ,其余为 备用接口 ,只有主接口执行转发工作
- 冗余接口的对端可以连接一台设备,也可以连接两台设备
- 当主接口发生故障,备用接口成为主接口,并向外发送 Gratuitous ARP , 目的是更新交换机的出接口 ,如下图所示
- 当故障接口恢复后, 不会抢占
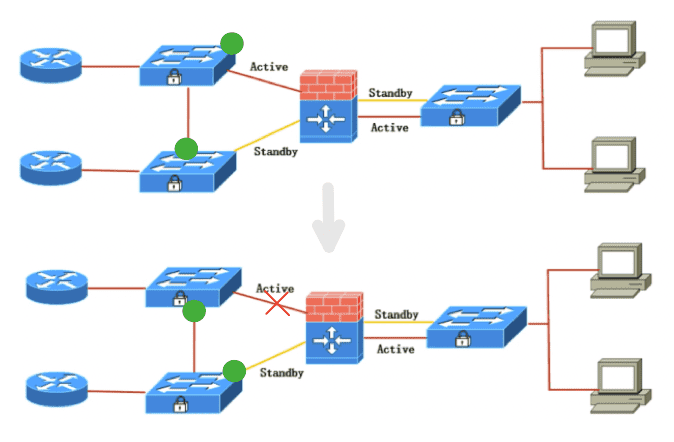
Figure 28: 使用 Gratuitous ARP 更新交换机出接口
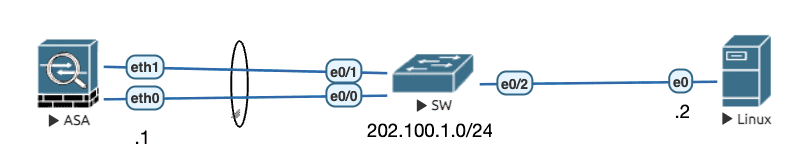
Figure 29: 实验拓扑
查看 ASA 冗余接口信息
ASA(config-if)# sh interface redundant 1
Interface Redundant1 "Outside", is up, line protocol is up
Hardware is i82559, BW 100 Mbps, DLY 100 usec
Auto-Duplex(Full-duplex), Auto-Speed(100 Mbps)
Input flow control is unsupported, output flow control is unsupported
MAC address 5000.0001.0000, MTU 1500
IP address 202.100.1.1, subnet mask 255.255.255.0
3 packets input, 13740 bytes, 0 no buffer
Received 41 broadcasts, 0 runts, 0 giants
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 pause input, 0 resume input
21 L2 decode drops
1 packets output, 64 bytes, 0 underruns
0 pause output, 0 resume output
0 output errors, 0 collisions, 0 interface resets
0 babbles, 0 late collisions, 0 deferred
0 lost carrier, 0 no carrier
0 input reset drops, 0 output reset drops
input queue (curr/max packets): hardware (0/2) software (0/41)
output queue (curr/max packets): hardware (0/3) software (0/1)
Traffic Statistics for "Outside":
20 packets input, 6560 bytes
1 packets output, 28 bytes
20 packets dropped
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 0 bytes/sec
5 minute output rate 0 pkts/sec, 0 bytes/sec
5 minute drop rate, 0 pkts/sec
Redundancy Information:
Member Ethernet0(Active), Ethernet1
Last switchover at 08:43:31 UTC Mar 27 2022
查看交换机 MAC 表项
Switch#sh mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0050.0000.0300 DYNAMIC Et0/2
1 5000.0001.0000 DYNAMIC Et0/0
Total Mac Addresses for this criterion: 2
将 ASA Ethernet0 口关闭后再次查看:
Switch#sh mac address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
1 0050.0000.0300 DYNAMIC Et0/2
1 5000.0001.0000 DYNAMIC Et0/1
Total Mac Addresses for this criterion: 2
8.2 聚合接口(EtherChannel)
- 所有物理成员接口都可以转发数据,起到了负载均衡的功能
- 聚合接口对端只能连接一台设备 (除非对端的多台设备可以使用特殊技术,如 Nexus VPC ,以形成一台逻辑设备)
8.3 Cluster
- 把多台 ASA 当成一台设备(逻辑上),一次增加吞吐量并提供冗余性
- 通过设定优先级决定 Master/Slave ,主备关系只是决定在哪台设备上进行配置, 备用设备也用于转发数据
- 只需要在 Master 上进行配置即可,会自动同步至 Slave 设备
- 每个设备需要使用一条或多条额外的链路用于控制管理
8.3.1 Spanned EtherChannel
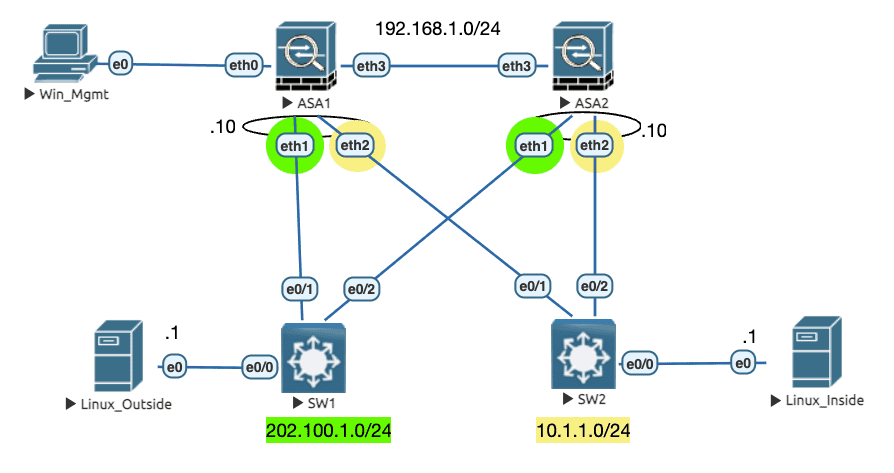
Figure 30: 实验拓扑
Cluster 配置
! ################################################### ! # ASA Master # ! ################################################### ! hostname will be synced between ASA hostname ASA-Cluster policy-map global_policy class inspection_default inspect icmp ! cluster interface-mode spanned int e3 no sh ! cluster group MyCluster local-unit unit1 priority 1 cluster-interface e3 ip 192.168.1.10 255.255.255.0 key Cisco123 enable Y !
! ################################################### ! # ASA Slave # ! ################################################### hostname ASA-Cluster policy-map global_policy class inspection_default inspect icmp ! cluster interface-mode spanned int e3 no sh ! cluster group MyCluster local-unit unit2 priority 10 cluster-interface e3 ip 192.168.1.20 255.255.255.0 key Cisco123 enable Y !
如果某个 ASA 意外 Disabled 了,被移除集群的话,重新加入下即可:
cluster group MyCluster enable !
如在当前的 Master ASA 上输入 cluster master unit <unit-name> 可以手动指定 Master 。
查看 Cluster 信息
ASA-Cluster(config)# sh cluster info
Cluster MyCluster: On
Interface mode: spanned
This is "unit1" in state MASTER
ID : 0
Version : 9.1(5)16
Serial No.: JMX1203L0NN
CCL IP : 192.168.1.10
CCL MAC : 5000.0001.0003
Last join : 14:47:46 UTC Mar 27 2022
Last leave: N/A
Other members in the cluster:
Unit "unit2" in state SLAVE
ID : 1
Version : 9.1(5)16
Serial No.: JMX1203L0NN
CCL IP : 192.168.1.20
CCL MAC : 5000.0002.0003
Last join : 14:48:10 UTC Mar 27 2022
Last leave: N/A
配置交换机 Etherchannel
! ################################################### ! # SW1 # ! ################################################### en conf t ip domain-name cisco.com hostname SW1 ! no ip do lo line con 0 exec-timeout 0 0 logging synchronous ! int r e0/1,e0/2 sw mo ac span portfast channel-group 1 mode active ! ! ################################################### ! # SW2 # ! ################################################### en conf t ip domain-name cisco.com hostname SW2 ! no ip do lo line con 0 exec-timeout 0 0 logging synchronous ! int r e0/1,e0/2 sw mo ac span portfast channel-group 1 mode active !
配置 Span Etherchannel
! ###################################################
! # ASA Master #
! ###################################################
int e1
channel-group 1 mode active
no sh
!
int e2
channel-group 2 mode active
no sh
!
int Po1
port-channel span-cluster
mac-address 1.1.1
nameif Outside
ip add 202.100.1.10 255.255.255.0
!
int Po2
port-channel span-cluster
mac-address 2.2.2
nameif Inside
ip add 10.1.1.10 255.255.255.0
!
测试连通性
! ################################################### ! # Linux Outside # ! ################################################### root@ubuntu:~# ip a add 202.100.1.1/24 dev eth0 root@ubuntu:~# ip r add default via 202.100.1.10 ! ################################################### ! # Linux Inside # ! ################################################### root@ubuntu:~# ip a add 10.1.1.1/24 dev eth0 root@ubuntu:~# ip r add default via 10.1.1.10 root@ubuntu:~# ping 202.100.1.1 PING 202.100.1.1 (202.100.1.1) 56(84) bytes of data. 64 bytes from 202.100.1.1: icmp_seq=48 ttl=64 time=2.30 ms 64 bytes from 202.100.1.1: icmp_seq=49 ttl=64 time=1.70 ms 64 bytes from 202.100.1.1: icmp_seq=50 ttl=64 time=1.75 ms
配置管理口
! ################################################### ! # ASA Master # ! ################################################### ip local pool Mgmt_Pool 172.16.1.2-172.16.1.10 int e0 management-only ip add 172.16.1.1 255.255.255.0 cluster-pool Mgmt_Pool nameif Mgmt no sh ! http server en http 0 0 Mgmt !
