ISE
{Back to Index}
Table of Contents
1 Radius 基本配置与测试
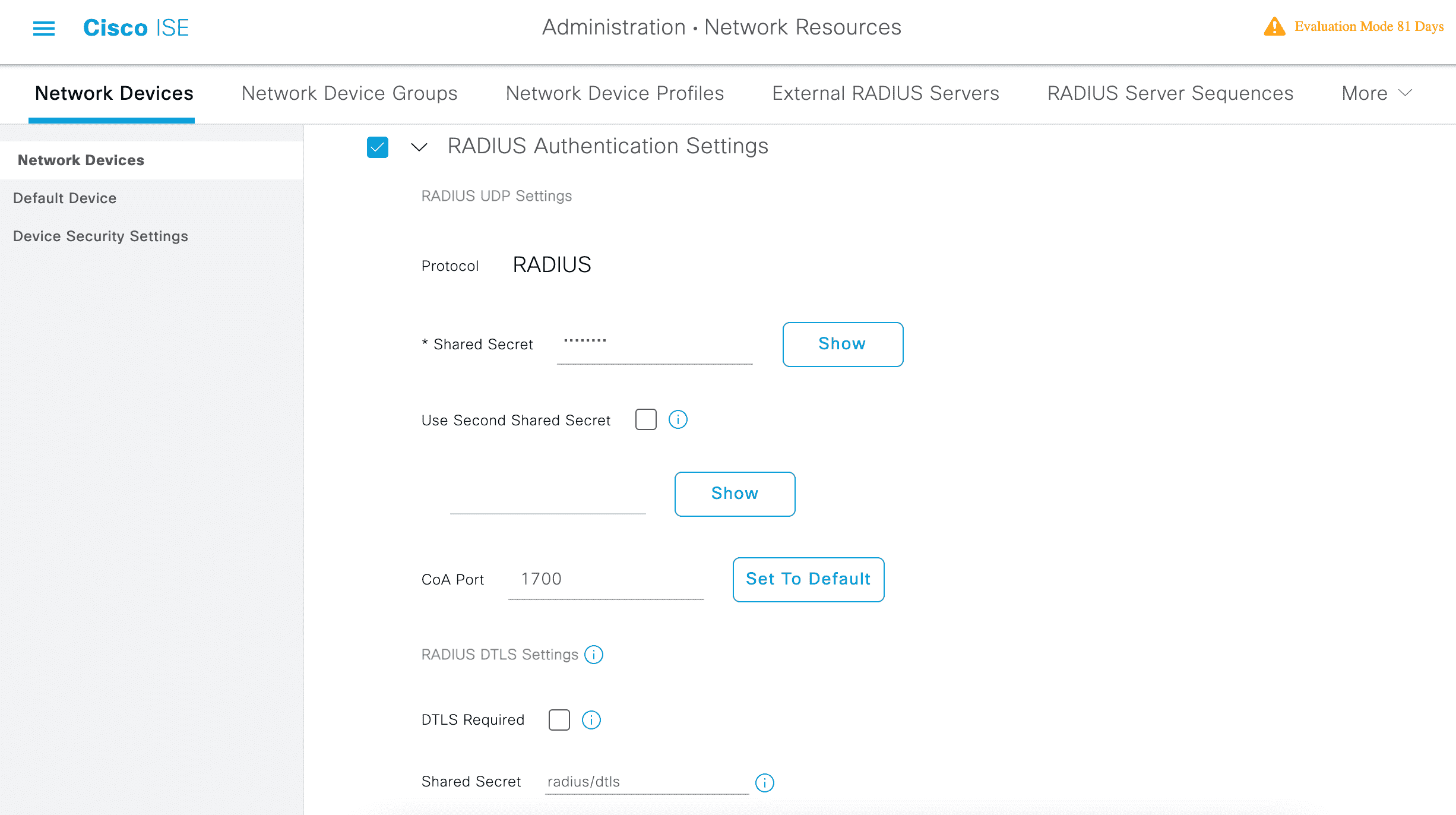
ISE 创建 【Radius 服务】
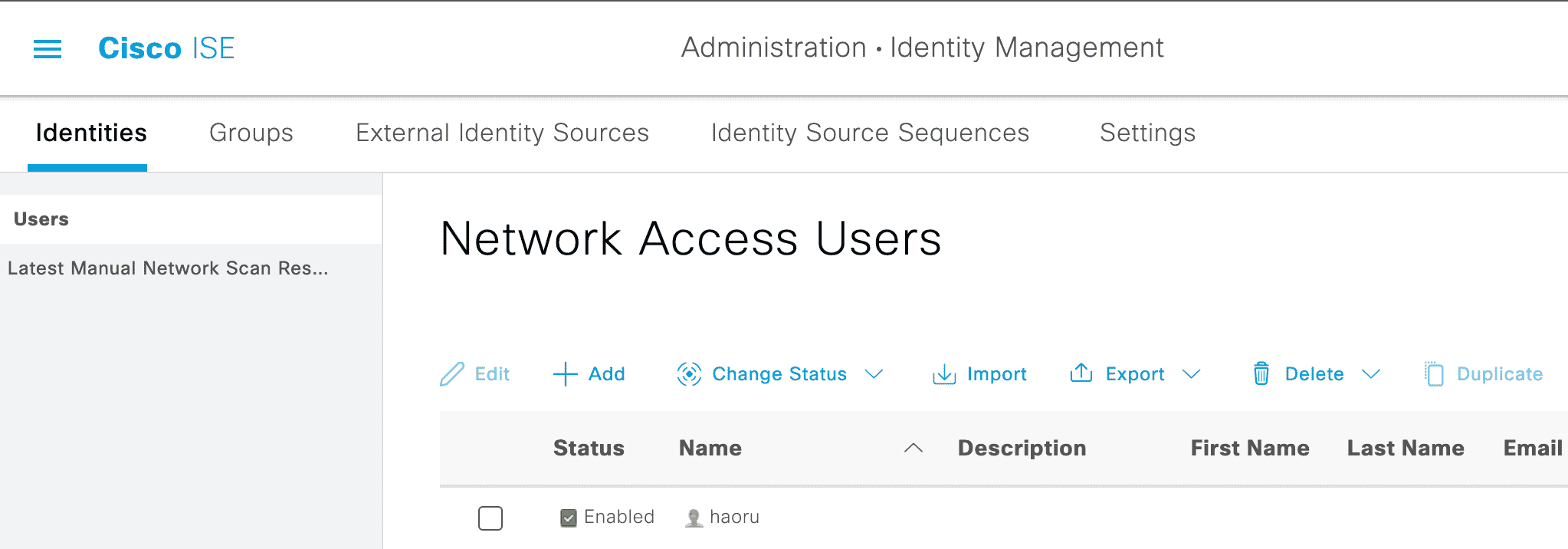
ISE 创建【用户】
2 交换机通用配置
2.1 Radius 配置
基本配置
aaa new-model aaa authentication dot1x default group radius ! enable dot1x, only with this line will sw send req to ISE when it handles dot1x aaa authorization network default group radius ! tell sw to accept the authz profile (attributes related to network) sent from ISE aaa accounting dot1x default start-stop group radius ! enable CoA aaa server radius dynamic-author client 10.74.107.227 server-key 12345678 ! dot1x system-auth-control ! enable dot1x globally ip device tracking ! tracking device IP ! radius-server attribute 6 on-for-login-auth ! send Service-Type attribute in access request radius-server attribute 8 include-in-access-req ! send Framed-IP-Address attribute in access request (optional) radius-server attribute 25 access-request include ! send Class attribute in access request (optional) radius-server dead-criteria time 5 tries 3 ! can try 3 times in 5 minutes radius server MY_RADIUS_SERVER address ipv4 10.74.107.227 key 12345678 ! aaa group server radius MY_RADIUS_SERVER_GROUP server name MY_RADIUS_SERVER ! radius-server vsa send accounting ! enable vendor-specific attributes to be sent in RADIUS accounting message (optional) radius-server vsa send authentication ! must have this to receive dACL which is a cisco specific attribute (aaa:event=acl-download)
2.2 ACL
基本流量 ACL
ip access-list extended ACL-DEFAULT
remark DHCP
permit udp any eq bootpc any eq bootps
remark DNS
permit udp any any eq domain
remark PING
permit icmp any any
remark TFTP
permit udp any any eq tftp
remark DROP all rest
deny ip any any
!
需要重定向的流量
ip access-list extended WEB-REDIRECT deny udp any any eq domain ! dns deny icmp any any deny ip any host 10.74.113.49 ! ISE deny udp any host 10.74.113.49 eq 8905 deny udp any host 10.74.113.49 eq 8906 deny tcp any host 10.74.113.49 eq 8905 deny tcp any host 10.74.113.49 eq 8909 permit ip any any !