8.4 stateful FO 5
- 两个 ASA 在逻辑上当做一个单元来管理,只需在 Active 设备上进行配置,配置会自动复制到 Standby 设备 (通过 FO Link)
- 状态化表项等信息会在设备间同步 (通过 Stateful Link),FO Link 和 Stateful Link 可以各自使用独立的端口对,也可以共享一对物理接口
- 发生切换时,Standby 设备的所有接口(除了FO接口)会继承原先 Active 设备的配置,如 IP 和 MAC
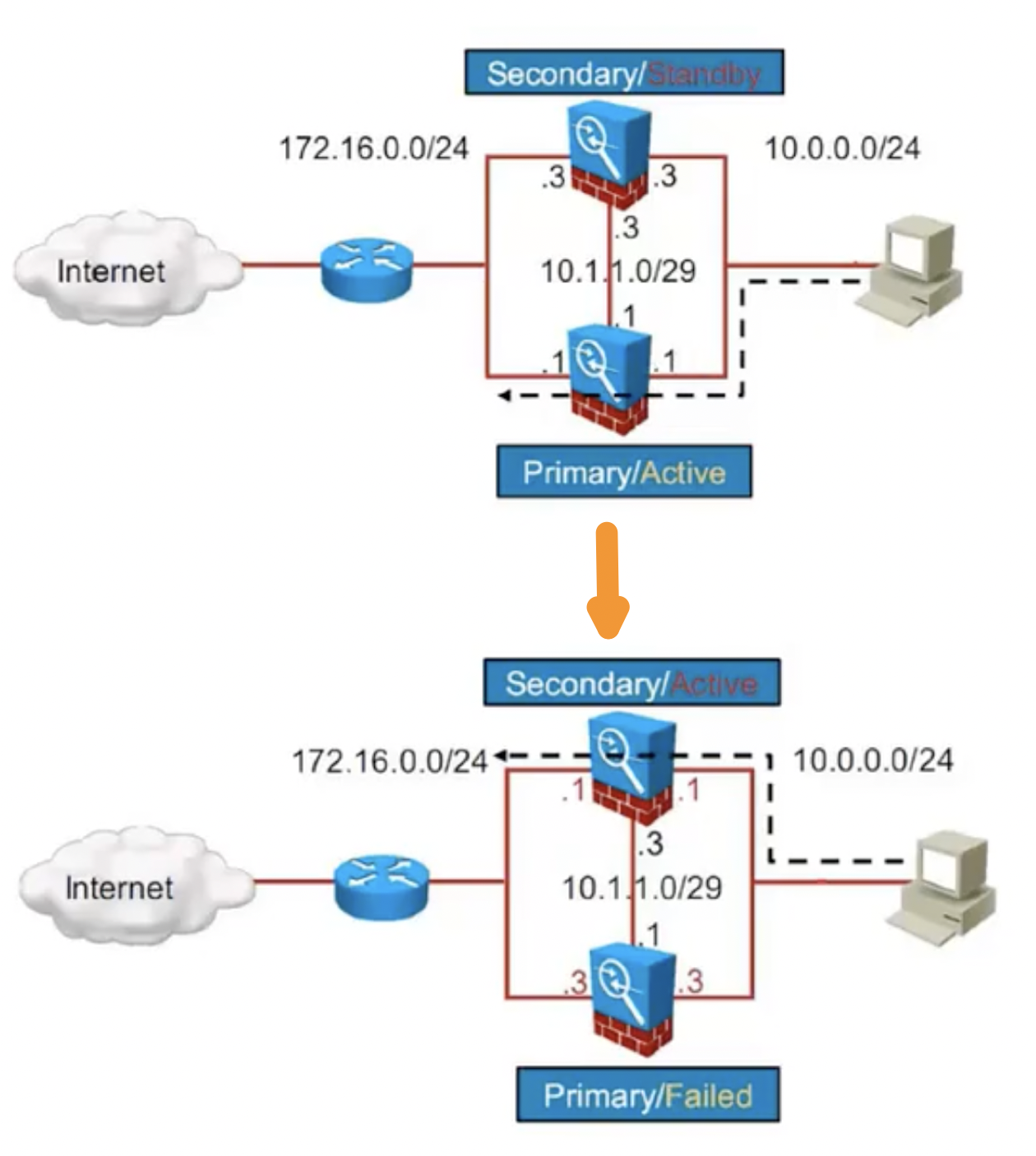
Figure 31: A/S 切换示意 【Standby 继承原 Active 设备的 IP 和 MAC (不包括 FO 接口)】
8.4.1 A/S FO 6
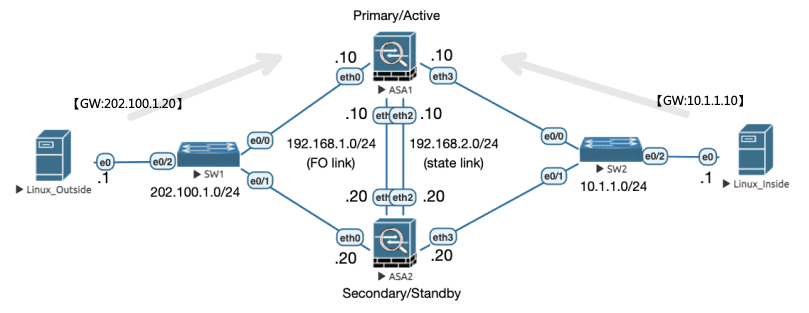
Figure 32: 实验拓扑
FO 接口的配置两个设备都要配置,其他的配置只在 Primary 上配置即可,会通过 FO 链路进行同步。
基础配置(仅 Primary)
! ################################################### ! # Primary # ! ################################################### hostname ASA no cluster interface-mode ! prompt will be like: ASA/pri/act prompt hostname priority state int e0 nameif Outside ! Need to specify standby ip here ip add 202.100.1.10 255.255.255.0 standby 202.100.1.20 no sh ! int e3 nameif Inside ip add 10.1.1.10 255.255.255.0 standby 10.1.1.20 no sh ! policy-map global_policy class inspection_default inspect icmp !
配置 State Link (仅 Primary)
int e2 no sh ! failover link State_Link e2 failover interface ip State_Link 192.168.2.10 255.255.255.0 standby 192.168.2.20 !
配置 FO Link (两个设备)
! ################################################### ! # Primary # ! ################################################### int e1 no sh ! failover lan unit primary failover lan int FO_Link e1 failover key Cisco123 failover interface ip FO_Link 192.168.1.10 255.255.255.0 standby 192.168.1.20 ! enable FO failover ! ! ################################################### ! # Secondary # ! ################################################### int e1 no sh ! failover lan unit secondary failover lan interface FO_Link e1 failover key Cisco123 failover interface ip FO_Link 192.168.1.10 255.255.255.0 standby 192.168.1.20 failover
Active 设备上的会话信息会自动同步到 Standby 设备上:
ASA/pri/act(config-if)# sh conn 9 in use, 12 most used TCP Outside 202.100.1.1:8080 Inside 10.1.1.1:35890, idle 0:00:03, bytes 11, flags UO ASA/sec/stby(config)# sh conn 8 in use, 13 most used TCP Outside 202.100.1.1:8080 Inside 10.1.1.1:35890, idle 0:00:08, bytes 0, flags U
8.4.2 A/A FO
- A/S FO 的问题在于只用 active 设备转发流量,不能充分利用设备资源。而使用一对 ASA 做成 A/A FO ,既可以实现设备级冗余,且都可以转发流量,实现负载分担
- A/A 本质上就是 两套交叉的 A/S
- A/A FO 必须用到多模墙,将两个子墙放进两个 failover group,每个group中包含一个active子墙和一个standby子墙,且这两个子墙分布在两个物理设备上
A/A 模式的 FO 特点在于两个设备可以 同时转发流量 ,配合路由器可实现负载均衡,如下图所示。
在这种模式中,需要使用虚拟子墙,为什么一定要用子墙,我的理解是,根据设计原则,一个 FO 组中的 Standby 设备必定是不转发流量的,如果使用物理设备的话,必然有一个处于待机状态,如 A/S FO 。而使用虚拟子墙的话,可以巧妙绕开这种限制,即将两个分布在不同物理设备上的虚拟子墙形成一个 FO 组,如果使用两个 FO 组,则可以实现每个物理设备上都能分到一个 Active 子墙,这样就能充分利用物理设备的资源,增加吞吐量。
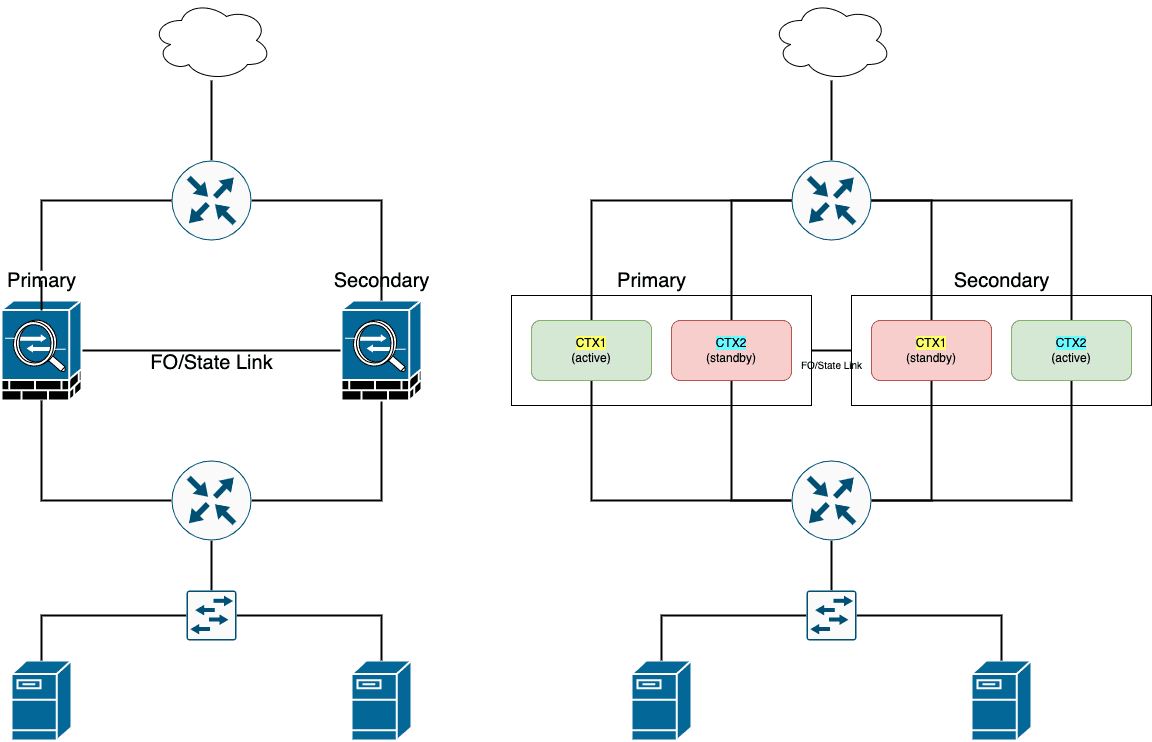
Figure 33: A/A FO 物理连接与逻辑连接
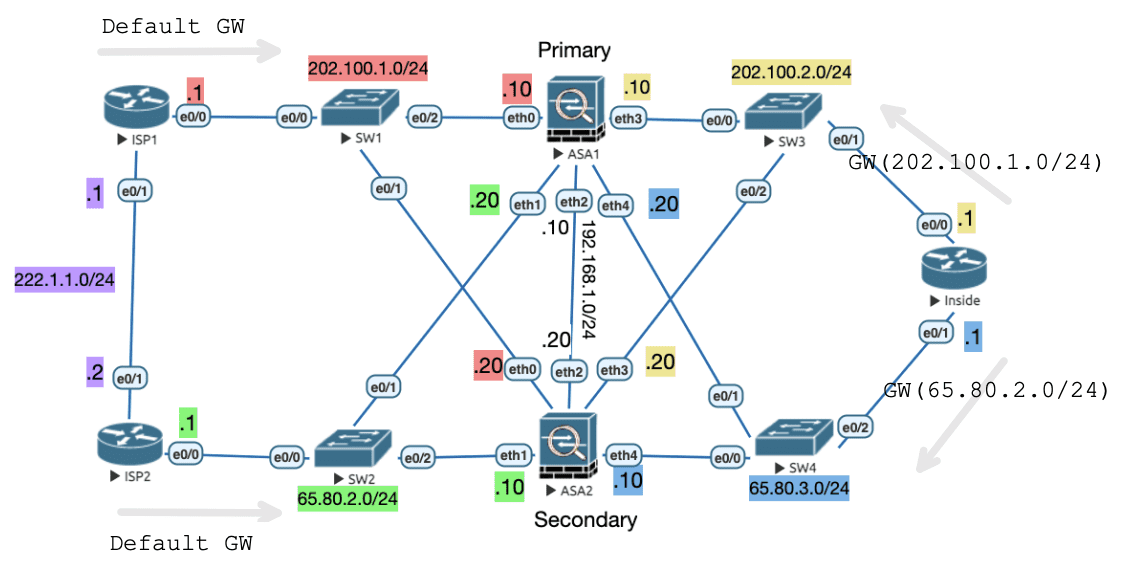
Figure 34: 实验物理拓扑 【模拟器如果 show 不出任何接口,尝试把 QEMU Nic 设置为 tpl(i82559er)】
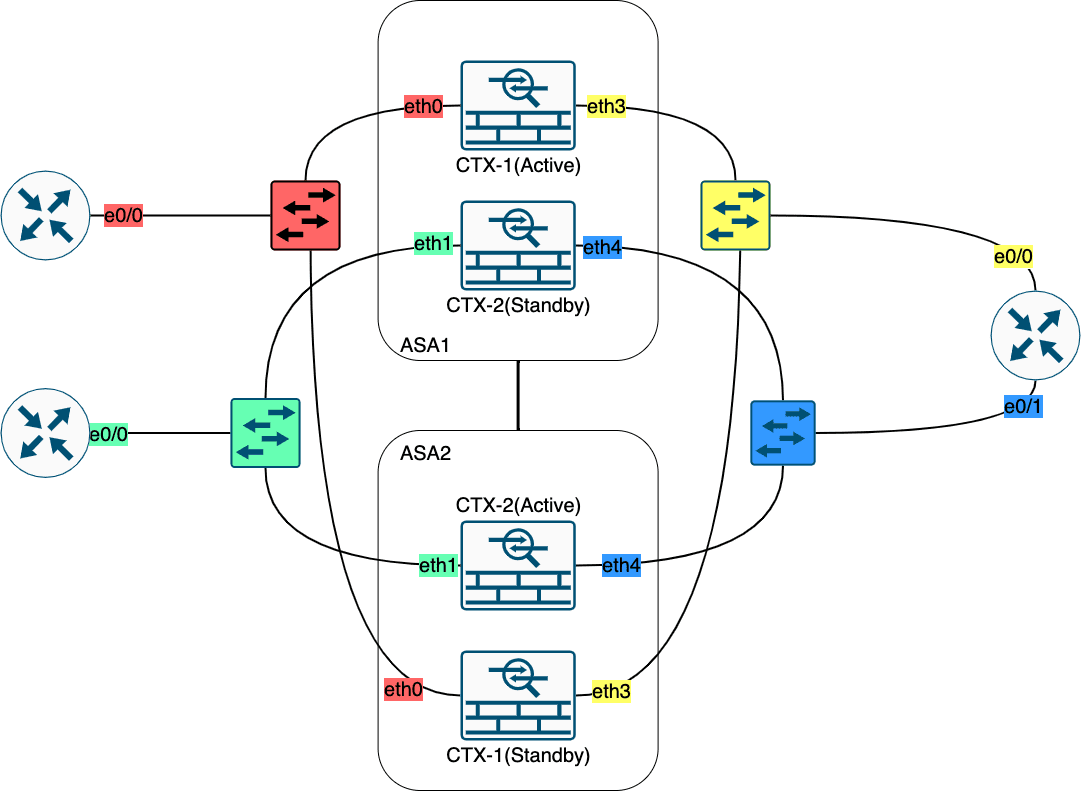
Figure 35: 实验逻辑拓扑
初始配置
以下是针对两个 ASA 的配置:(ASA 要确保处于多模式状态)
基础配置
! ################################################### ! # Primary # ! ################################################### hostname ASA prompt hostname priority state context int e0 no sh ! int e1 no sh ! int e2 no sh ! int e3 no sh ! int e4 no sh !