2.3 接口配置
dot1x 配置
switchport mode access ! mode must be access, not dynamic authentication port-control auto authentication host-mode multi-auth dot1x pae authenticator ! enable dot1x
通用策略配置(MAB/dot1x/webAuth)
shutdown ! no sh when everything is done description ISE-MAB-DOT1X-WEBAUTH switchport mode access ! mode must be access, not dynamic spanning-tree portfast authentication port-control auto ! enable authentication dot1x pae authenticator ! pc is supplicant, switch is authenticator, ise is authentication server mab authentication open ! often comes with acl as below ip access-group ACL-DEFAULT in authentication host-mode multi-auth authentication violation restrict ! no use when host-mode is multi-auth or multi-host, effective only for multi-domain and single-host authentication order mab dot1x ! mab auth first, dot1x auth second authentication priority dot1x mab ! result of dot1x matters more authentication event fail action next-method ! if mab auth fails, then try dot1x authentication event server dead action authorize vlan 100 ! if authentication server is down, then authorize vlan 100 authentication event fail retry 5 action authorize vlan 200 ! you can guess password 5 times, if fail, then authorize vlan 200 authentication event no-response action authorize vlan 300 ! no reponse from AAA server authentication event server alive action reinitialize ! if authentication server is back to normal, do it again no shutdown
3 MAB
- MAB ,即静态 MAC 认证,使用 MAC 地址作为用户名和密码
- MAB 是一种最基本的认证(因为很多设备并不支持 802.1x)
3.1 有线 MAB 实验
3.1.1 减少实验干扰的设置
关闭Radius黑名单功能
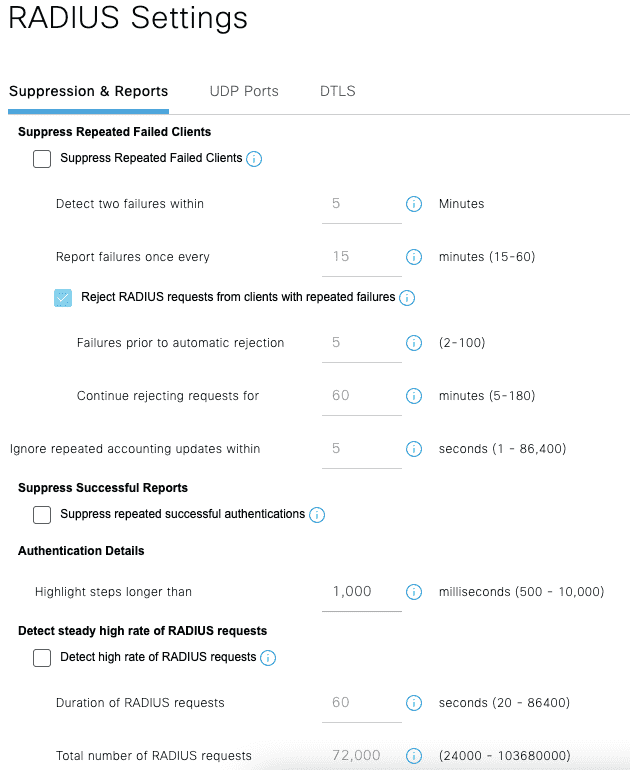
Figure 3: Administration/System/Settings/Protocols/RADIUS
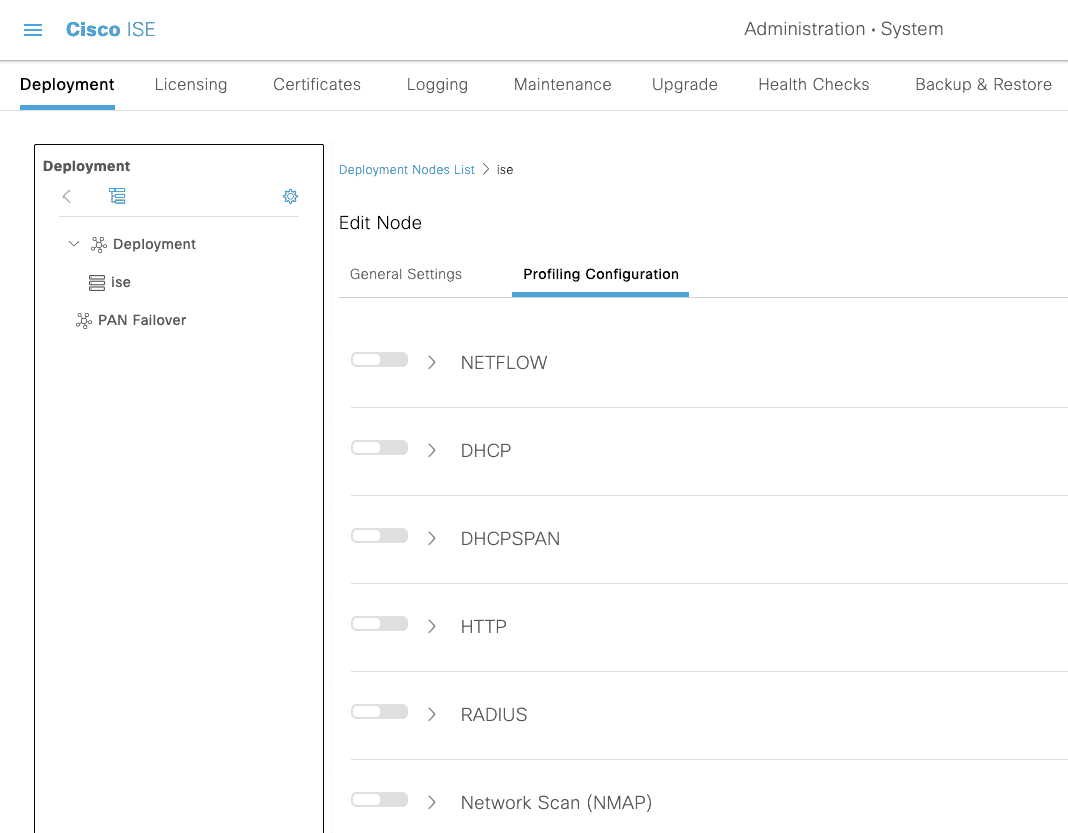
关闭默认的设备识别功能
3.1.2 添加 Endpoint (MAC 地址)
新增 ID Group
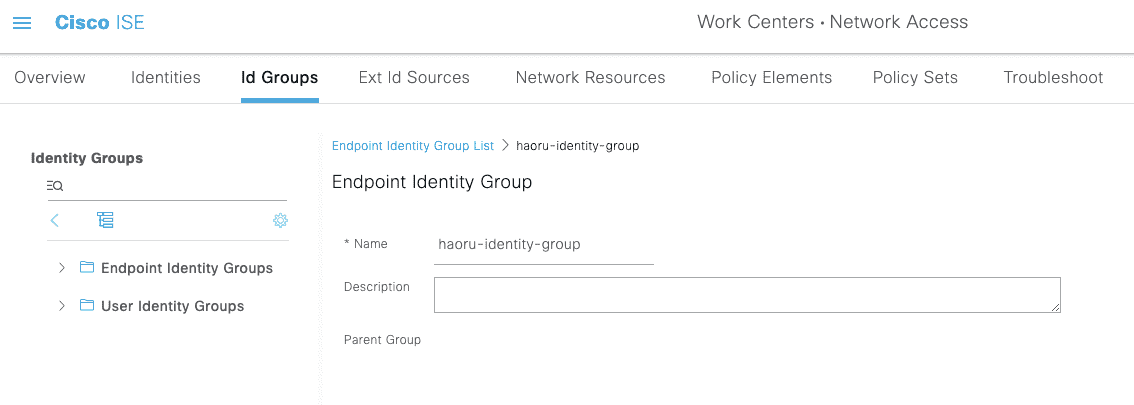
添加 Endpoint
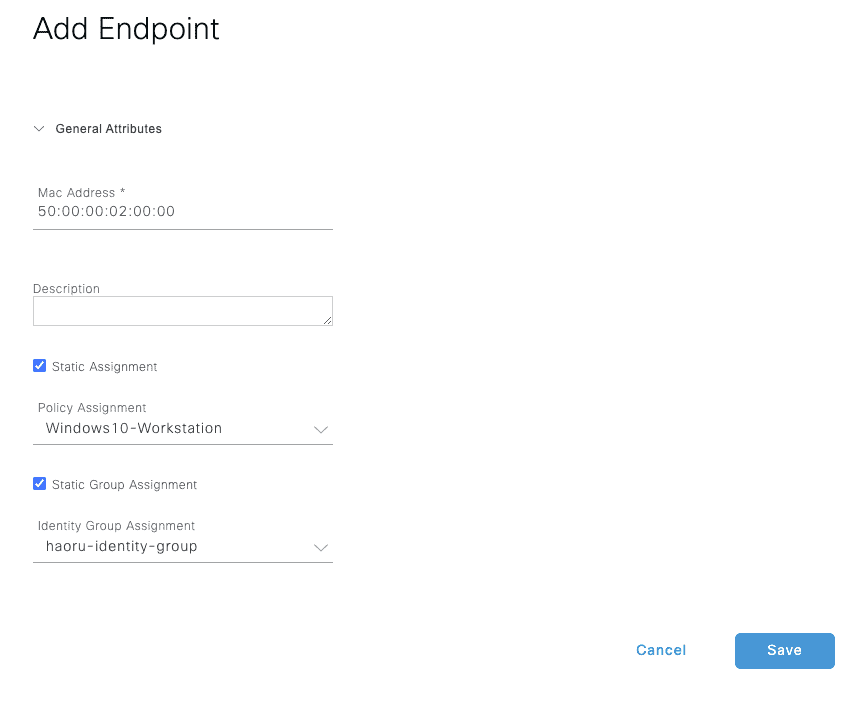
Figure 6: Work Centers/Network Access/Identities
3.1.3 配置授权策略
创建授权 Profile
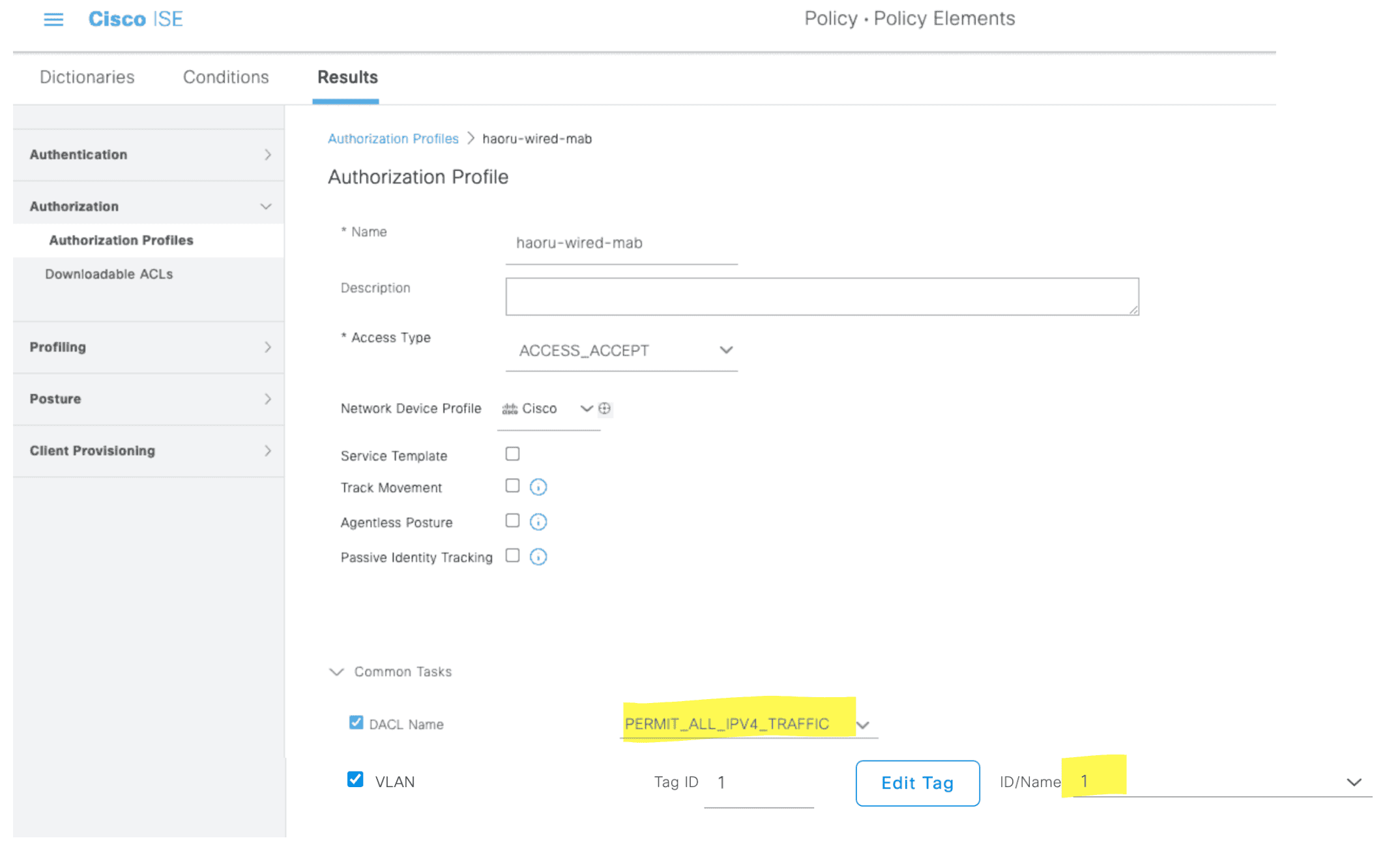
添加授权策略
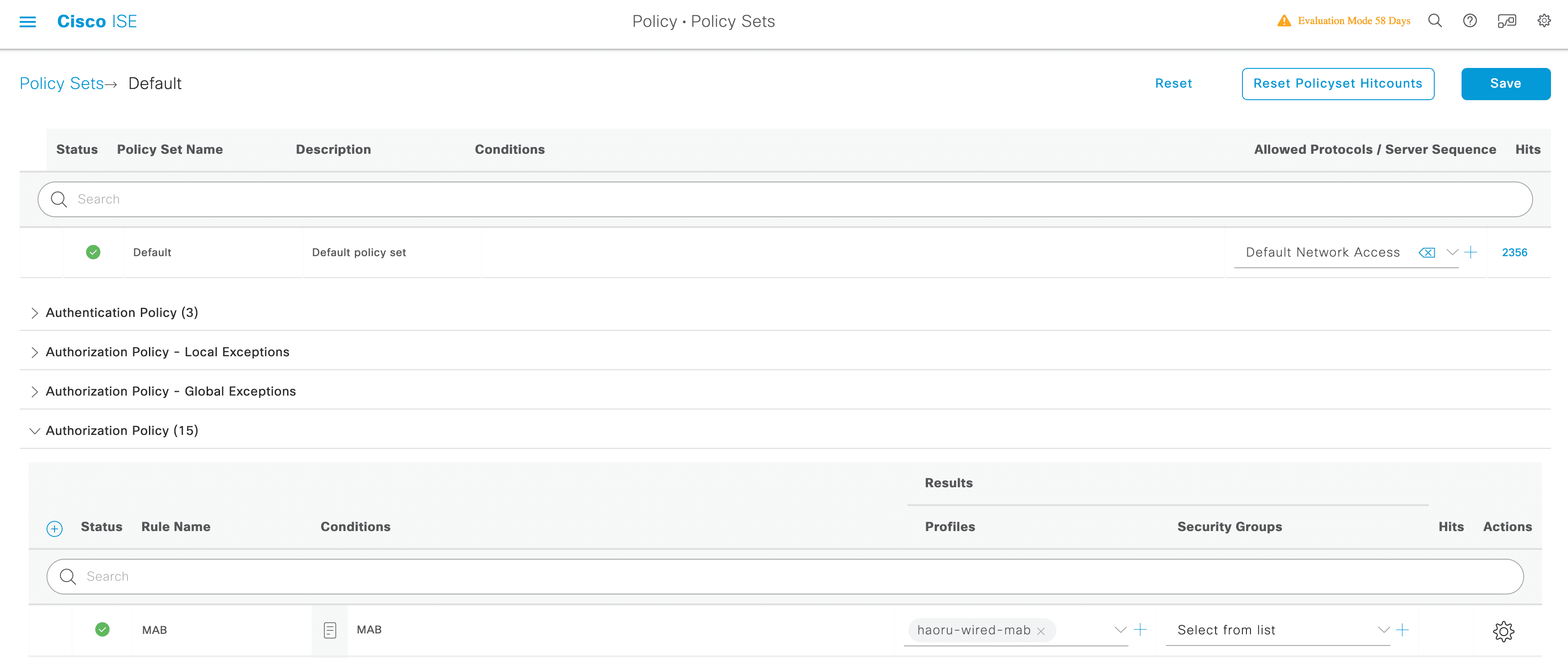
3.1.4 查看接口状态与日志
翻动交换机接口并查看认证信息:
接口信息
SW(config)#do sh authentication sessions int e0/1 details
Interface: Ethernet0/1
MAC Address: 5000.0002.0000
IPv6 Address: Unknown
IPv4 Address: 10.74.113.88
User-Name: 50-00-00-02-00-00
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Periodic Acct timeout: N/A
Session Uptime: 61s
Common Session ID: 0A4A71570000000F01359235
Acct Session ID: 0x00000005
Handle: 0xCF000004
Current Policy: POLICY_Et0/1
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
Vlan Group: Vlan: 1
ACS ACL: xACSACLx-IP-PERMIT_ALL_IPV4_TRAFFIC-57f6b0d3
Method status list:
Method State
mab Authc Success
认证日志
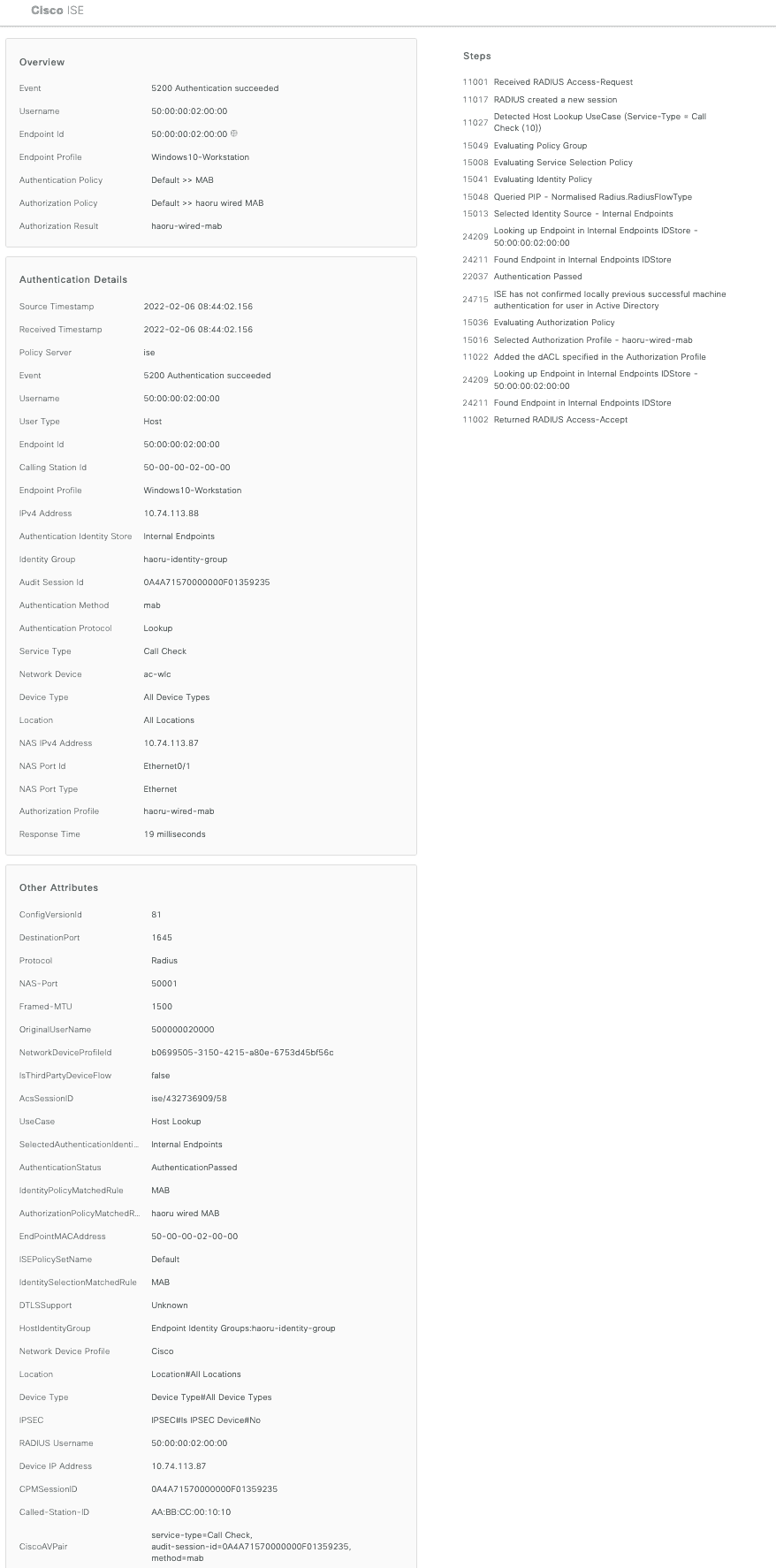
4 802.1x
- 通过认证实现端口物理访问限制
- 封装 EAP 的二层协议,即 EAPOL ,在终端与交换机/AP之间传输认证信息
- 支持端口状态监控,即只要端口 down ,认证信息就会消失
4.1 角色
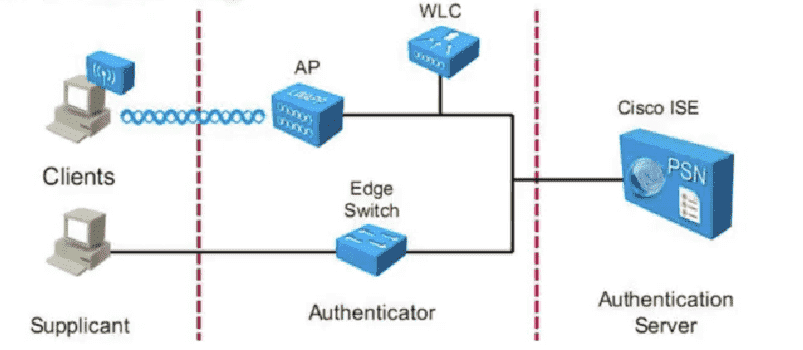
Figure 10: 三种角色(如果AP作为Authenticator则必为胖AP)
4.2 与 EAP 的关系
EAP (Extensible Authentication Protocol) 是用来承载认证信息的协议。常见的保障 EAP 安全性的方式有:
- EAP-MD5 (Deprecated)
- EAP-TLS (复杂,终端和认证服务器都需要证书)
- EAP-FAST [Cisco 私有协议,要求终端(使用anyconnect)和服务器均为Cisco设备]
- PEAP (主流,终端通过证书验证服务器,服务器通过用户名/密码验证终端)
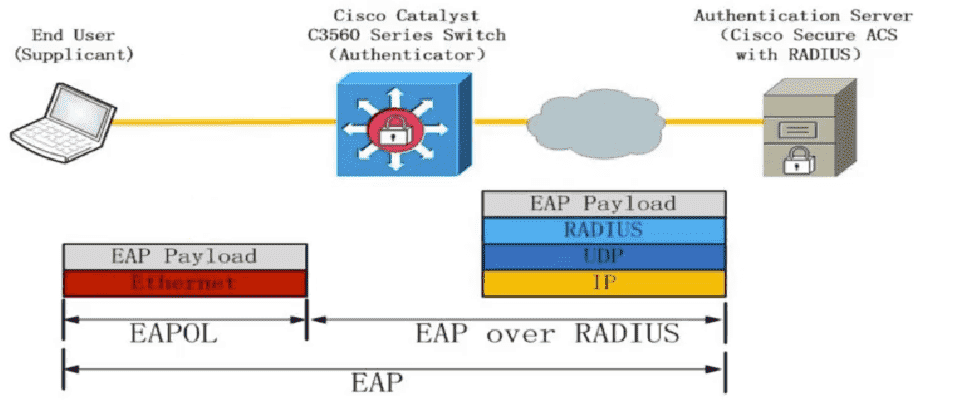
Figure 11: EAP 认证会话发生在终端与认证服务器之间,Authenticator 能感知到这个过程,但主要是作为中继设备
4.3 有线 802.1x 实验 (Windows10/PEAP) 1
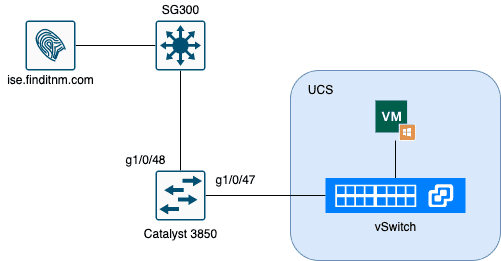
Figure 12: 实验环境
EVE 有个地方需要配置下 ,不然 Window VM 收不到 EAPol 消息。2
! ####################### EVE host ####################### echo 65528 > /sys/class/net/pnet1/bridge/group_fwd_mask echo 65528 > /sys/class/net/pnet2/bridge/group_fwd_mask echo 65528 > /sys/class/net/pnet3/bridge/group_fwd_mask echo 65528 > /sys/class/net/pnet4/bridge/group_fwd_mask echo 65528 > /sys/class/net/pnet5/bridge/group_fwd_mask ...