创建Context ,并划入相应的 FO 组
! ################################################### ! # Primary # ! ################################################### ! Create FO group first failover group 1 primary preempt ! failover group 2 secondary preempt ! ! Create Contexts context CTX-1 allocate-interface e0 allocate-interface e3 config-url disk0:/ctx-1.cfg join-failover-group 1 ! context CTX-2 allocate-interface e1 allocate-interface e4 config-url disk0:/ctx-2.cfg join-failover-group 2 !
初始化 Context
! ################################################### ! # Primary # ! ################################################### changeto context CTX-1 int e0 nameif Outside ip add 202.100.1.10 255.255.255.0 standby 202.100.1.20 ! int e3 nameif Inside ip add 202.100.2.10 255.255.255.0 standby 202.100.2.20 ! policy-map global_policy class inspection_default inspect icmp ! changeto context CTX-2 int e1 nameif Outside ip add 65.80.2.10 255.255.255.0 standby 65.80.2.20 ! int e4 nameif Inside ip add 65.80.3.10 255.255.255.0 standby 65.80.3.20 ! policy-map global_policy class inspection_default inspect icmp !
配置 FO/State 接口
! ################################################### ! # Primary (FO and State share the same link) # ! ################################################### changeto system ! failover lan unit primary failover lan interface FO/State e2 failover key Cisco123 failover link FO/State e2 failover interface ip FO/State 192.168.1.10 255.255.255.0 standby 192.168.1.20 failover
Secondary 上所需的配置
! ################################################### ! # Secondary # ! ################################################### int e2 no sh ! ! Setup FO group for secondary (seems have to define these before enable FO) failover group 1 secondary preempt ! failover group 2 primary preempt ! failover lan unit secondary failover lan interface FO/State e2 failover key Cisco123 failover link FO/State e2 failover interface ip FO/State 192.168.1.10 255.255.255.0 standby 192.168.1.20 failover
查看 Failover 状态信息
! ################################################### ! # Primary # ! ################################################### ASA/pri/act(config)# sh fail Failover On Failover unit Primary Failover LAN Interface: FO/State Ethernet2 (up) Unit Poll frequency 1 seconds, holdtime 15 seconds Interface Poll frequency 5 seconds, holdtime 25 seconds Interface Policy 1 Monitored Interfaces 4 of 60 maximum Version: Ours 9.1(5)16, Mate 9.1(5)16 Group 1 last failover at: 06:47:31 UTC Mar 30 2022 Group 2 last failover at: 06:47:40 UTC Mar 30 2022 This host: Primary Group 1 State: Active Active time: 1160 (sec) Group 2 State: Standby Ready Active time: 9 (sec) CTX-1 Interface Outside (202.100.1.10): Normal (Monitored) CTX-1 Interface Inside (202.100.2.10): Normal (Monitored) CTX-2 Interface Outside (65.80.2.20): Normal (Monitored) CTX-2 Interface Inside (65.80.3.20): Normal (Monitored) Other host: Secondary Group 1 State: Standby Ready Active time: 0 (sec) Group 2 State: Active Active time: 1080 (sec) CTX-1 Interface Outside (202.100.1.20): Normal (Monitored) CTX-1 Interface Inside (202.100.2.20): Normal (Monitored) CTX-2 Interface Outside (65.80.2.10): Normal (Monitored) CTX-2 Interface Inside (65.80.3.10): Normal (Monitored)
当创建一条 Inside <-> ISP1 的 TCP 时,可以看到 ASA/pri/act/CTX-1 上有一条会话记录,同时 ASA/pri/stby/CTX-1 上也记录了这个会话信息。
类似的,当创建一条 Inside <-> ISP2 的 TCP 时,可以看到 ASA/sec/act/CTX-2 上有一条会话记录,同时 ASA/pri/stby/CTX-2 记录了这个会话信息。
关闭 SW1/e/0/2 ,25s 后,在 ASA1 上可以看到 Active CTX-1 跑到了 ASA2 上:
ASA/pri/stby(config)# sh fail
Failover On
Failover unit Primary
Failover LAN Interface: FO/State Ethernet2 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
Interface Policy 1
Monitored Interfaces 4 of 60 maximum
Version: Ours 9.1(5)16, Mate 9.1(5)16
Group 1 last failover at: 08:51:11 UTC Mar 30 2022
Group 2 last failover at: 06:47:40 UTC Mar 30 2022
This host: Primary
Group 1 State: Failed
Active time: 7421 (sec)
Group 2 State: Standby Ready
Active time: 9 (sec)
CTX-1 Interface Outside (202.100.1.20): Failed (Waiting)
CTX-1 Interface Inside (202.100.2.20): Normal (Monitored)
CTX-2 Interface Outside (65.80.2.20): Normal (Monitored)
CTX-2 Interface Inside (65.80.3.20): Normal (Monitored)
Other host: Secondary
Group 1 State: Active
Active time: 78 (sec)
Group 2 State: Active
Active time: 7094 (sec)
CTX-1 Interface Outside (202.100.1.10): Normal (Waiting)
CTX-1 Interface Inside (202.100.2.10): Normal (Monitored)
CTX-2 Interface Outside (65.80.2.10): Normal (Monitored)
CTX-2 Interface Inside (65.80.3.10): Normal (Monitored)
ASA/pri/stby(config)# changeto context CTX-1
ASA/pri/stby/CTX-1(config)# sh fail
Failover On
Last Failover at: 08:51:11 UTC Mar 30 2022
This context: Failed
Active time: 7421 (sec)
Interface Outside (202.100.1.20): Failed (Waiting)
Interface Inside (202.100.2.20): Normal (Monitored)
Peer context: Active
Active time: 176 (sec)
Interface Outside (202.100.1.10): Normal (Waiting)
Interface Inside (202.100.2.10): Normal (Monitored)
打开交换机的端口后,一切又能恢复原状,这是配置 preempt 的效果。
8.4.2.1 异步路由组
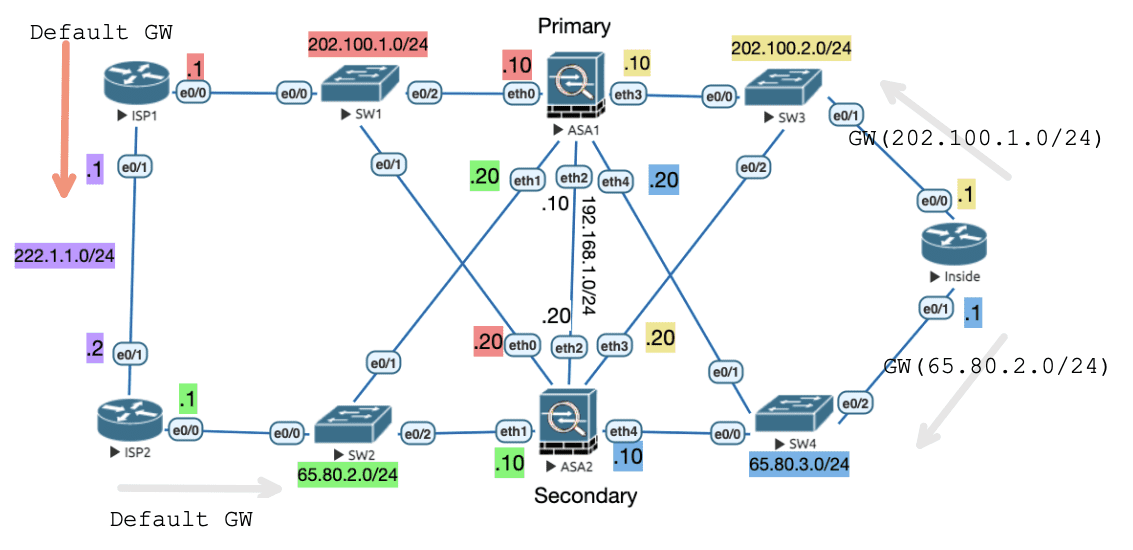
Figure 36: 异步路由环境(只是调整了 ISP1 的默认路由指向 ISP2 )
如上图所示,如果将 ISP1 的默认路由指向 ISP2 ,即 ip route 0.0.0.0 0.0.0.0 222.1.1.2 ,则由于出现了异步路由,ISP1 发往 Inside 的回包在到达 ASA2 时将被丢弃(因为 ASA2 上的 Active CTX-2 没有该连接的会话信息)。
需要配置异步路由组来解决这个问题,即把发生异步路由成员的接口指派到相同的 ASR 组中,效果是 ASA 会检查其他 FO 组(这里指的是 ASA2 上的 Standby CTX-1)的状态化表项,如果发现会话信息,则 修改二层信息 从而转发给正确的 ASA 进行转发。
! ################################################### ! # Active CTX-1 (ASA1) # ! ################################################### changeto context CTX-1 int e0 asr-group 1 ! ! ################################################### ! # Active CTX-2 (ASA2) # ! ################################################### changeto context CTX-2 int e1 asr-group 1 !
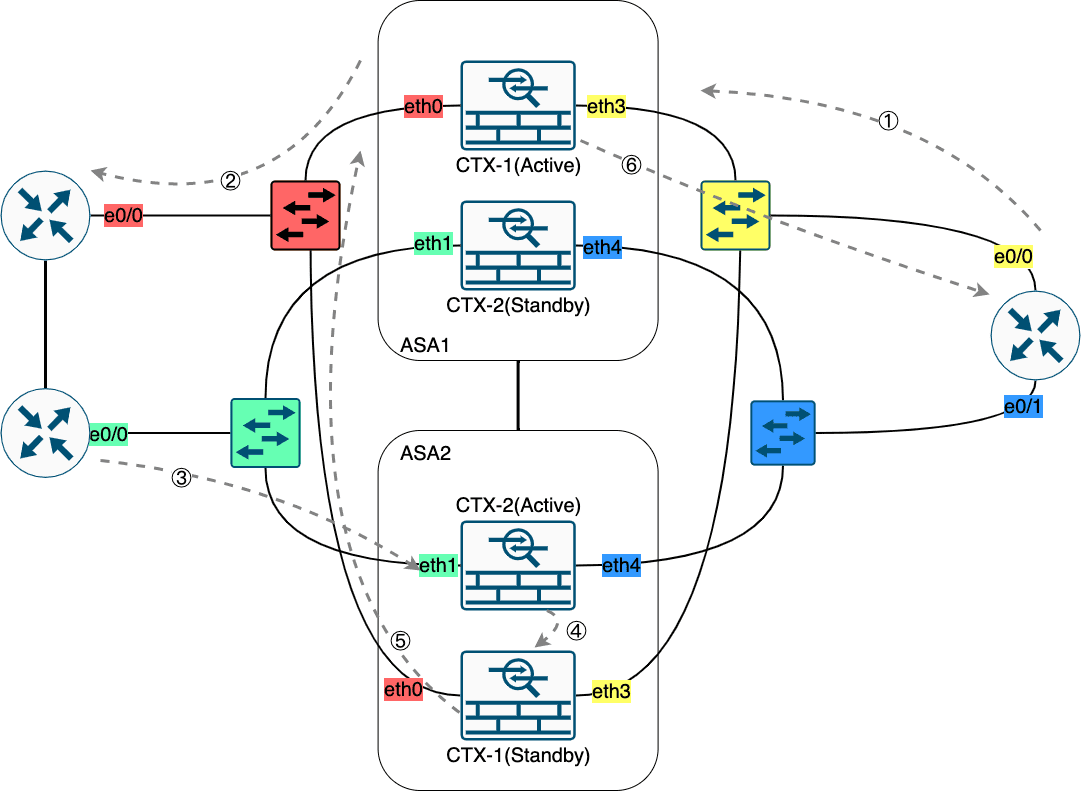
Figure 37: 实际数据通信流向
9 SSLVPN
9.1 Clientless Mode 【Layer 7】
该模式主要用于基于 Web 浏览器的内容提供。
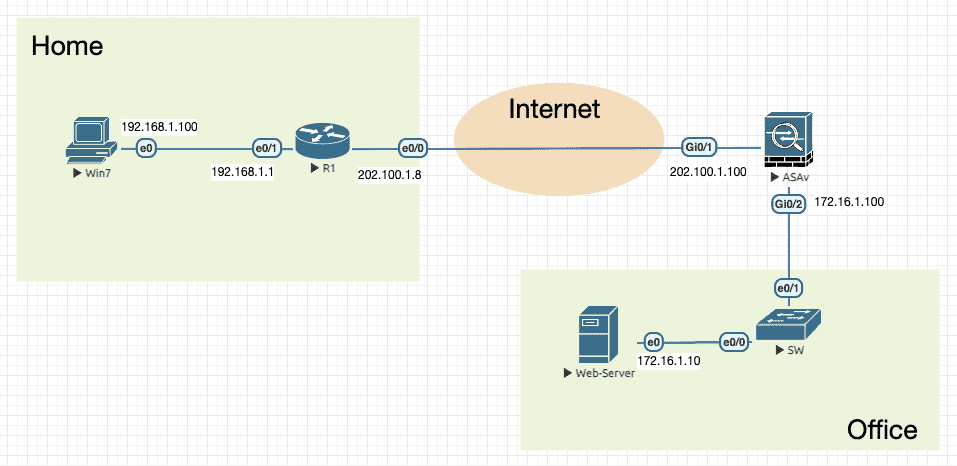
Figure 38: 实验拓扑(基本模型,现实中通常需要配置动态路由)
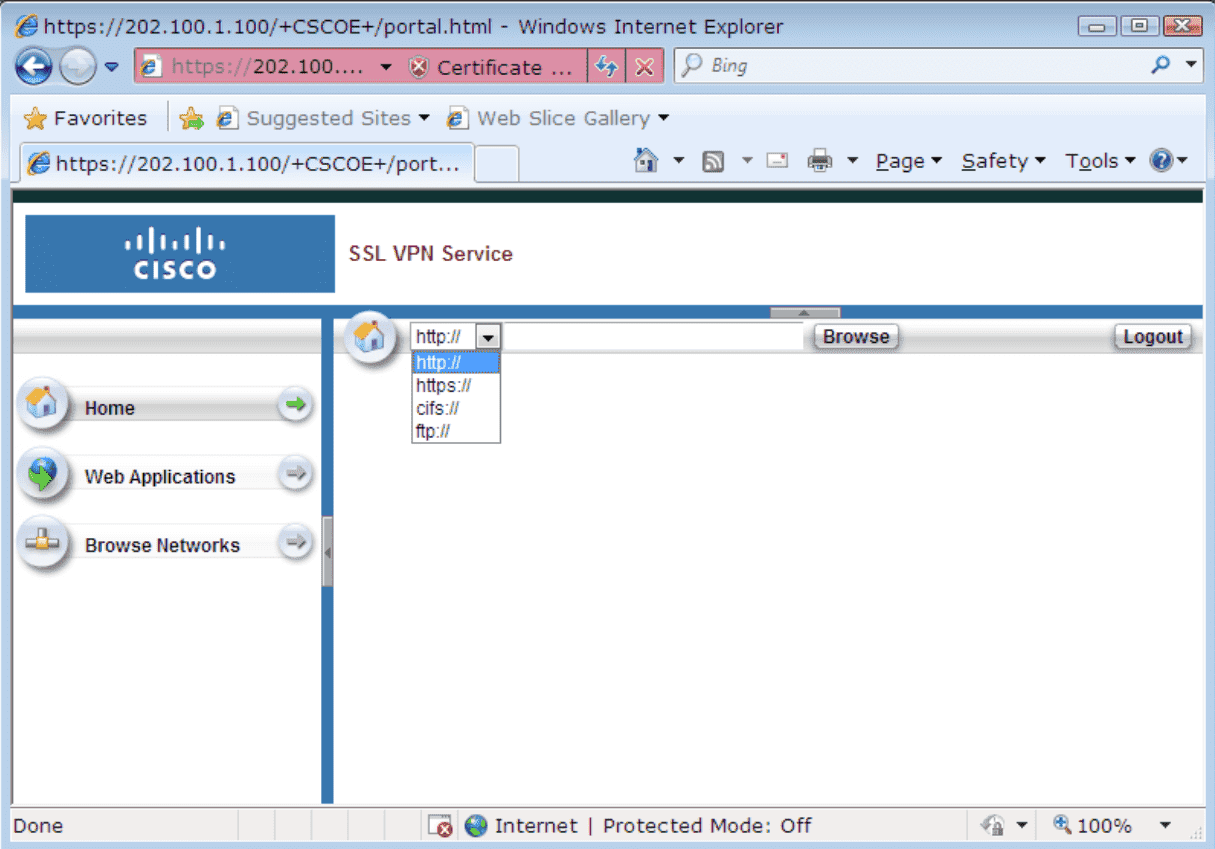
Figure 39: 使用界面【Win7】
9.2 Thin Client Mode 【Layer 7】
本质上是 本地端口转发 ,所谓的瘦客户端其实是 Java 程序。
实验拓扑与上一个模式相同。
! ################################################### ! # ASAv # ! ################################################### webvpn enable Outside port-forward Web-Server-PF 8080 172.16.1.10 8000 ! group-policy Thin-Group-Policy internal group-policy Thin-Group-Policy attributes webvpn port-forward enable Web-Server-PF ! ! username cisco password Cisco123 username cisco attributes vpn-group-policy Thin-Group-Policy !
需要先设置下Java安全策略
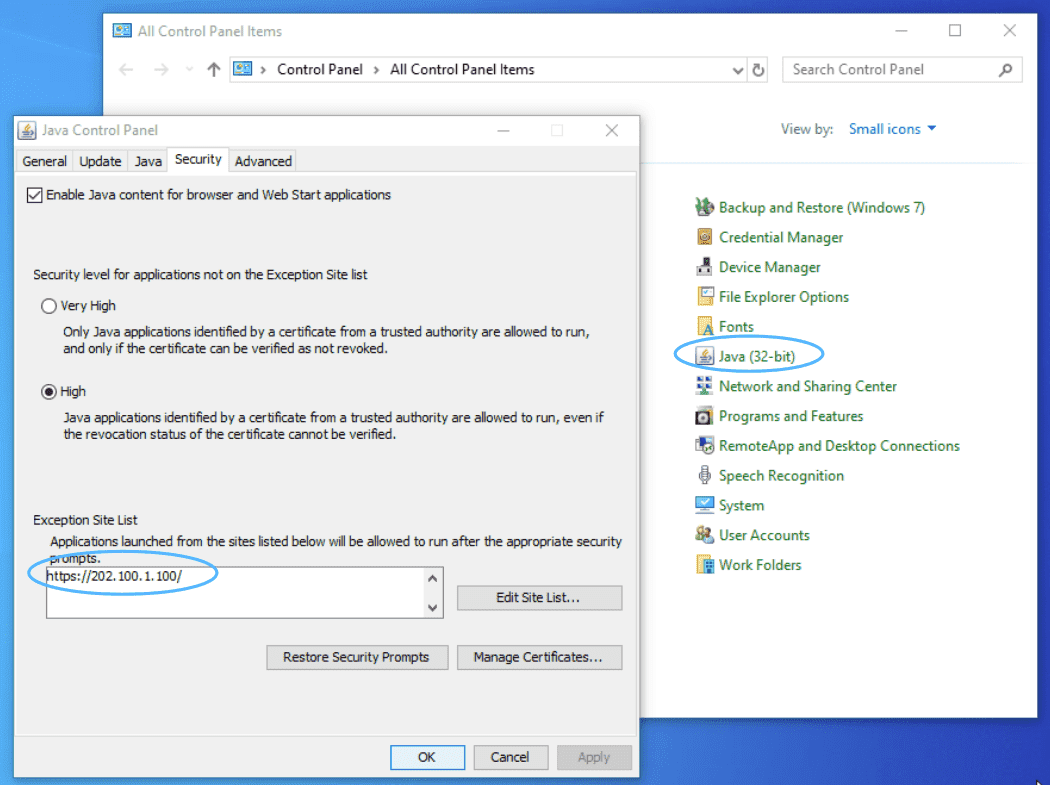
设置完后可能需要关闭浏览器重新登录。
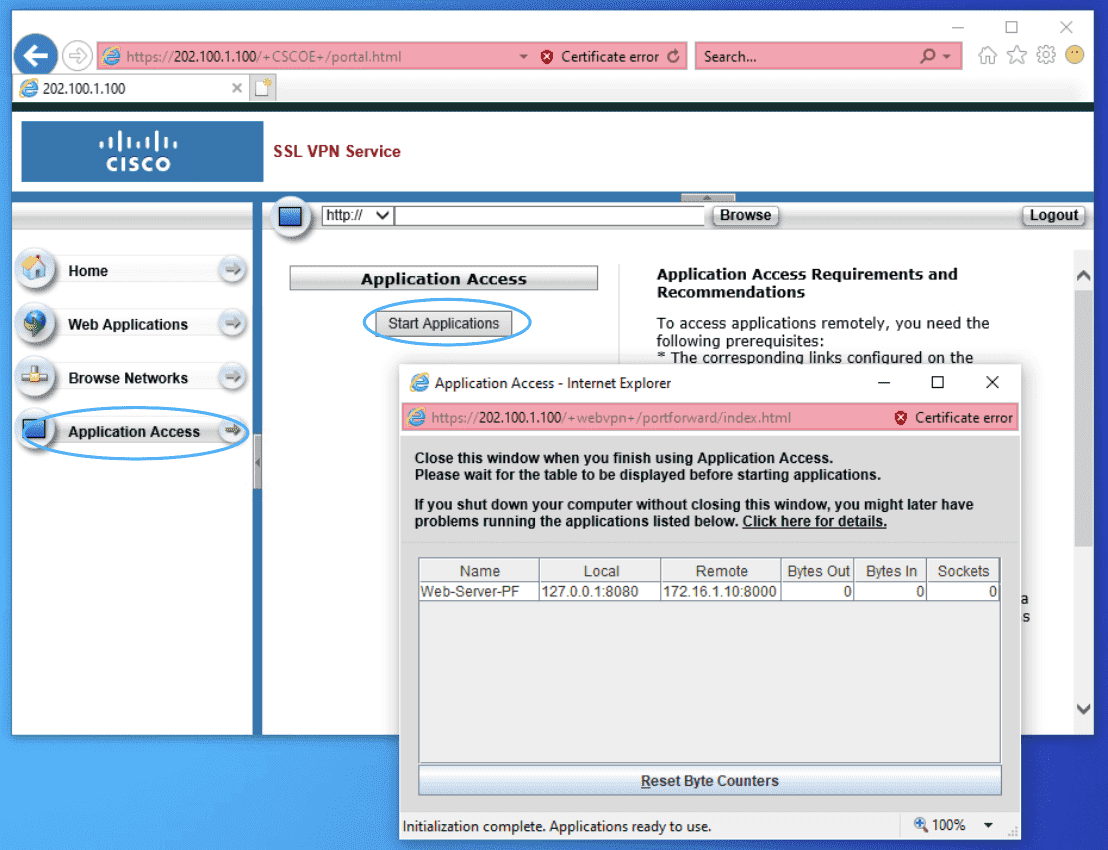
Figure 41: 使用界面【Win10】
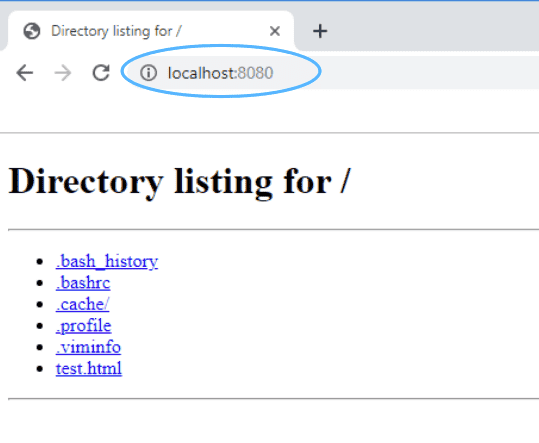
Figure 42: 访问本地端口
9.3 Thick Client Mode 【Layer 3】
! ################################################### ! # ASAv # ! ################################################### ip local pool SSLVPN-POOL 10.74.68.100-10.74.68.150 ! webvpn enable Outside anyconnect image disk0:/anyconnect-win-4.4.00243-webdeploy-k9.pkg anyconnect enable ! group-policy Thick-Group-Policy internal group-policy Thick-Group-Policy attributes vpn-tunnel-protocol ssl-client ssl-clientless address-pools value SSLVPN-POOL ! username cisco password Cisco123 username cisco attributes vpn-group-policy Thick-Group-Policy !