4.3.1 交换机端口配置
C3850-SW(config-if)#do sh run int g1/0/47
Building configuration...
Current configuration : 615 bytes
!
interface GigabitEthernet1/0/47
description ISE-MAB-DOT1X-WEBAUTH
switchport mode access
! we do not specify vlan id here, vlan will be determined after authorization
ip access-group ACL-DEFAULT in
authentication event fail retry 5 action authorize vlan 200
authentication event server dead action authorize vlan 100
authentication event no-response action authorize vlan 300
authentication event server alive action reinitialize
authentication host-mode multi-auth
authentication open
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
spanning-tree portfast
4.3.2 ISE 配置
和 MAB 实验类似,必须创建 Profile 。 不能使用默认的认证授权,默认的授权虽然是 PermitAccess ,但是该授权没有指定 vlan ,以及 dACL ,即使 Access-Accept ,在 ACL 的控制下,端口仍然不能访问
Authentication Policy
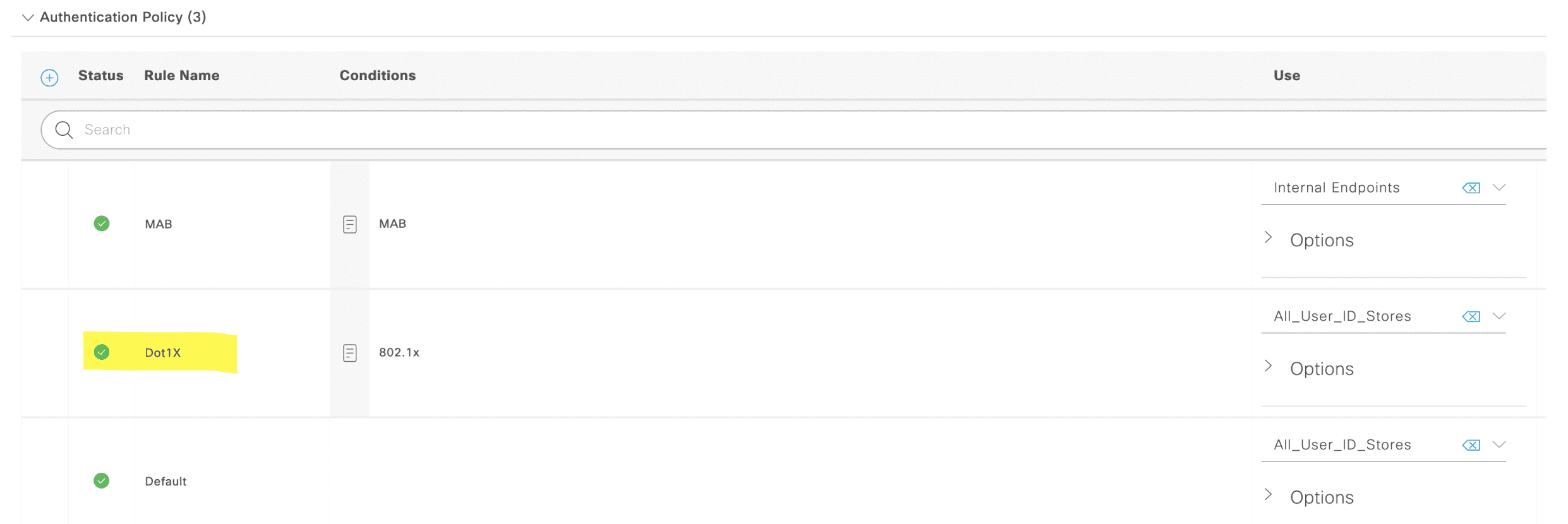
Authorization Policy
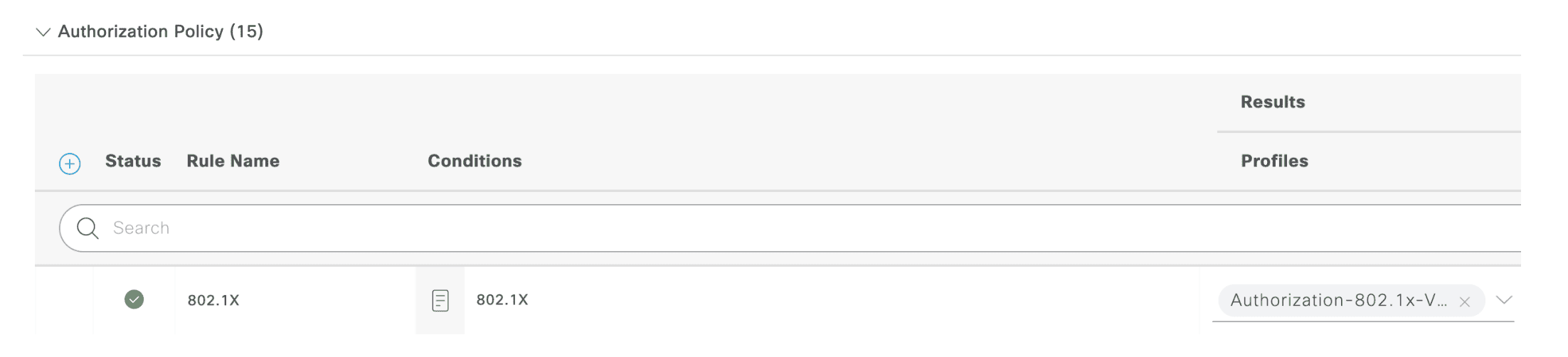
Authorization Profile
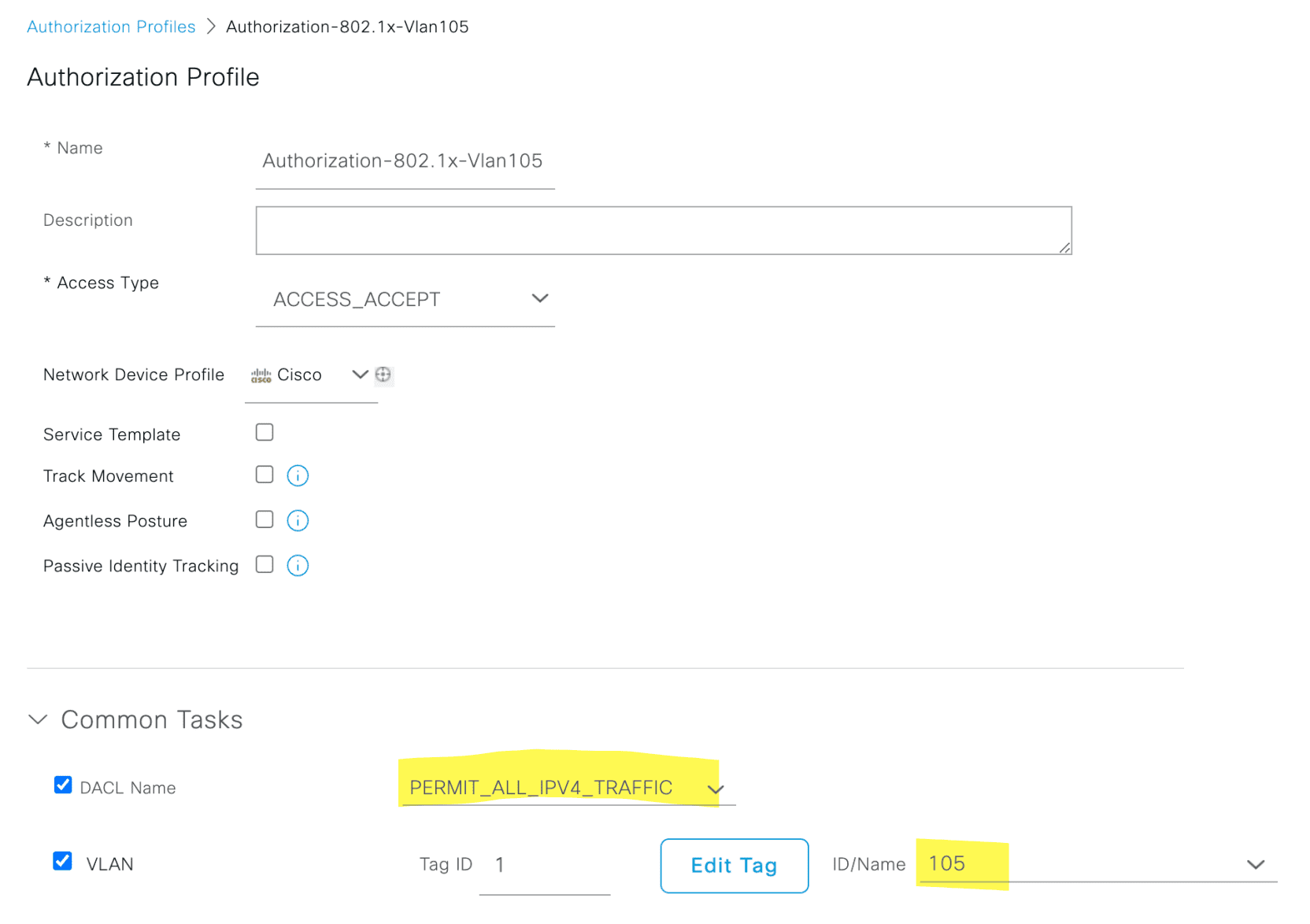
4.3.3 Windows 配置
确认 Wired Autoconfig 服务开启
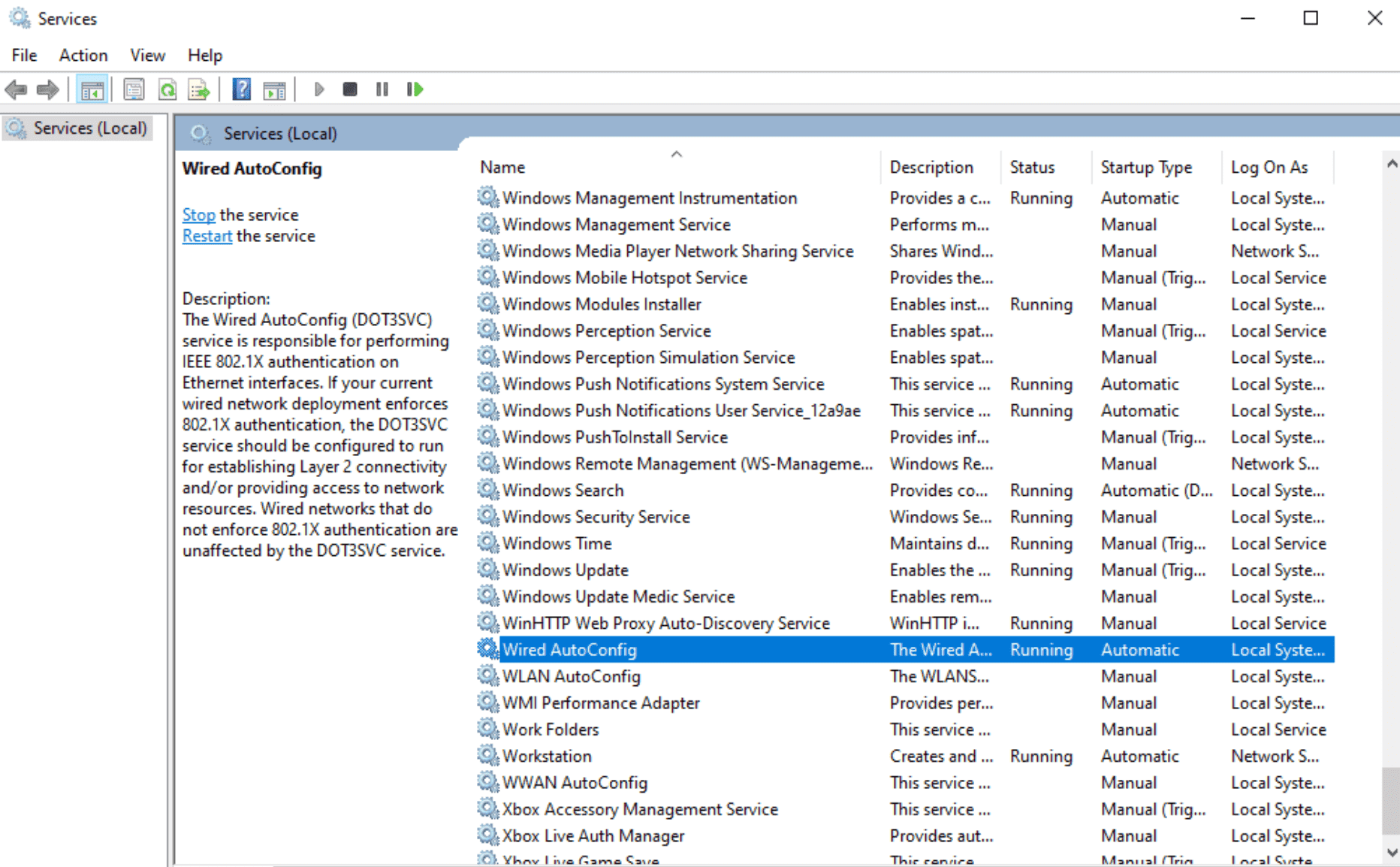
Figure 16: services.msc
网卡设置
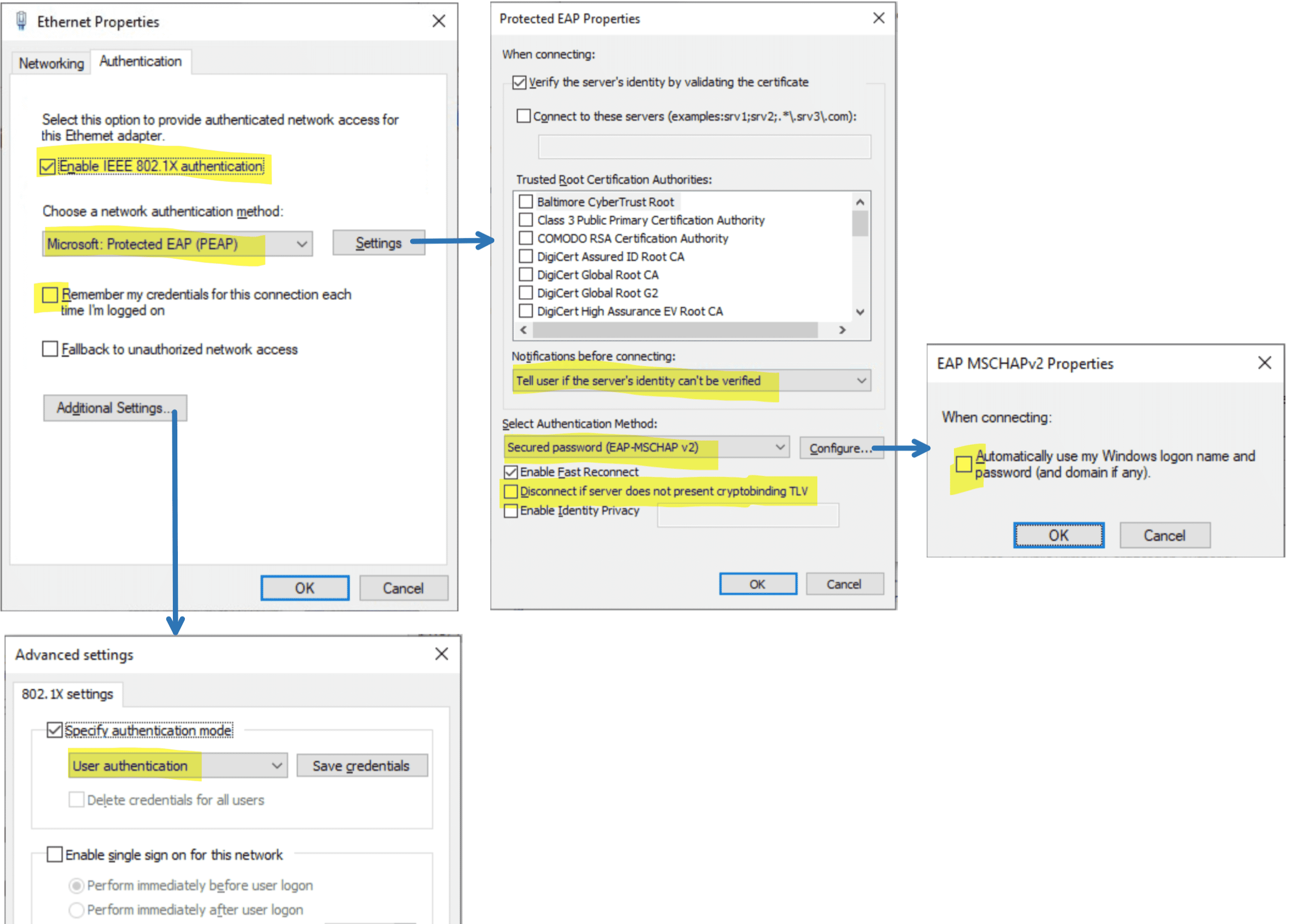
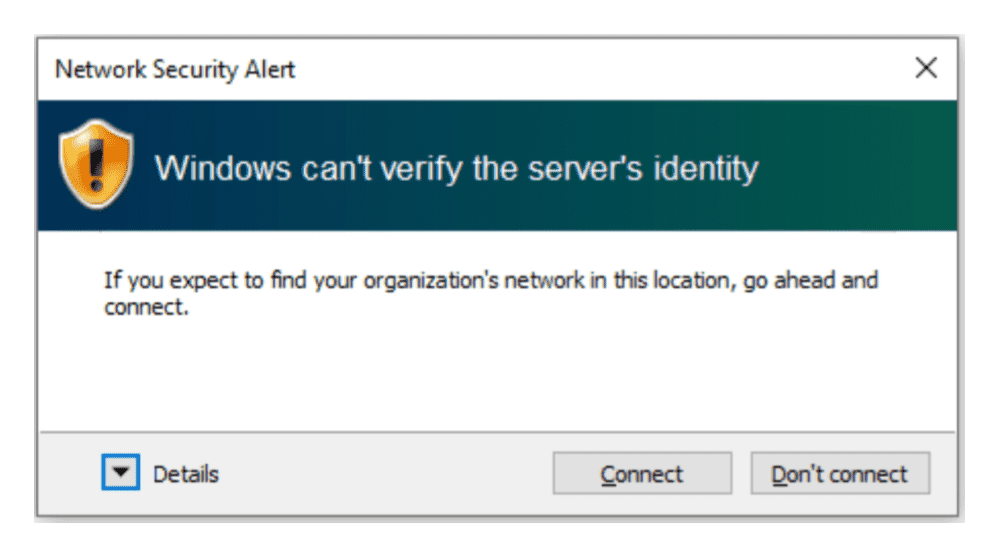