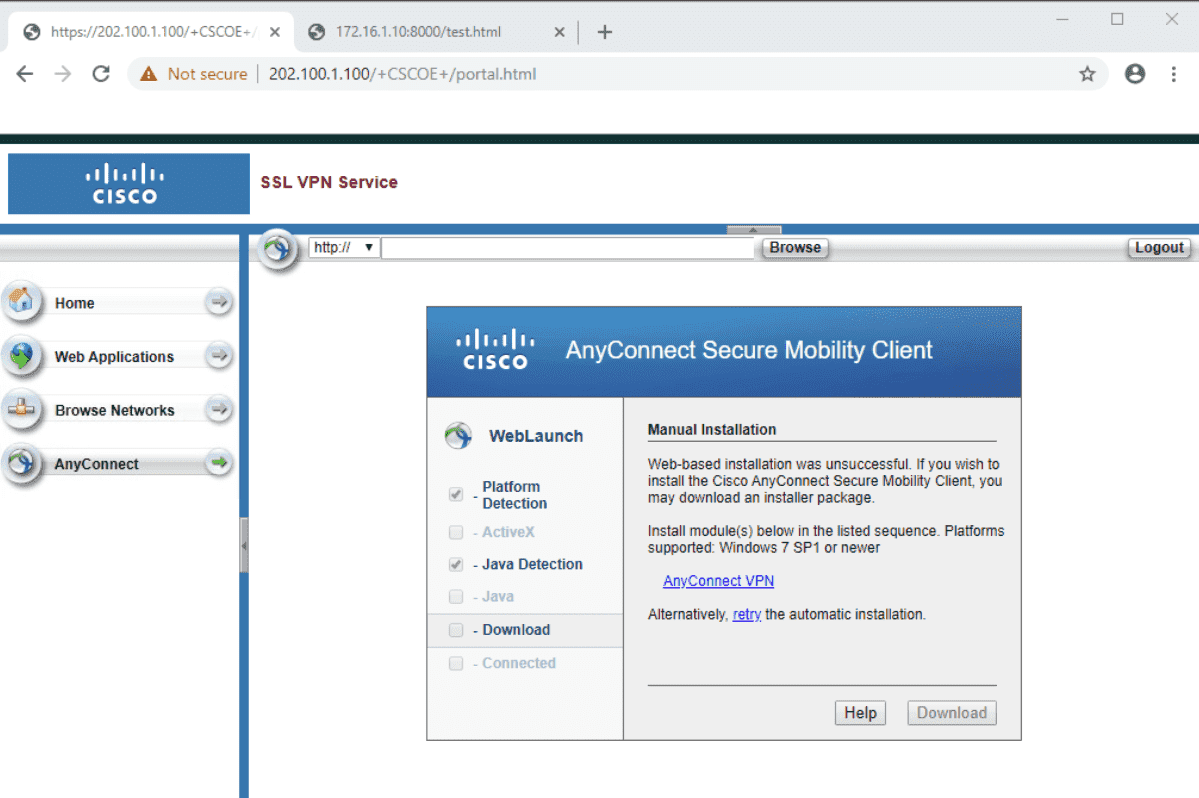
Figure 43: Anyconnect 下载界面
! ###################################################
! # show route on ASAv #
! ###################################################
ASAv(config)# sh route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is not set
! 10.74.68.100 是分配给客户端的地址,这里 ASA 动态添加了一条回程路由
S 10.74.68.100 255.255.255.255 [1/0] via 202.100.1.8, Outside
C 172.16.1.0 255.255.255.0 is directly connected, Inside
L 172.16.1.100 255.255.255.255 is directly connected, Inside
C 202.100.1.0 255.255.255.0 is directly connected, Outside
L 202.100.1.100 255.255.255.255 is directly connected, Outside
10 特性
10.1 uRPF
用于抵御 IP 地址欺骗,uRPF 分为严格和宽松模式,严格模式指的是当收到一个数据包时,ASA 上必须要有去往源 IP 的路由,且路由出接口与收到数据包的接口一致。而宽松模式只需要有去往源 IP 的路由即可。ASA 只支持严格模式。
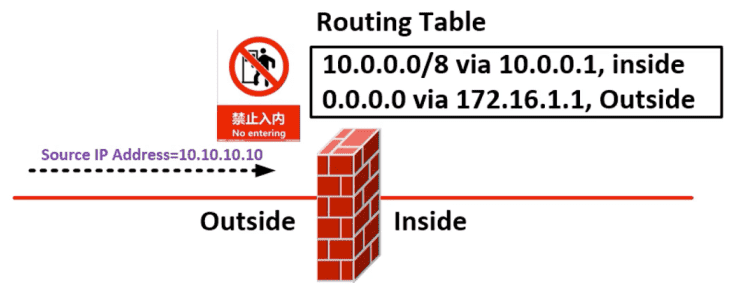
Figure 44: 原理示意
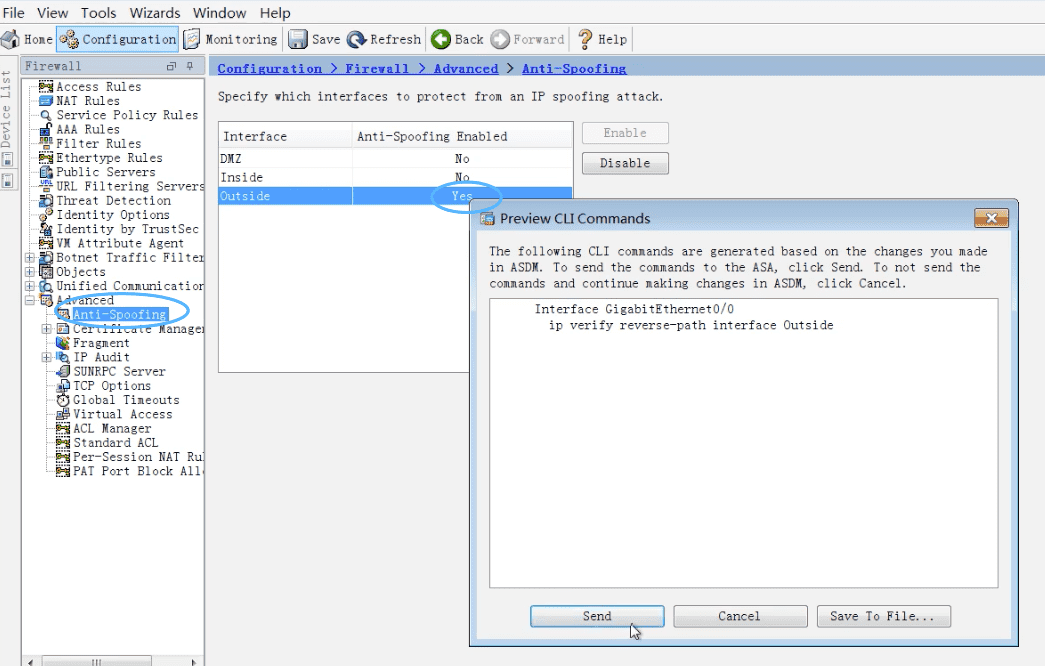
Figure 45: ASDM 配置
10.2 Shunning
用于丢弃源自于特征主机的数据包,可以与 IPS 联动用来动态阻止某些恶意流量。
ACL 是针对 初始流量 的,当会话表建立后就无法使用 ACL 阻止流量,这时可以手动配置 Shunning 来清除会话。
Shunning 优先于接口上的 ACL 规则,但在 ASA 重启后就无效了。
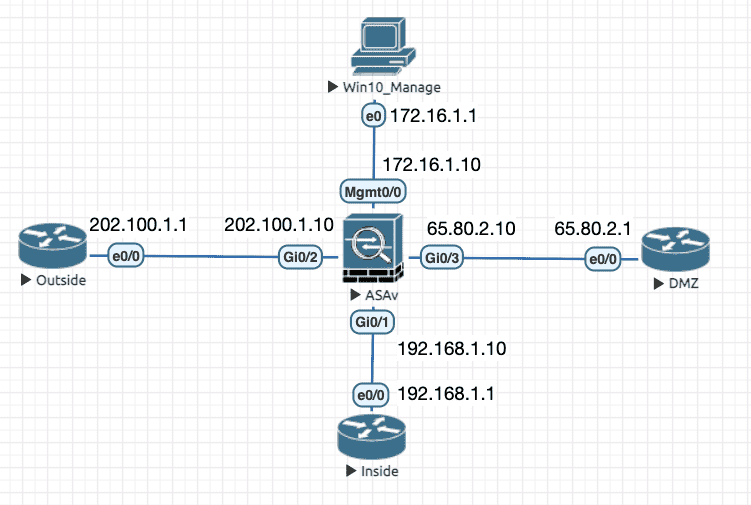
Figure 46: 实验拓扑
初始配置
先从 Inside telnet DMZ 建立 session :
! ################################################### ! # Cut session # ! ################################################### ASAv(config)# sh conn 1 in use, 1 most used TCP Outside 202.100.1.1:23 Inside 192.168.1.1:41564, idle 0:00:07, bytes 143, flags UIO ASAv(config)# shun 202.100.1.1 Shun 202.100.1.1 added in context: single_vf Shun 202.100.1.1 successful ASAv(config)# sh conn 0 in use, 1 most used ! session 已被踢掉 ASAv(config)# sh shun ! 查看 shun 状态 shun (Outside) 202.100.1.1 0.0.0.0 0 0 0 ASAv(config)# sh shun statistics Manage=OFF, cnt=0 Inside=OFF, cnt=0 Outside=ON, cnt=0 DMZ=OFF, cnt=0 ASAv(config)# clear shun ASAv(config)# sh shun statistics Manage=OFF, cnt=0 Inside=OFF, cnt=0 Outside=OFF, cnt=0 DMZ=OFF, cnt=0
10.3 Traffic Zone
没有 Zone ,ASA 无法解决负载均衡和异步路由问题。
Zone 是一系列接口的集合 ,ASA 可以将多个接口划分到一个 Zone 。
这样流量可以在 Zone 内的任何一个接口进入或者离开,以实现 Equal-Cost Multi-Path (ECMP) 和多接口负载均衡。
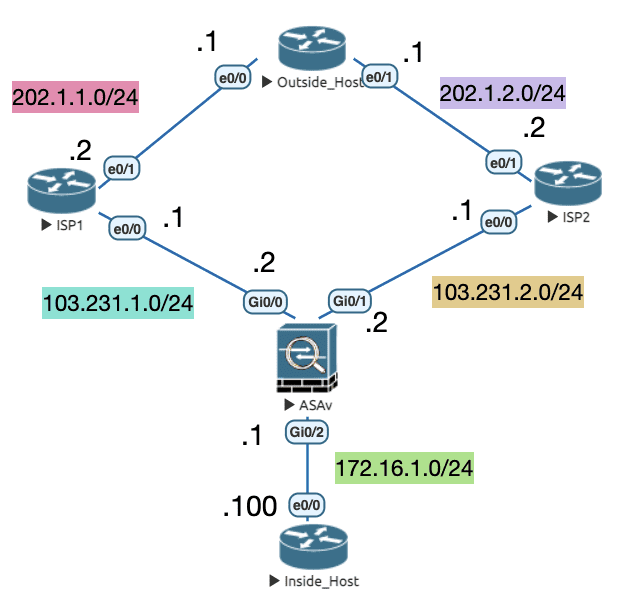
Figure 47: 实验拓扑
初始配置
! ###################################################
! # Create Zone #
! ###################################################
zone MY-ZONE
int gi0/0
zone-member MY-ZONE
!
! static routes attached to the interface will be removed due to zone changes, so reapply it
route Outside-ISP1 202.1.1.0 255.255.255.0 103.231.1.1 1
int gi0/1
zone-member MY-ZONE
!
route Outside-ISP2 202.1.2.0 255.255.255.0 103.231.2.1 1
! ################################################### ! # Show Zone Info # ! ################################################### ASAv(config)# sh zone Zone: MY-ZONE Security-level: 0 Zone member(s): 2 Outside-ISP2 GigabitEthernet0/1 Outside-ISP1 GigabitEthernet0/0 ASAv(config)# show nameif zone Interface Name Zone Name Security GigabitEthernet0/0 Outside-ISP1 MY-ZONE 0 GigabitEthernet0/1 Outside-ISP2 MY-ZONE 0 GigabitEthernet0/2 Inside 100 ASAv(config)# sh conn zone 1 in use, 1 most used TCP MY-ZONE:Outside-ISP1(Outside-ISP1) 202.1.1.1:23 Inside 172.16.1.100:14177, idle 0:00:03, bytes 99, flags UIO ! telnet session
11 技术联动
11.1 VxLAN
ASA 可以作为 VxLAN 的 NVE ,三层墙和二层墙都可以部署 VxLAN 。
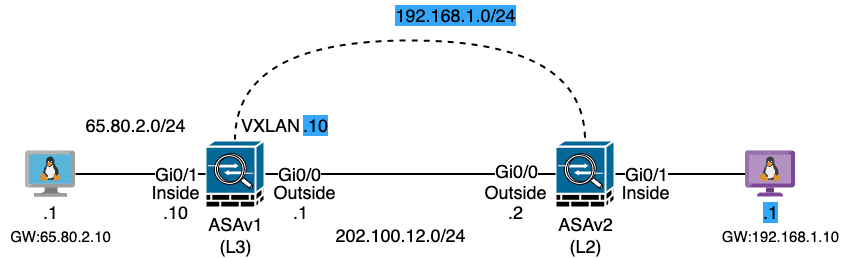
Figure 48: 实验拓扑
! ####################### ASAv1 ####################### hostname ASAv1 policy-map global_policy class inspection_default inspect icmp ! int gi0/1 nameif Inside ip add 65.80.2.10 255.255.255.0 no sh ! int gi0/0 nameif Outside ip add 202.100.12.1 255.255.255.0 no sh ! ! ----------------- VxLAN ----------------- ! ARP is sent through multicast multicast-routing nve 1 encapsulation vxlan source-interface Outside ! define mcast address for all vni under the nve default-mcast-group 224.0.0.1 ! interface vni 1 segment-id 6000 nameif VXLAN security-level 50 ip add 192.168.1.10 255.255.255.0 vtep-nve 1 ! access-list VXLAN_ACL extended permit ip any any access-group VXLAN_ACL in interface VXLAN !
! ####################### ASAv2 ####################### firewall transparent hostname ASAv2 policy-map global_policy class inspection_default inspect icmp ! int gi0/1 nameif Inside bridge-group 1 no sh ! must have BVI for L2 ASA, though this ifc is of no use here int BVI1 ip add 192.168.1.100 255.255.255.0 ! ! ----------------- VxLAN ----------------- int gi0/0 ! cannot config IP for ifc without this line nve-only nameif Outside ip add 202.100.12.2 255.255.255.0 no sh ! nve 1 encapsulation vxlan source-interface Outside ! int vni 1 segment-id 6000 nameif VXLAN bridge-group 1 security-level 50 vtep-nve 1 ! define mcast address only for this vni mcast-group 224.0.0.1 ! access-list VXLAN_ACL extended permit ip any any access-group VXLAN_ACL in interface VXLAN !
PCAP (ARP over VxLAN)
=> Who has 192.168.1.10? Tell 192.168.1.1 Frame 48: 110 bytes on wire (880 bits), 110 bytes captured (880 bits) on interface -, id 0 Ethernet II, Src: 50:00:00:06:00:01 (50:00:00:06:00:01), Dst: IPv4mcast_01 (01:00:5e:00:00:01) Internet Protocol Version 4, Src: 202.100.12.2, Dst: 224.0.0.1 请求用组播 User Datagram Protocol, Src Port: 60684, Dst Port: 4789 Virtual eXtensible Local Area Network Flags: 0x0800, VXLAN Network ID (VNI) Group Policy ID: 0 VXLAN Network Identifier (VNI): 6000 Reserved: 0 Ethernet II, Src: NexoComm_00:04:00 (00:50:00:00:04:00), Dst: Broadcast (ff:ff:ff:ff:ff:ff) Address Resolution Protocol (request) <= 192.168.1.10 is at 50:00:00:05:00:01 Frame 49: 92 bytes on wire (736 bits), 92 bytes captured (736 bits) on interface -, id 0 Ethernet II, Src: 50:00:00:05:00:01 (50:00:00:05:00:01), Dst: 50:00:00:06:00:01 (50:00:00:06:00:01) Internet Protocol Version 4, Src: 202.100.12.1, Dst: 202.100.12.2 回包用的是单播 User Datagram Protocol, Src Port: 62431, Dst Port: 4789 Virtual eXtensible Local Area Network Flags: 0x0800, VXLAN Network ID (VNI) Group Policy ID: 0 VXLAN Network Identifier (VNI): 6000 Reserved: 0 Ethernet II, Src: 50:00:00:05:00:01 (50:00:00:05:00:01), Dst: NexoComm_00:04:00 (00:50:00:00:04:00) Address Resolution Protocol (reply)
show nve
----------------- ASAv1 -----------------
ASAv1(config)# sh nve
nve 1, source-interface "Outside" is up
IP address 202.100.12.1, subnet mask 255.255.255.0
Encapsulation: vxlan
Encapsulated traffic statistics:
1363 packets input, 133148 bytes
1438 packets output, 191420 bytes
0 packets dropped
Number of configured static peer VTEPs: 0
Number of discovered peer VTEPs: 1
Discovered peer VTEPs:
IP address 202.100.12.2
Default multicast group: 224.0.0.1
Number of VNIs attached to nve 1: 1
VNIs attached:
vni 1: segment-id 6000, mcast-group none
----------------- ASAv2 -----------------
ASAv2(config)# sh nve
nve 1, source-interface "Outside" is up
IP address 202.100.12.2, subnet mask 255.255.255.0
Encapsulation: vxlan
Encapsulated traffic statistics:
15 packets input, 1414 bytes
15 packets output, 1916 bytes
0 packets dropped
Number of configured static peer VTEPs: 0
Number of discovered peer VTEPs: 1
Discovered peer VTEPs:
IP address 202.100.12.1
Number of VNIs attached to nve 1: 1
VNIs attached:
vni 1: segment-id 6000, mcast-group 224.0.0.1
11.2 TrustSec(SXP) 7
TrustSec 根据用户身份,角色信息分配组标签(SGT),标签可以同步到整个网络,网络设备可以根据 SGT 做出转发决策,而不是简单依赖 ACL 。
标签可以手动配置,根据 IP 地址静态配置,也可以使用 ISE 动态下发。
Figure 49: 实验拓扑 【ASAv1 Gi0/3 接口实际上没必要添加,但是不知道为什么以 Gi0/0 为源地址却不能与 ISE 建立 SXP 邻居,同一网段却可以,理论上应该不存在这种限制】
基本网络配置
! -------------------- NTP-Server -------------------- en conf t ip domain-name cisco.com hostname NTP-Server line con 0 exec-timeout 0 0 logging synchronous ! int e0/0 ip add dh no sh int e0/1 ip add 192.168.2.123 255.255.255.0 no sh int e0/2 ip add 65.80.2.123 255.255.255.0 no sh ! clock timezone WST 8 ntp master ! ! -------------------- ASAv1 -------------------- hostname ASAv1 int gi0/0 nameif Outside ip add 202.100.12.1 255.255.255.0 no sh int gi0/1 nameif Inside ip add 65.80.2.10 255.255.255.0 no sh int gi0/2 nameif Mgmt ip add dh no sh int gi0/3 nameif LAN ip add 192.168.2.11 255.255.255.0 no sh ! int gi0/4 nameif DMZ ip add 10.74.68.10 255.255.255.0 no sh ! policy-map global_policy class inspection_default inspect icmp ! username cisco pass Cisco123 pri 15 http server en aaa authentication http console LOCAL http 0 0 Mgmt ntp server 65.80.2.123 source Inside ! route Mgmt 10.79.0.0 255.255.0.0 10.74.113.1 route Outside 192.168.2.1 255.255.255.255 202.100.12.2 route Outside 0 0 202.100.12.2 ! access-list Outside_ACL permit ip any any access-group Outside_ACL in interface Outside ! ! -------------------- ASAv2 -------------------- hostname ASAv2 int gi0/0 nameif Outside ip add 202.100.12.2 255.255.255.0 no sh int gi0/1 nameif Inside ip add 192.168.2.10 255.255.255.0 no sh int gi0/2 nameif Mgmt ip add dh no sh policy-map global_policy class inspection_default inspect icmp ! username cisco pass Cisco123 pri 15 http server en aaa authentication http console LOCAL http 0 0 Mgmt ntp server 192.168.2.123 source Inside ! route Mgmt 10.79.0.0 255.255.0.0 10.74.113.1 route Outside 0 0 202.100.12.1 access-list Outside_ACL permit ip any any access-group Outside_ACL in interface Outside !