如果配置一切正常,但网卡一直处于 Attempting to authenticate 状态,检查下是否是没注意到弹出的确认 Server Identity 窗口,如下图所示:
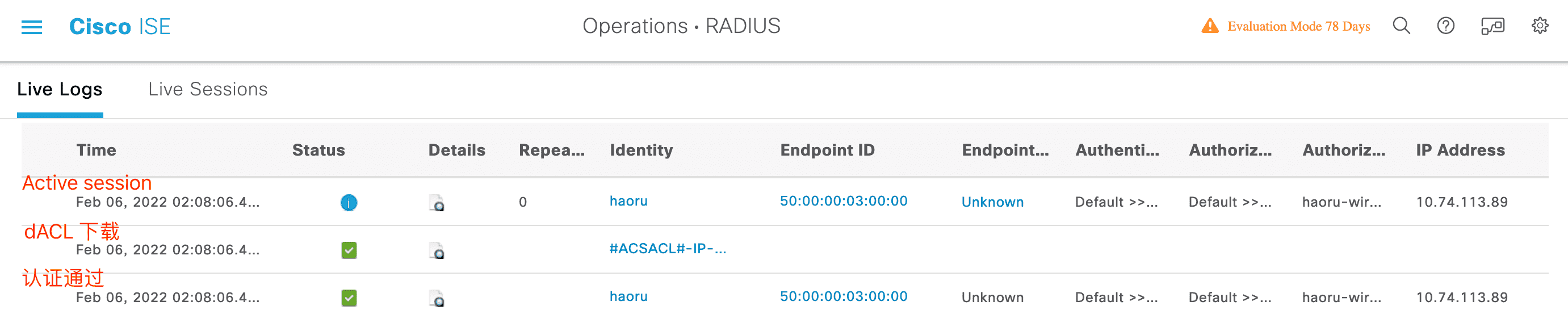
4.3.4 验证
Radius log
show auth session
C3850-SW(config-if)#do sh auth se int g1/0/47 d Interface: GigabitEthernet1/0/47 IIF-ID: 0x105B7C0000000BD MAC Address: 5000.0004.0000 IPv6 Address: Unknown IPv4 Address: 10.74.113.108 User-Name: haoru Status: Authorized Domain: DATA Oper host mode: multi-auth Oper control dir: both Session timeout: N/A Restart timeout: N/A Common Session ID: 0A4A715E00000FD909DB188A Acct Session ID: 0x00000FC0 Handle: 0x8B00002C Current Policy: POLICY_Gi1/0/47 Local Policies: Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150) Security Policy: Should Secure Security Status: Link Unsecure Server Policies: Vlan Group: Vlan: 105 ACS ACL: xACSACLx-IP-PERMIT_ALL_IPV4_TRAFFIC-57f6b0d3 Method status list: Method State mab Stopped dot1x Authc Success C3850-SW(config)#do sh ip device tracking all Global IP Device Tracking for clients = Enabled Global IP Device Tracking Probe Count = 3 Global IP Device Tracking Probe Interval = 30 Global IP Device Tracking Probe Delay Interval = 0 ----------------------------------------------------------------------------------------------- IP