设备与ISE 相互认证
Figure 50: 创建网络设备组(ASA_Group)
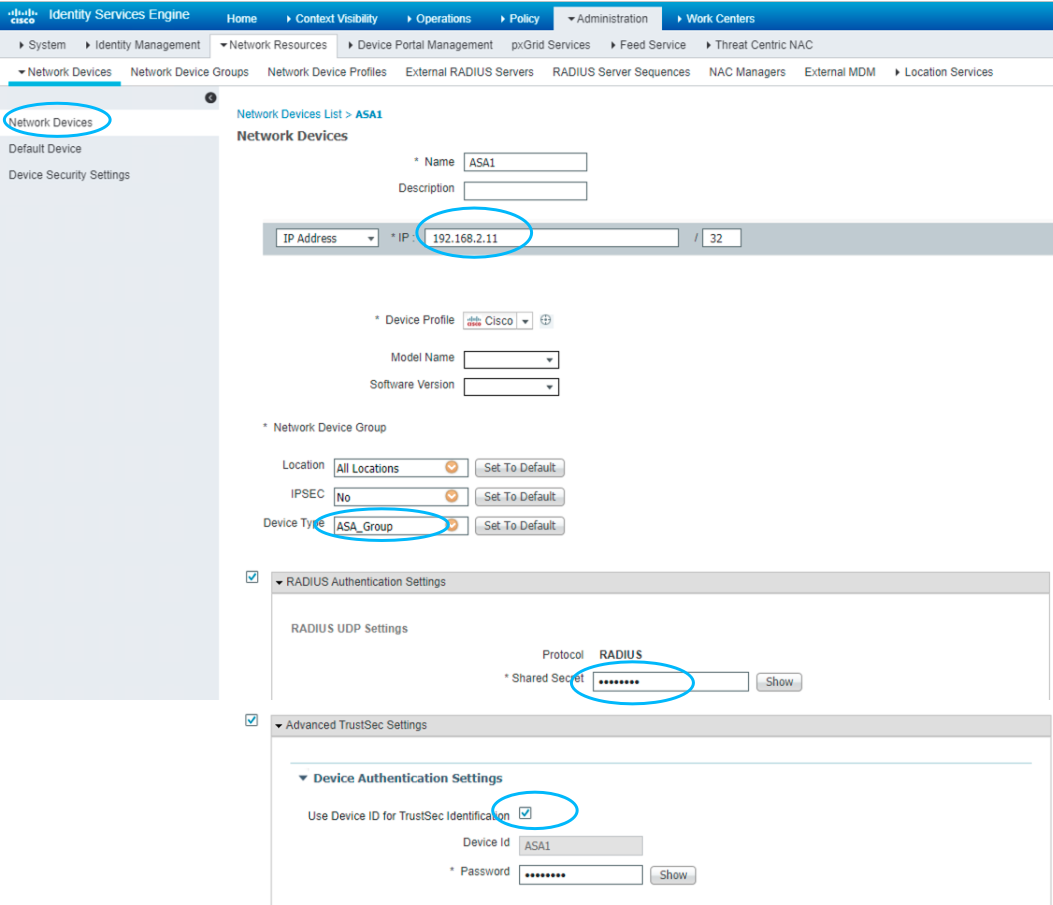
Figure 51: 将两台 ASA 加入 Network Device Group ,以便同时管理
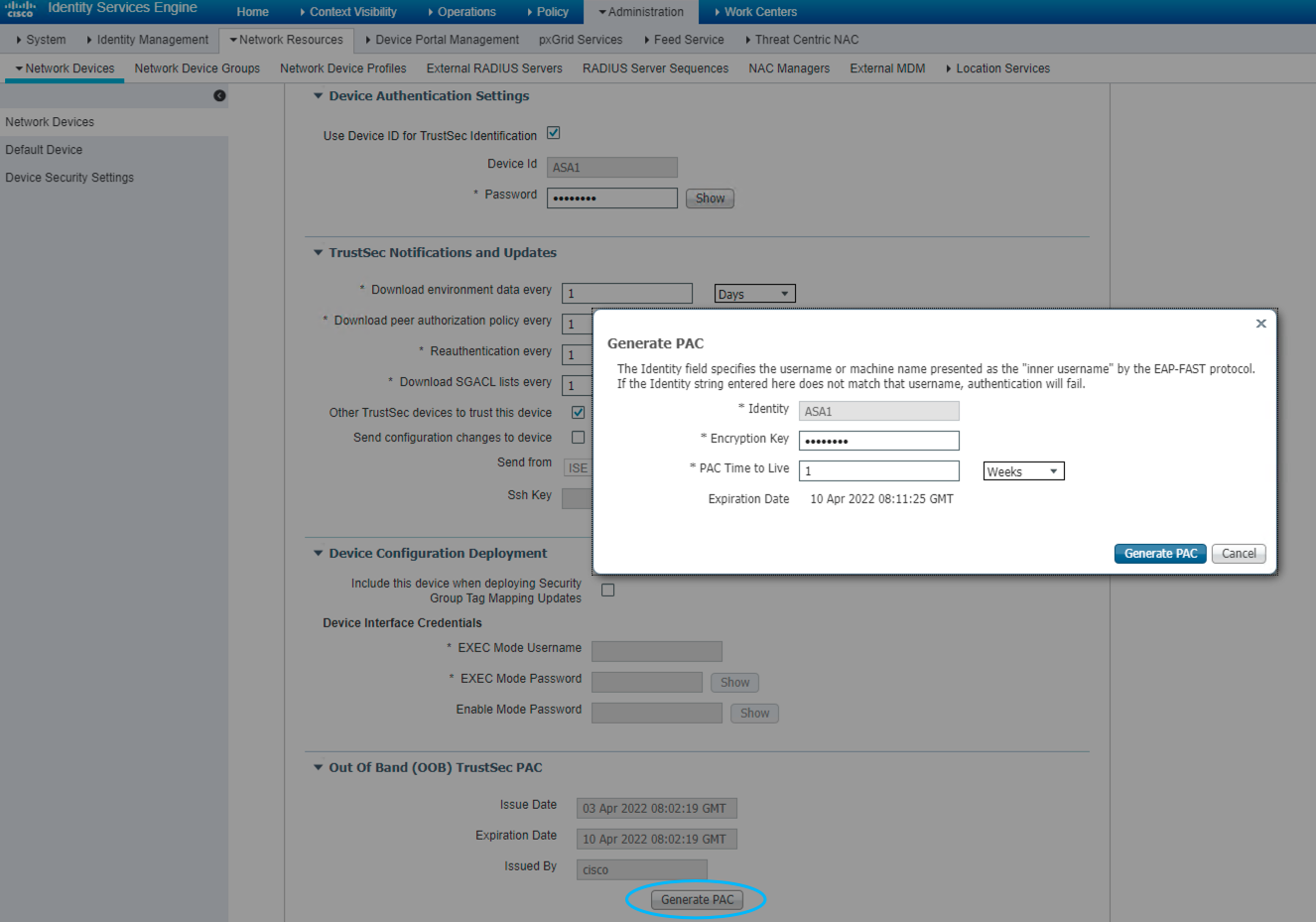
Figure 52: 下载设备 PAC 文件
将两个 PAC 文件上传至对应的 ASA ,导入并指定 ISE 作为 AAA 服务器。
通过认证后,ASA 和 ISE 之间使用 RADIUS 协议进行通信,同时 PAC 以 AVPair 的形式与 TrustSec 服务进行交互。
! ---------------- Load PAC file (ASAv1) ------------------
cts import-pac flash:/ASA1.pac password Cisco123
aaa-server ISE protocol radius
aaa-server ISE (LAN) host 192.168.2.241
key Cisco123
!
! Specify ISE as TrustSec Server
cts server-group ISE
!
cts refresh environment-data
!
! ---------------- Load PAC file (ASAv2) ------------------
cts import-pac flash:/ASA2.pac password Cisco123
aaa-server ISE protocol radius
aaa-server ISE (Inside) host 192.168.2.241
key Cisco123
!
cts server-group ISE
!
cts refresh environment-data
!
查看 Tag
ASAv1(config)# sh cts environment-data CTS Environment Data ==================== Status: Active Last download attempt: Successful Environment Data Lifetime: 86400 secs Last update time: 18:44:08 WST Apr 2 2022 Env-data expires in: 0:21:22:19 (dd:hr:mm:sec) Env-data refreshes in: 0:21:12:19 (dd:hr:mm:sec) ASAv1(config)# sh cts environment-data sg-table Security Group Table: Valid until: 18:44:08 WST Apr 3 2022 Showing 17 of 17 entries SG Name SG Tag Type ------- ------ ------------- ANY 65535 unicast Auditors 9 unicast BYOD 15 unicast Contractors 5 unicast Developers 8 unicast Development_Servers 12 unicast Employees 4 unicast Guests 6 unicast Network_Services 3 unicast PCI_Servers 14 unicast Point_of_Sale_Systems 10 unicast Production_Servers 11 unicast Production_Users 7 unicast Quarantined_Systems 255 unicast Test_Servers 13 unicast TrustSec_Devices 2 unicast Unknown 0 unicast
SXP 相关配置
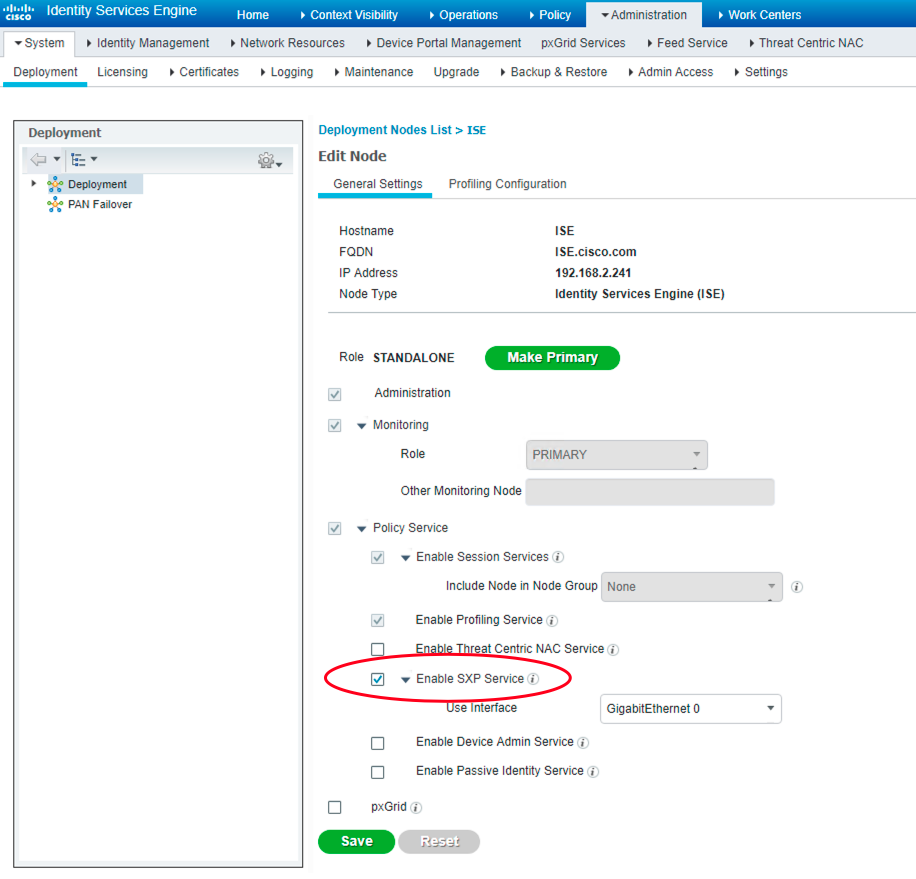
Figure 53: ISE 先要激活 SXP
########## 确保 SXP Service 处于 running 状态 ##########
ISE/cisco# sh app status ise
ISE PROCESS NAME STATE PROCESS ID
--------------------------------------------------------------------
Database Listener running 5084
Database Server running 76 PROCESSES
Application Server running 13422
Profiler Database running 6941
ISE Indexing Engine running 15527
AD Connector running 16615
Certificate Authority Service running 16392
EST Service running 26019
SXP Engine Service running 1036
Docker Daemon running 8314
TC-NAC Service disabled
...