Address MAC Address Vlan Interface Probe-Timeout State Source ----------------------------------------------------------------------------------------------- 10.74.113.108 5000.0004.0000 105 GigabitEthernet1/0/47 30 ACTIVE ARP Total number interfaces enabled: 1 Enabled interfaces: Gi1/0/47
5 Web Authentication
- 网页认证通常作为候补认证方式,因为终端不一定运行 802.1x
- 当终端第一次通过有线或无线的方式连到本地网络,会被置于一个访问受限的网络中,可以使用 dACL 定义(授权)这个隔离的网路
- 属于三层认证,二层认证如 802.1x 可以授权 VLAN 和 ACL ,三层认证只能授权 ACL (因为三层认证的时候已经获取到了地址,就算后面授权了新的 VLAN 也无法触发终端重新通过 DHCP 获取新的地址)
5.1 有线中心网页认证实验 3 , 4 , 5
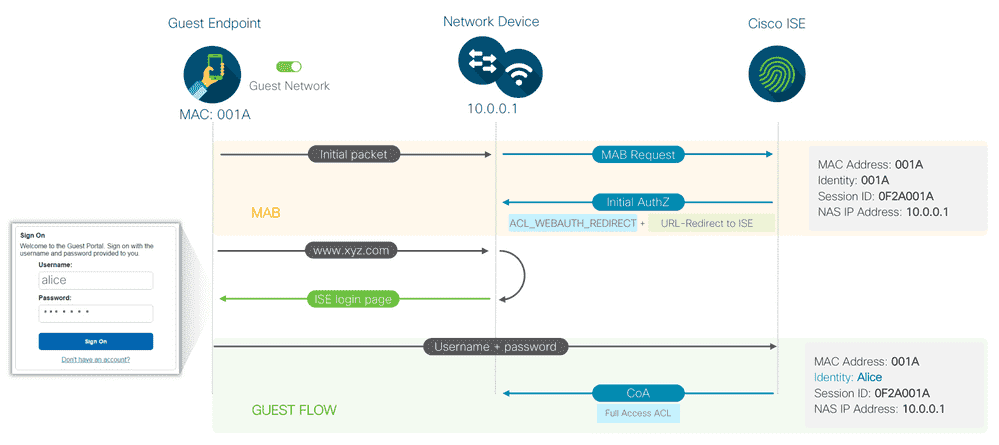
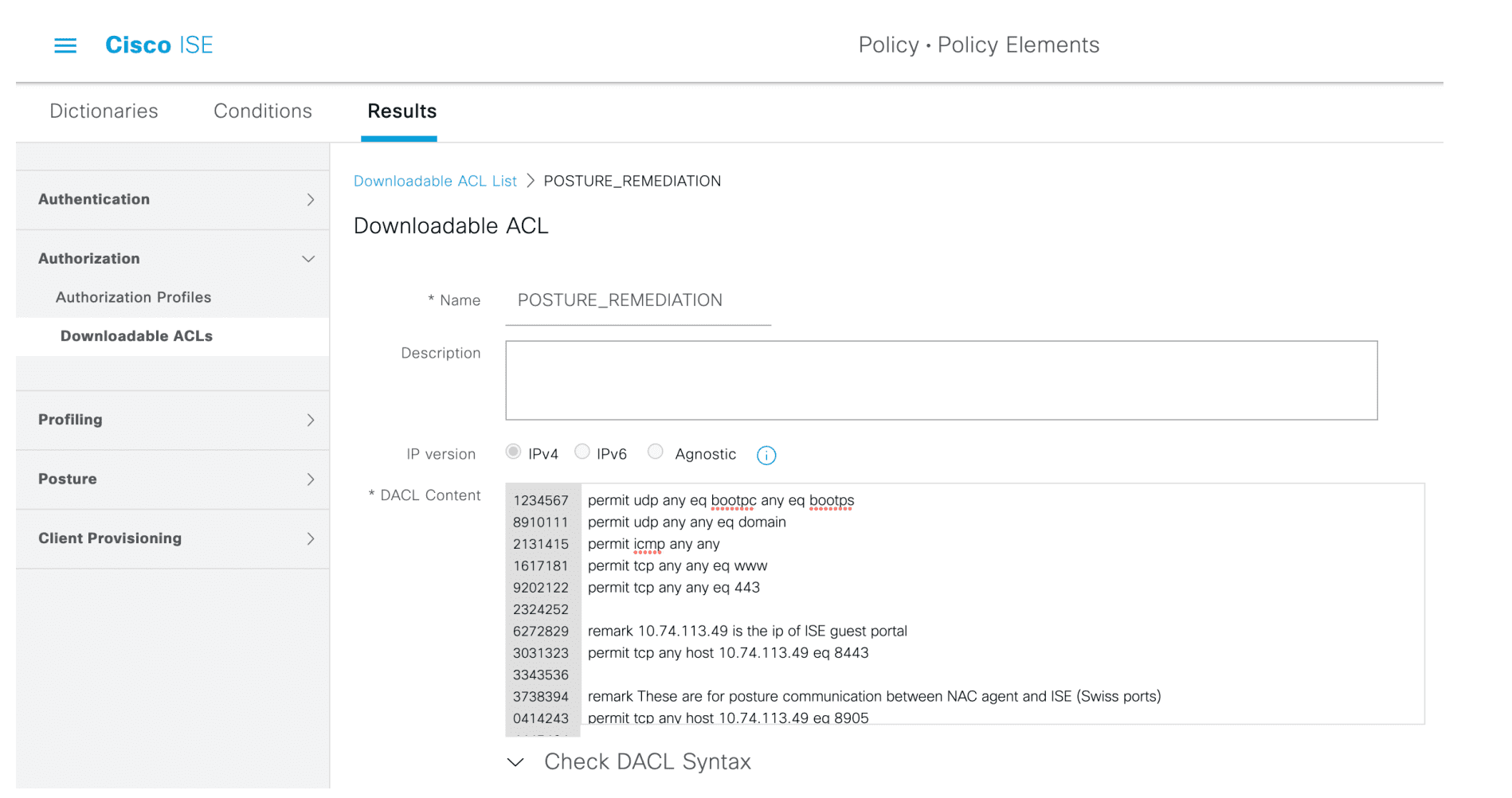
Figure 20: Initial AuthZ 那里还要下放一个 dACL (POSTURE_REMEDIATION)
因为授权是分为 两个阶段 的,所以要在 ISE 上定义两个 Authorization Profile 。
注意,dACL 下载下来后会动态替换掉 pACL (就是最初作用在 port 上的 ACL) ,最终生效的是 dACL 。
该实验模拟器做不出来,能看到 dACL 下发,但是浏览器不能自动跳转,貌似镜像不能匹配需要重定向的流量,建议用 Catalyst 3560 实验。
该实验使用的拓扑与 802.1x 一样。
5.1.1 第一阶段配置
因为 CWA 属于三层认证, 交换机的端口必须正确配置以保证主机可以获得 IP 地址 , 在这个实验中,在端口通用配置的基础上,还将端口划入了 VLAN 105 ,目的是能顺利从 DHCP 获取地址。 而在后续的授权并没有设置 VLAN 信息,这是与 802.1x 认证不同的地方。
dACL 配置