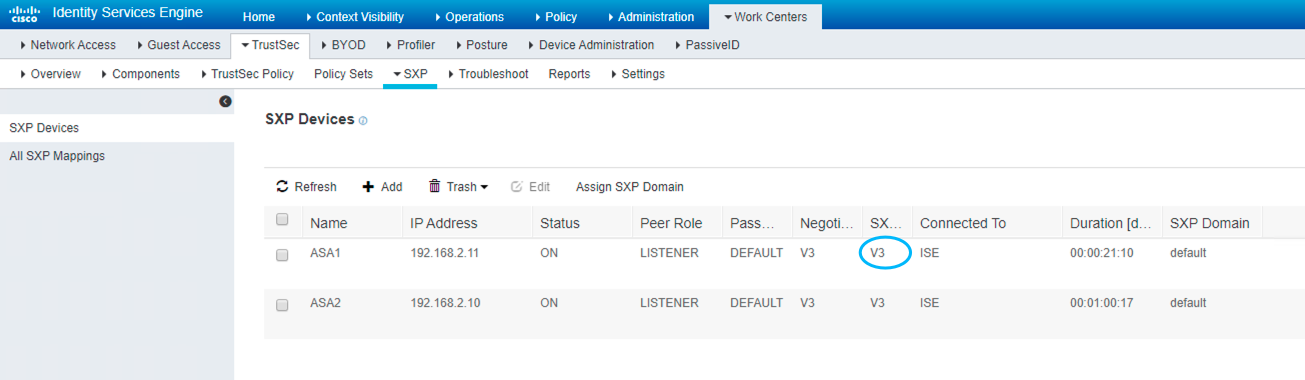
Figure 54: 添加 SXP 设备
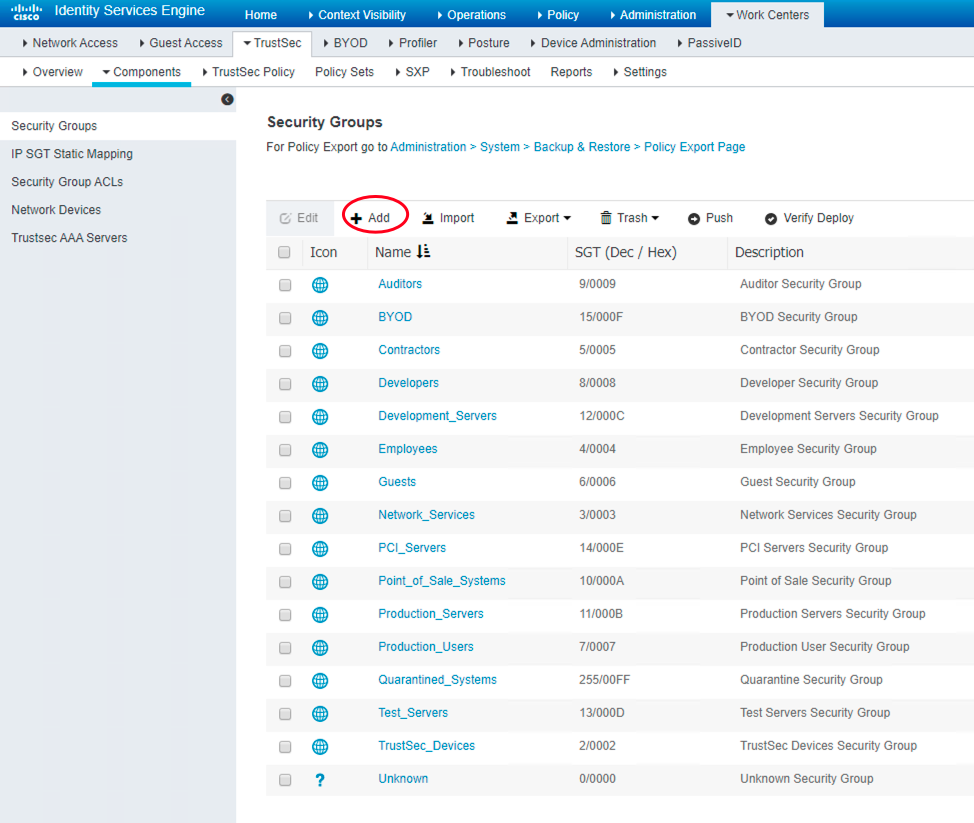
Figure 55: 创建自定义的 TAG
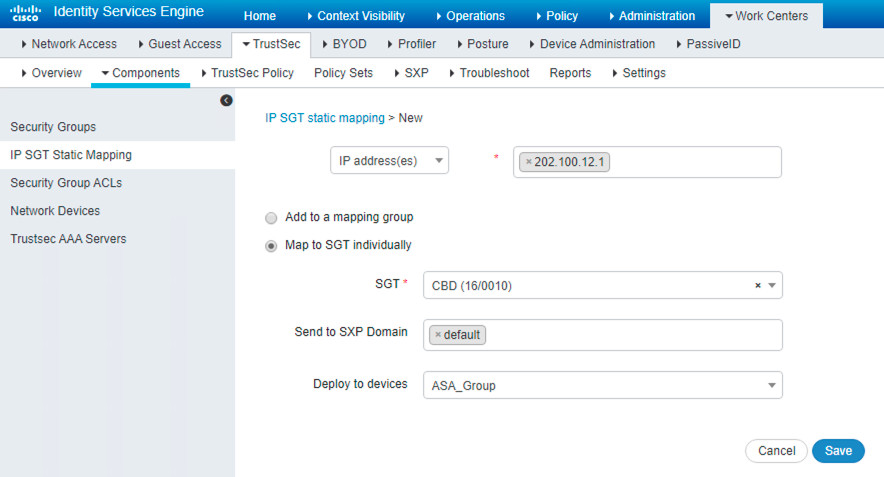
Figure 56: 为 IP 地址静态映射 TAG
! ####################### Configure SXP for ASAv1 ####################### ! Specify password and source ip in a default way cts sxp enable cts sxp default password Cisco123 cts sxp default source-ip 192.168.2.11 cts sxp connection peer 192.168.2.241 password default mode peer speaker ! ! ####################### Configure SXP for ASAv2 ####################### cts sxp enable cts sxp default password Cisco123 cts sxp connection peer 192.168.2.241 source 192.168.2.10 password default mode peer speaker ! ! can use 'sh cts sxp connections' to check info ! can ue 'sh cts sxp sgt-map' to check mapping
####################### 确认静态 SGT 已经同步过来 ####################### ASAv1(config)# sh cts sxp conn b SXP : Enabled Highest version : 3 Default password : Set Default local IP : 192.168.2.11 Reconcile period : 120 secs Retry open period : 120 secs Retry open timer : Not Running Total number of SXP connections: 1 Total number of SXP connections shown: 1 --------------------------------------------------------------------------- Peer IP Local IP Conn Status Duration (dd:hr:mm:sec) --------------------------------------------------------------------------- 192.168.2.241 192.168.2.11 On 0:00:49:31 ASAv1(config)# sh cts sxp sgt-map Total number of IP-SGT mappings : 1 Total number of IP-SGT mappings shown: 1 SGT : 17 此时只是同步了 TAG ,但是 TAG 对应的名称需要运行 cts refresh environment-data 手动同步 IPv4 : 202.100.12.1 Peer IP : 192.168.2.241 Ins Num : 1 Status : Active
! ####################### Configure ACL based on TAG (ASAv2) ####################### object-group security My_Tag_Group ! security-group tag 17 security-group name CBD ! access-list Outside_ACL line 1 deny icmp object-group-security My_Tag_Group any any !
之后,ASAv1 就无法 ping 通 192.168.2.1 了(_ASAv1 发出的数据包不携带 TAG_) 。
但 Linux1 可以 ping 通 Linux2 。
SSLVPN
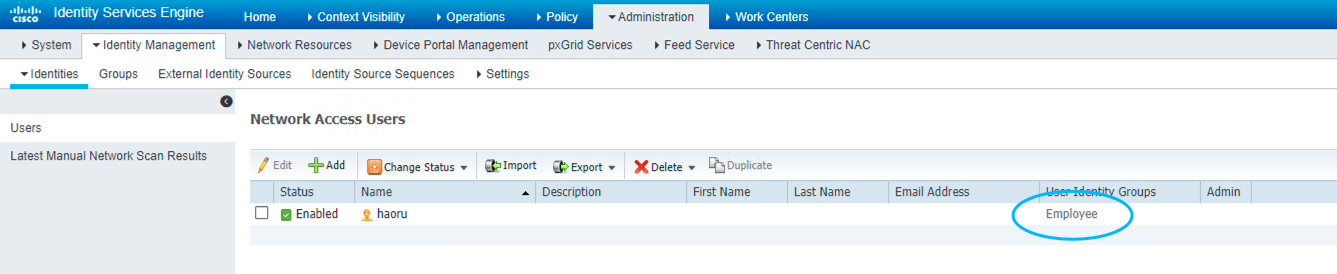
Figure 57: 创建用户
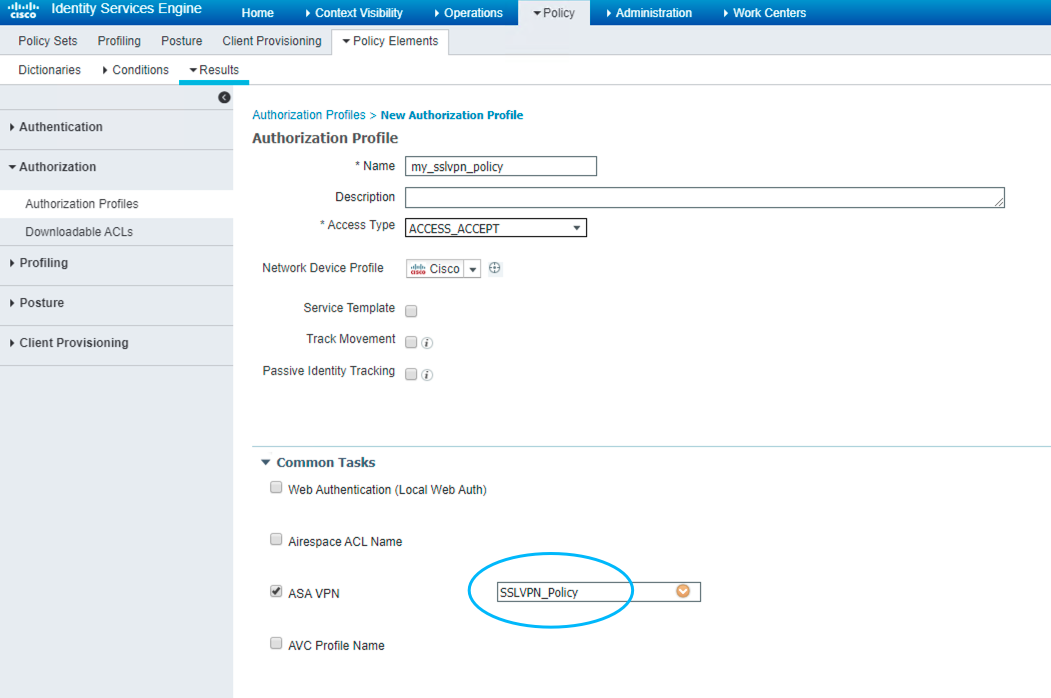
Figure 58: 创建 Authorization Profile
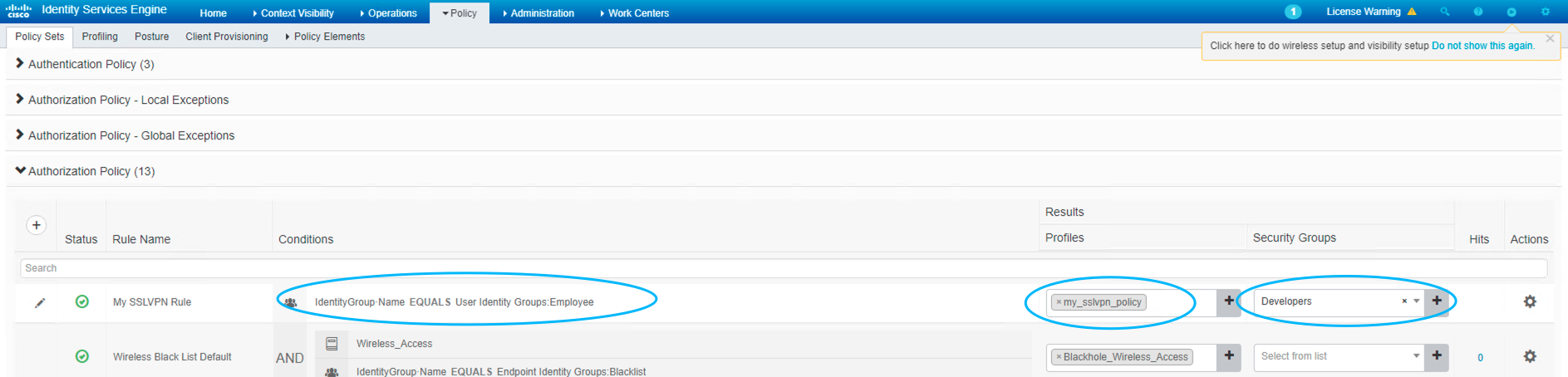
Figure 59: 添加策略
! ####################### SSLVPN Config (ASAv1) ####################### ip local pool SSLVPN-POOL 172.16.1.100-172.16.1.200 ! webvpn enable DMZ anyconnect image disk0:/anyconnect-win-4.4.00243-webdeploy-k9.pkg anyconnect enable ! ! group policy name is used in ISE Authorization Profile group-policy SSLVPN_Policy internal group-policy SSLVPN_Policy attributes vpn-tunnel-protocol ssl-client ssl-clientless address-pools value SSLVPN-POOL ! username cisco attributes vpn-group-policy SSLVPN_Policy ! ! can check all tunnel group via: sh run all tunnel-group tunnel-group DefaultWEBVPNGroup general-attributes authentication-server-group ISE ! int g0/0 ! there will be no tag without this config cts manual ! ! ####################### SSLVPN Config (ASAv2) ####################### int g0/0 cts manual !
! ####################### 查看 vpn session #######################
ASAv1(config-if-cts-manual)# sh vpn-sessiondb anyconnect
Session Type: AnyConnect
Username : haoru Index : 8
Assigned IP : 172.16.1.100 Public IP : 10.74.68.1
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA1
Bytes Tx : 15240 Bytes Rx : 3455
Group Policy : SSLVPN_Policy Tunnel Group : DefaultWEBVPNGroup
Login Time : 11:51:51 UTC Sun Apr 3 2022
Duration : 0h:04m:30s
Inactivity : 0h:00m:00s
VLAN Mapping : N/A VLAN : none
Audt Sess ID : 4150020a0000800062498a57
Security Grp : 8:Developers
! ####################### 数据包 #######################
Frame 9: 82 bytes on wire (656 bits), 82 bytes captured (656 bits) on interface -, id 0
Ethernet II, Src: 50:00:00:0a:00:01 (50:00:00:0a:00:01), Dst: 50:00:00:04:00:01 (50:00:00:04:00:01)
Destination: 50:00:00:04:00:01 (50:00:00:04:00:01)
Source: 50:00:00:0a:00:01 (50:00:00:0a:00:01)
Type: CiscoMetaData (0x8909)
Cisco MetaData
Version: 1
Length: 1
Options: 0x0001
SGT: 8
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 172.16.1.100, Dst: 192.168.2.1
Internet Control Message Protocol