permit udp any eq bootpc any eq bootps permit udp any any eq domain permit icmp any any permit tcp any any eq www permit tcp any any eq 443 remark 10.74.113.49 is the ip of ISE guest portal permit tcp any host 10.74.113.49 eq 8443 remark These are for posture communication between NAC agent and ISE (Swiss ports) permit tcp any host 10.74.113.49 eq 8905 permit udp any host 10.74.113.49 eq 8905 permit udp any host 10.74.113.49 eq 8906 permit tcp any host 10.74.113.49 eq 8906 deny ip any any
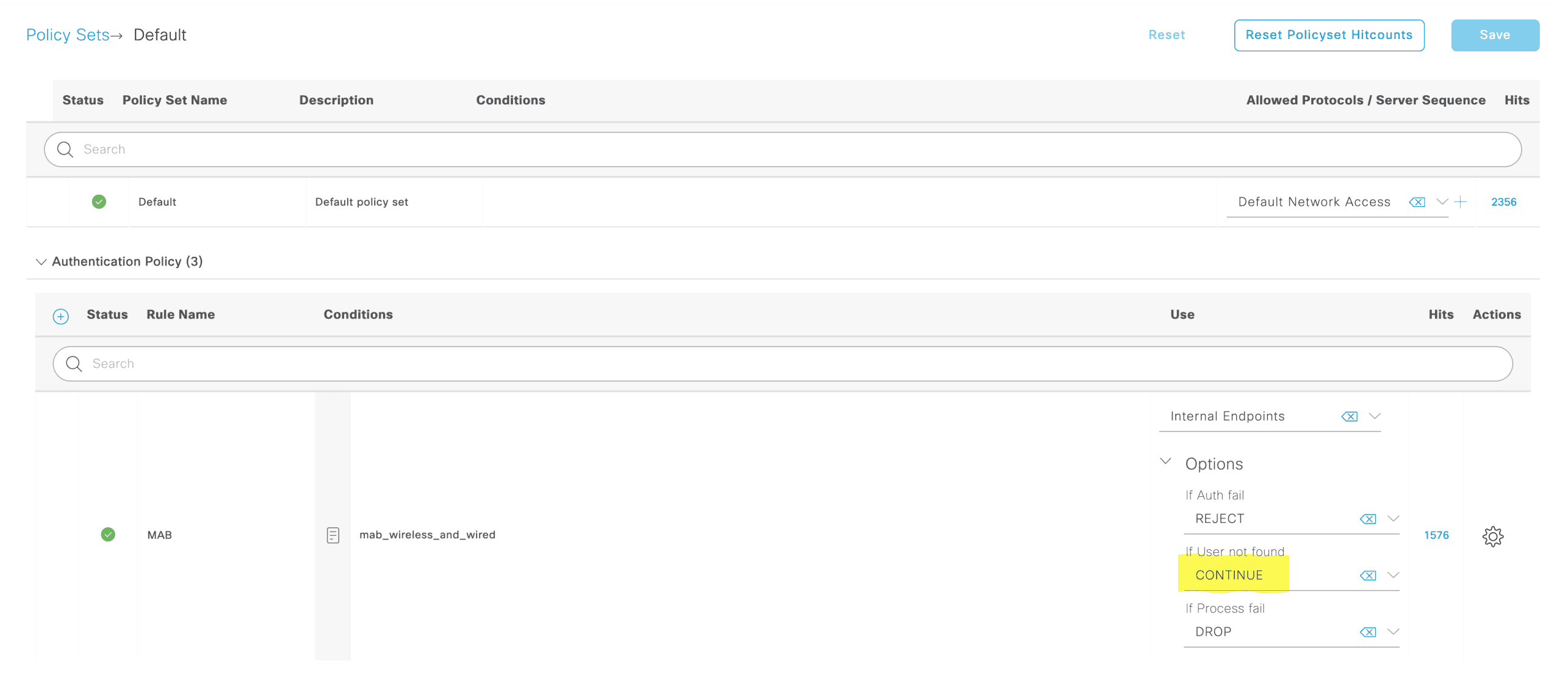
MAB 认证处理(默认行为)
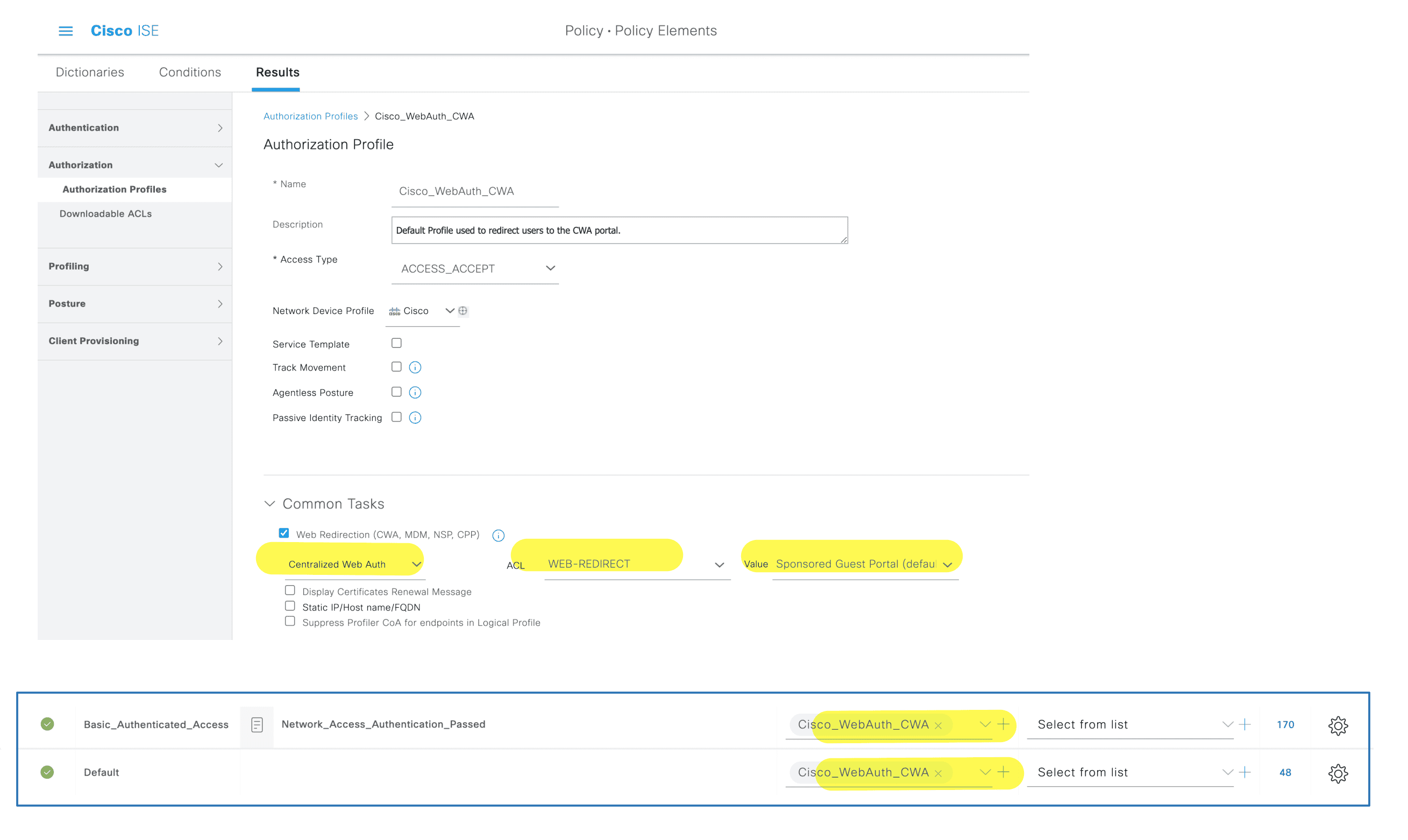
创建 CWA 授权并设为默认授权
5.1.2 第二阶段配置
创建用户组和用户
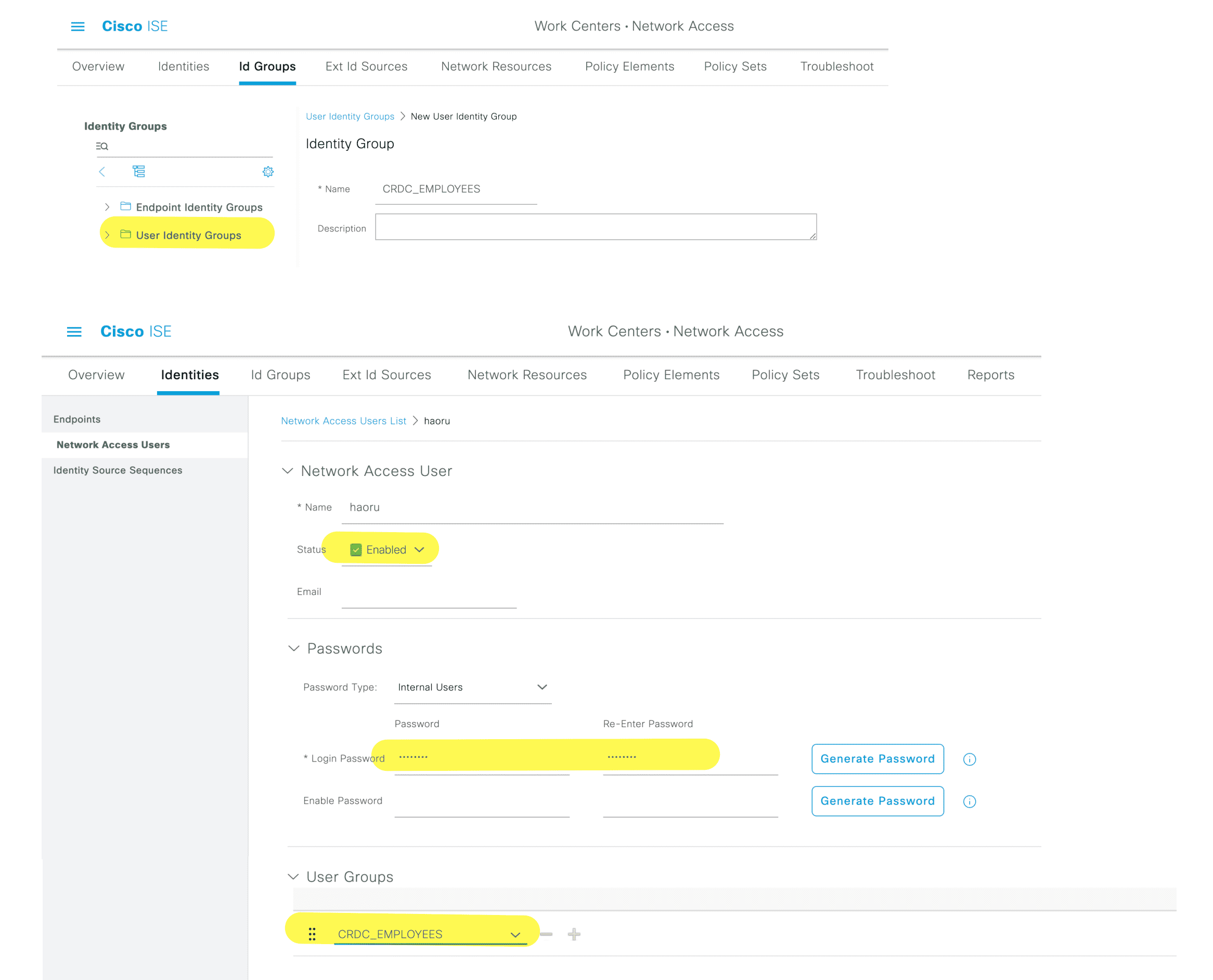
Figure 24: 这么做是为了更好的组织授权
创建针对用户的授权
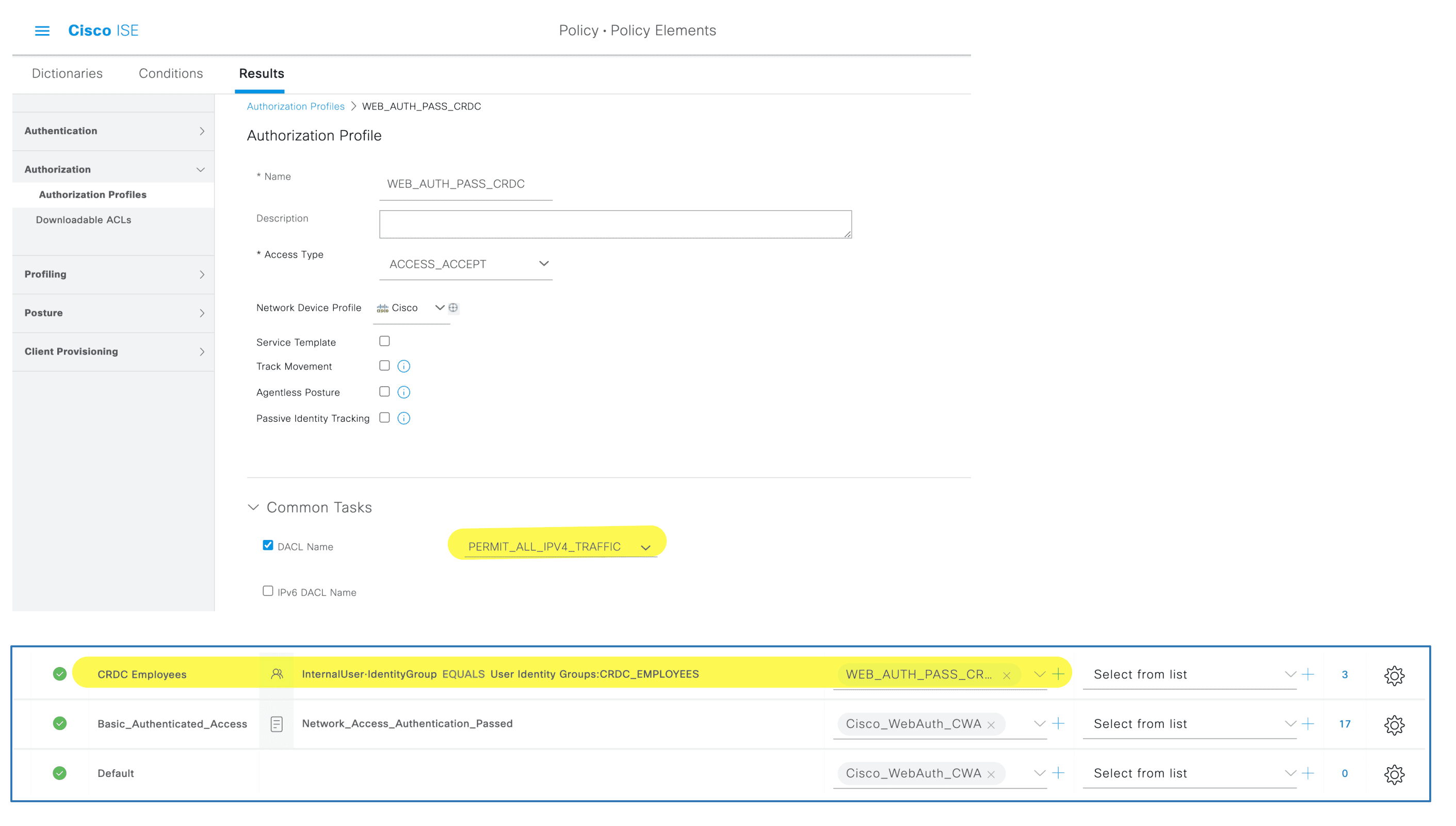
虽然可以在授权中指定 VLAN 信息,但是因为 CWA 是三层认证,配置 VLAN 意义不大,因为用户必须重启网卡。
5.1.3 验证
如果 ISE 使用自签名证书,浏览器基于安全目的可能会限制访问 Portal 6 ,解决的方法是使用 CA 认证的证书, 或者提前让浏览器信任 ISE 证书(比如先在别的电脑上完成认证,让浏览器可以正常访问 Portal 并点击信任证书)。
第一阶段
C3850-SW(config-if)#do sh auth session int g1/0/47 detail
Interface: GigabitEthernet1/0/47
IIF-ID: 0x101EFC000000122
MAC Address: 5000.0002.0000
IPv6 Address: Unknown
IPv4 Address: 10.74.113.110 认证前已经获取了地址
User-Name: 50-00-00-02-00-00
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Common Session ID: 0A4A715E0000103D0F659FD2
Acct Session ID: 0x0000102D
Handle: 0x6100008D
Current Policy: POLICY_Gi1/0/47
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
URL Redirect: https://ise.finditnm.com:8443/portal/gateway?sessionId=0A4A715E0000103D0F659FD2&portal=92cf00d5-7334-4746-b615-6a5d2a7a77ec&action=cwa&token=8ae59f520c438679796ed20d8552cbcd
URL Redirect ACL: WEB-REDIRECT
ACS ACL: xACSACLx-IP-POSTURE_REMEDIATION-621b4e05
Method status list:
Method State
mab Authc Success
第二阶段
C3850-SW(config-if)#do sh auth session int g1/0/47 detail
Interface: GigabitEthernet1/0/47
IIF-ID: 0x101EFC000000122
MAC Address: 5000.0002.0000
IPv6 Address: Unknown
IPv4 Address: 10.74.113.110
User-Name: haoru
Status: Authorized
Domain: DATA
Oper host mode: multi-auth
Oper control dir: both
Session timeout: N/A
Restart timeout: N/A
Common Session ID: 0A4A715E0000103D0F659FD2
Acct Session ID: 0x0000102F
Handle: 0x6100008D
Current Policy: POLICY_Gi1/0/47
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
ACS ACL: xACSACLx-IP-PERMIT_ALL_IPV4_TRAFFIC-57f6b0d3
Method status list:
Method State
mab Authc Success
5.1.4 重定向原理
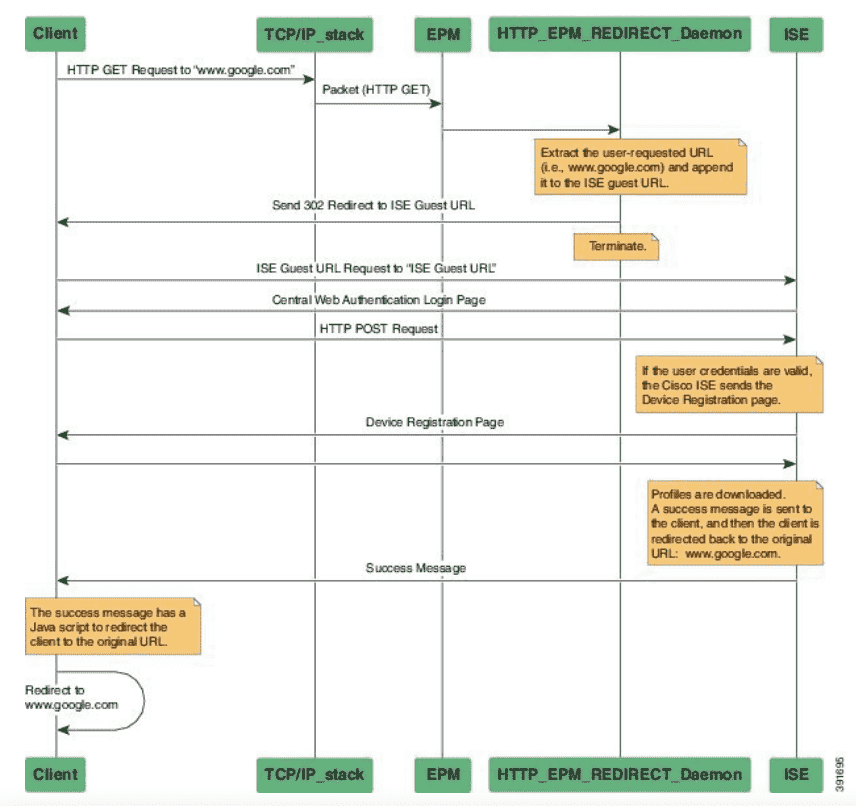
交换机必须要开启 ip http server 和 ip http secure-server ,因为重定向本质在于终端的 http 请求三次握手是与 Switch 的 http server 建立的,因为有 device tracking 机制,所以针对被 tracking 的终端的 http 请求,会返回 302 消息。